Unauthorized resource use methods and system, base station, and user equipment
A non-authorized and resource-based technology, applied in wireless communication, electrical components, network planning, etc., can solve problems such as strong interference and collision
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
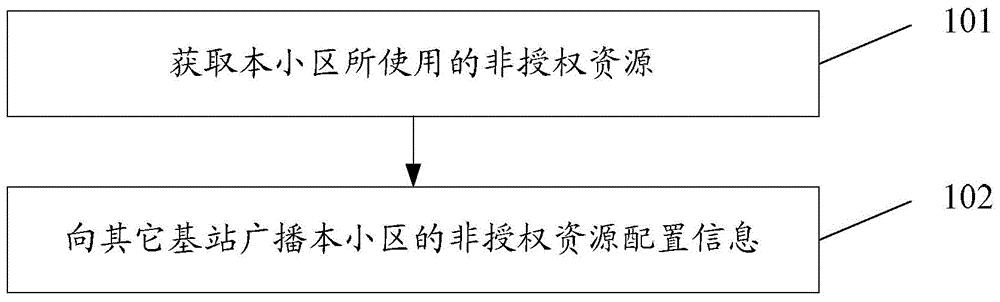
[0106] In this embodiment, a method for using unauthorized resources is applied to a base station, such as figure 1 As shown, the method includes the following steps:
[0107] Step 101: Obtain the unauthorized resources used by the cell;
[0108] Specifically, obtain the unauthorized resources used by the cell through resource competition; or,
[0109] Coordinate with other base stations in advance, and use the predefined unlicensed resources obtained through coordination as the unlicensed resources used by the cell; or,
[0110] Obtain usage information of unauthorized resources of other cells; obtain unauthorized resources used by this cell according to the unauthorized resources used by other cells.
[0111] Wherein, the non-authorized resources used by the cell are obtained through competition, specifically:
[0112] It itself or triggers subordinate UEs to compete for resources on the set unlicensed carrier to obtain unlicensed resources used by the cell.
[0113]Here...
Embodiment 2
[0201] This embodiment describes the resource coordination and sending method of the PRACH on the unlicensed carrier.
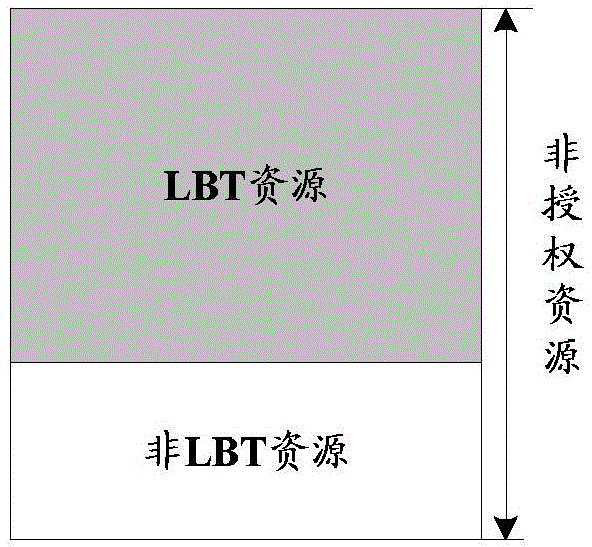
[0202] The unlicensed resources corresponding to the PRACH include time domain resources, frequency domain resources and preamble (preamble) resources, and the resource configuration of each cell can be extended on the basis of the original 64 types stipulated by LTE.
[0203] The PRACH on the unlicensed carrier can be sent in the following ways.
[0204] The first method: sending by LBT
[0205] Cells of different operators may transmit uplink and downlink data on unlicensed carriers, so there will be situations where multiple cells use unlicensed carriers to send PRACH at the same time for timing synchronization. In this case, different cells of different operators can coordinate and use limited unlicensed resources in one of the following ways:
[0206] Method 1: Cells of different operators acquire unlicensed resources of the PRACH in a TDM coordinated ...
Embodiment 3
[0256] In this embodiment, a method for coordinating and sending SRS non-authorized resources of multiple cells of different operators is described.
[0257] SRS unlicensed resources may include time domain resources (OFDM symbols, subframes), frequency domain resources, and code domain resources corresponding to different sequences and cyclic shifts.
[0258] The SRS on the unlicensed carrier can be sent in the following ways.
[0259] The first method: using a non-LBT sending method
[0260]In this way, multiple cells of multiple operators are allowed to directly obtain SRS unlicensed resources without competition, so that UEs under multiple cells of multiple operators can send SRS on unlicensed carriers, but in order to avoid Interference requires multiple operators to coordinate resources. The specific implementation methods of multi-operator multi-cell SRS resource coordination are as follows:
[0261] Method 1: Different operators use different OFDM symbols or time sl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com