A single-packet traceability method based on the importance assessment of trace traces
An important and traceable technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve the problems of reducing traceability storage costs, reducing traceability accuracy, and severe traceability storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
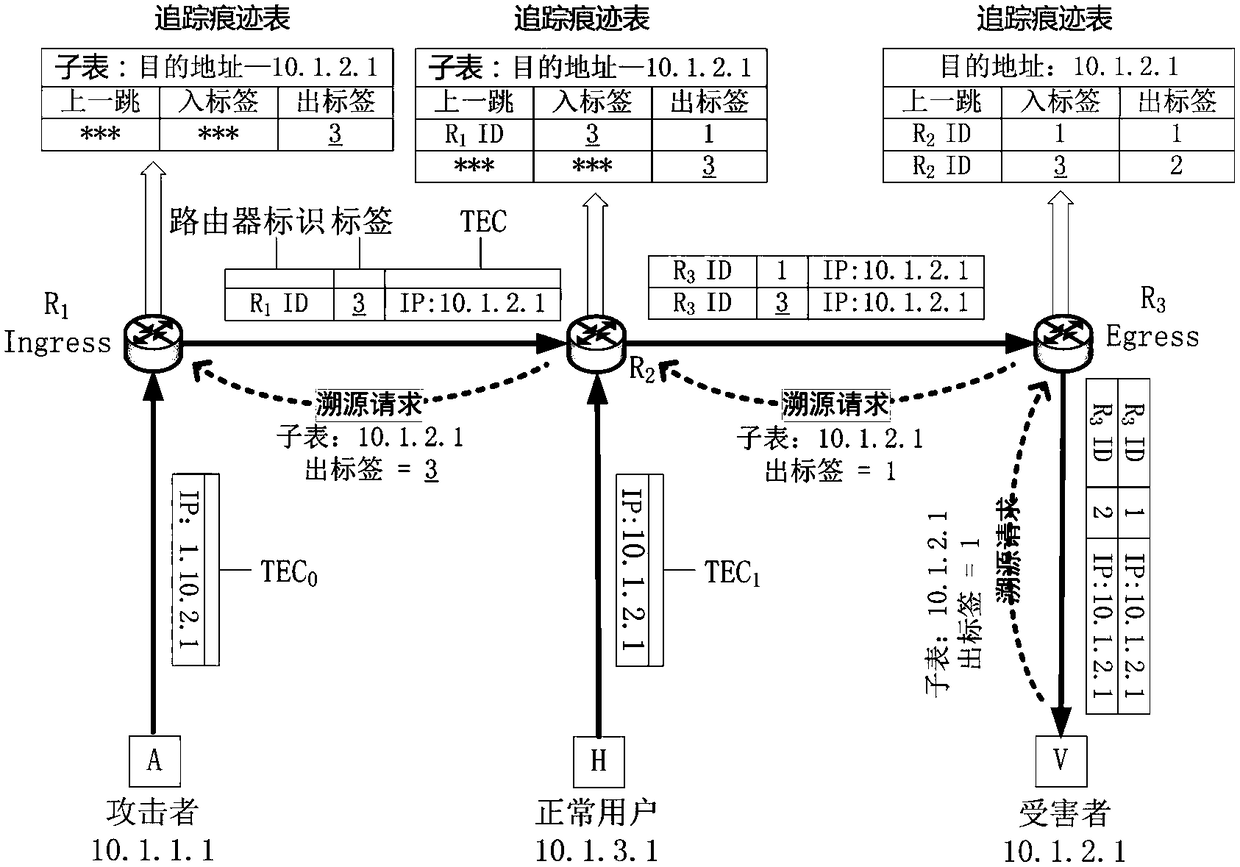
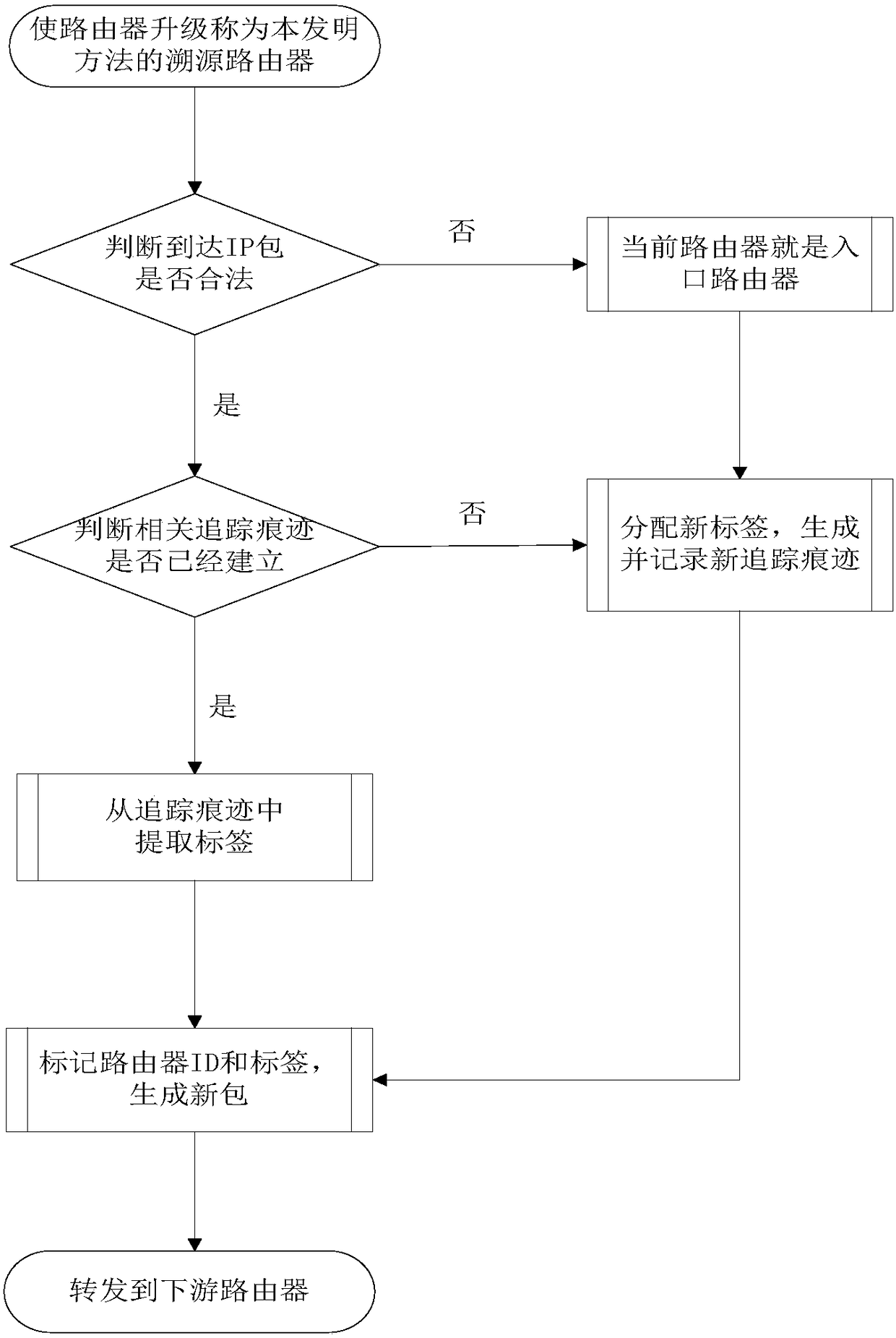
[0063] Embodiment 1 of the present invention: a single-package traceability method based on the importance assessment of trace traces, such as Figure 1 ~ Figure 3 shown, including the following steps:
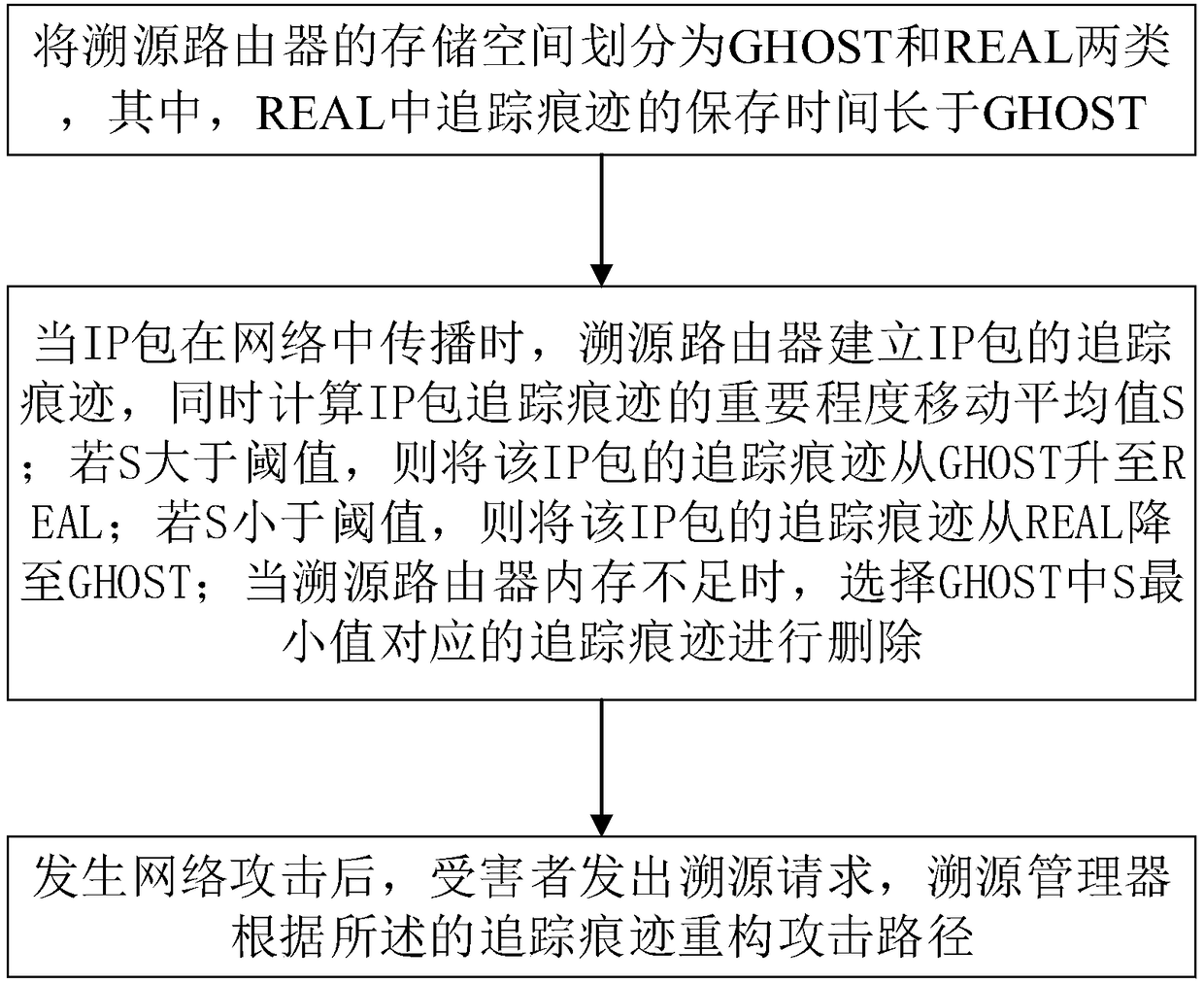
[0064] S1. Divide the storage space of the traceability router into two types: GHOST and REAL. Among them, the storage time of tracking traces in REAL is longer than that in GHOST;
[0065] S2. When the IP packet propagates in the network, the traceability router establishes the tracking trace of the IP packet, and at the same time calculates the moving average prediction value S of the importance of the trace trace corresponding to the IP packet; if S is greater than the threshold value, the tracking trace of the IP packet The trace is raised from GHOST to REAL; if S is less than the threshold, the trace of the IP packet will be lowered from REAL to GHOST; when the memory of the traceability router is insufficient, select the trace corresponding to the minimum value of S in G...
Embodiment 2
[0089] Embodiment 2: A single package traceability method based on the importance assessment of trace traces, comprising the following steps:
[0090] S1. Divide the storage space of the traceability router into two types: GHOST and REAL. Among them, the storage time of tracking traces in REAL is longer than that in GHOST;
[0091]S2. When the IP packet propagates in the network, the traceability router establishes the tracking trace of the IP packet, and at the same time calculates the moving average prediction value S of the importance of the trace trace corresponding to the IP packet; if S is greater than the threshold value, the tracking trace of the IP packet The trace is raised from GHOST to REAL; if S is less than the threshold, the trace of the IP packet will be lowered from REAL to GHOST; when the memory of the traceability router is insufficient, select the trace corresponding to the minimum value of S in GHOST to delete;
[0092] S3. After a network attack occurs, t...
Embodiment 3
[0097] Embodiment 3: a single package traceability method based on the evaluation of the importance of trace traces, comprising the following steps:
[0098] S1. Divide the storage space of the traceability router into two types: GHOST and REAL. Among them, the storage time of tracking traces in REAL is longer than that in GHOST;
[0099] S2. When the IP packet propagates in the network, the traceability router establishes the tracking trace of the IP packet, and at the same time calculates the moving average prediction value S of the importance of the trace trace corresponding to the IP packet; if S is greater than the threshold value, the tracking trace of the IP packet The trace is raised from GHOST to REAL; if S is less than the threshold, the trace of the IP packet will be lowered from REAL to GHOST; when the source tracing router has insufficient memory, select the trace corresponding to the minimum value of S in GHOST to delete; The router uses an irregular pipeline to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com