A sensitive data identification method and device
A sensitive data and identification method technology, which is applied in the field of information security, can solve the problems of time-consuming and labor-intensive detection of sensitive data, and achieve the effect of efficiently and automatically identifying sensitive data and reducing the probability of missing sensitive data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
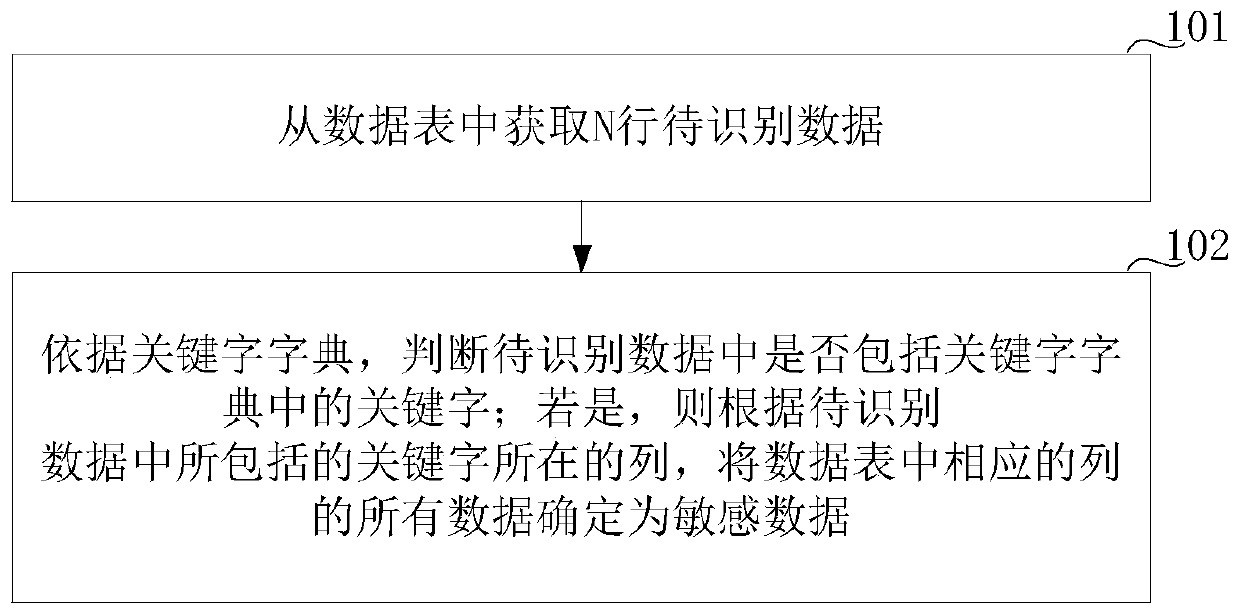
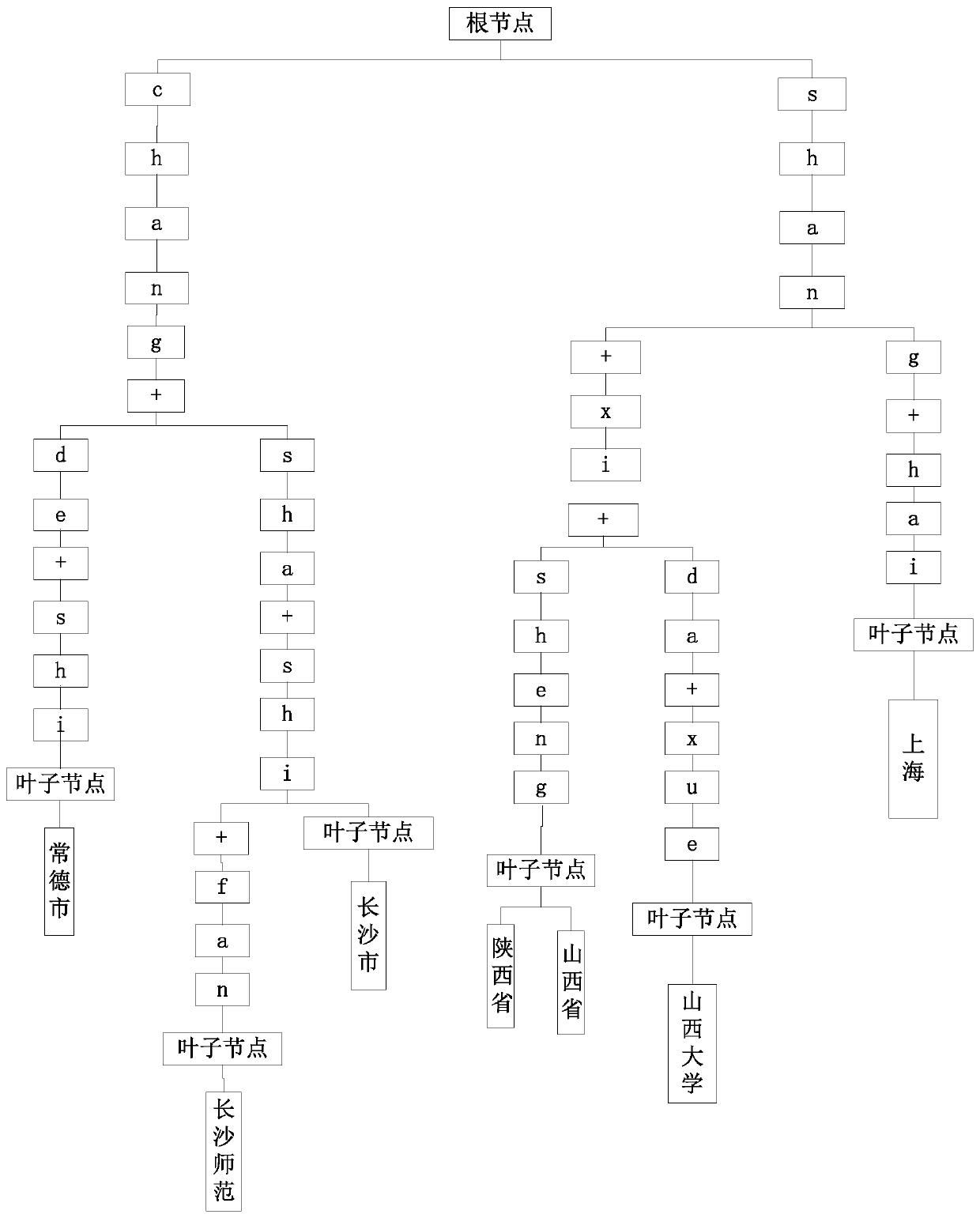
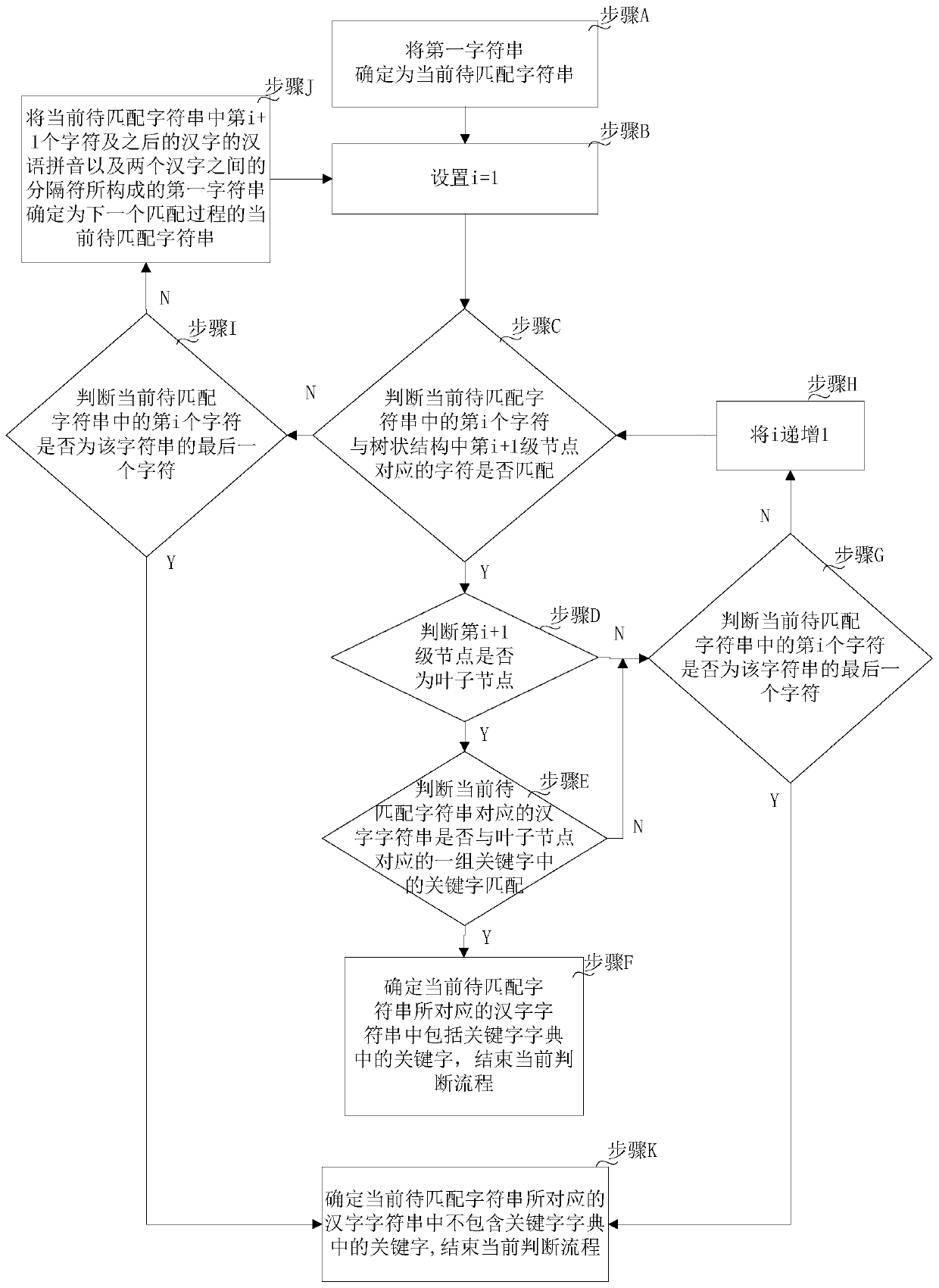
[0022] Embodiments of the present invention provide a sensitive data identification method and device. In the embodiment of the present invention, N rows of data to be identified are obtained from the data table, N≥1; according to the keyword dictionary, it is judged whether the data to be identified includes the keywords in the keyword dictionary; The column in which the keyword is included determines all data in the corresponding column in the data table as sensitive data. Since keywords are included in the keyword dictionary, when the keywords in the keyword dictionary are included in the data to be identified, it is determined that sensitive data is included in the data to be identified, and further because the N rows of data to be identified are only a part of the data table, Therefore, all the data in the columns corresponding to the keywords determined in the data table are determined as sensitive data, thereby achieving the purpose of efficiently and automatically iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com