Security Authentication Method for Vehicular Ad Hoc Network Based on Cuckoo Filter
A vehicle self-organization and network security technology, which is applied in the field of vehicle self-organization network security certification based on Cuckoo filter, can solve the problems of no group communication verification and no increase in verification overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the embodiments.
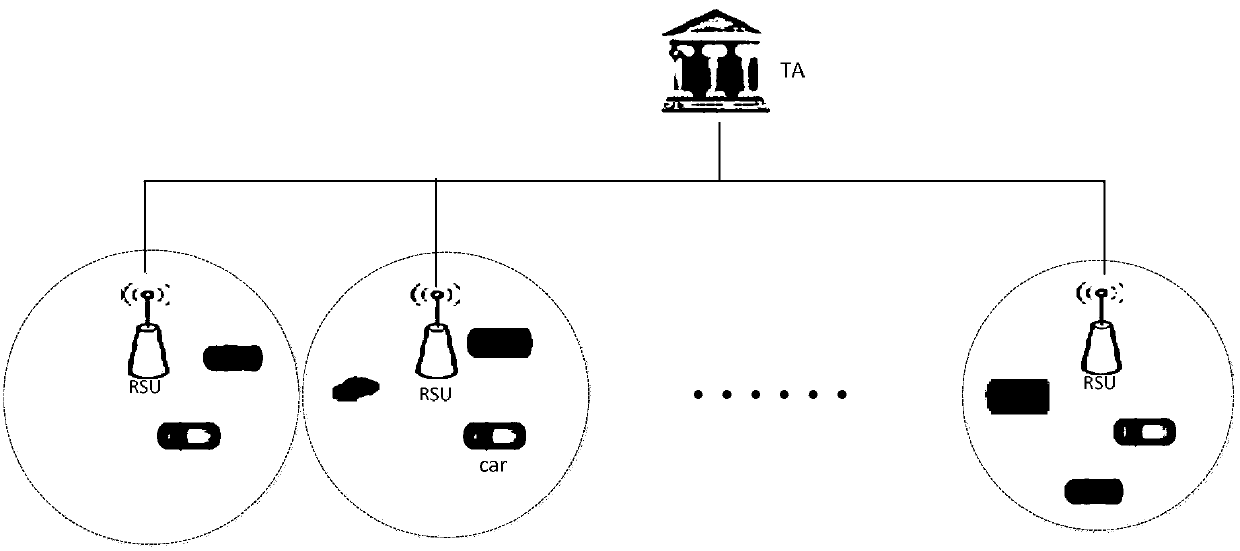
[0074] Such as figure 1 As shown, a kind of vehicle-mounted ad hoc network security authentication method based on Cuckoo filter of the present invention is divided into 2 layers: the top layer is the national credible institution TA, which is connected with RSU through a safe channel; the bottom layer has RSU and vehicle (or OBU) Composition, the communication between them is based on the dedicated short-range communication (DSRC) protocol; TA is always online, credible, and never compromised, TA can uniquely confirm the true identity of the vehicle; RSU is credible, compared to OBU, With higher computing power.
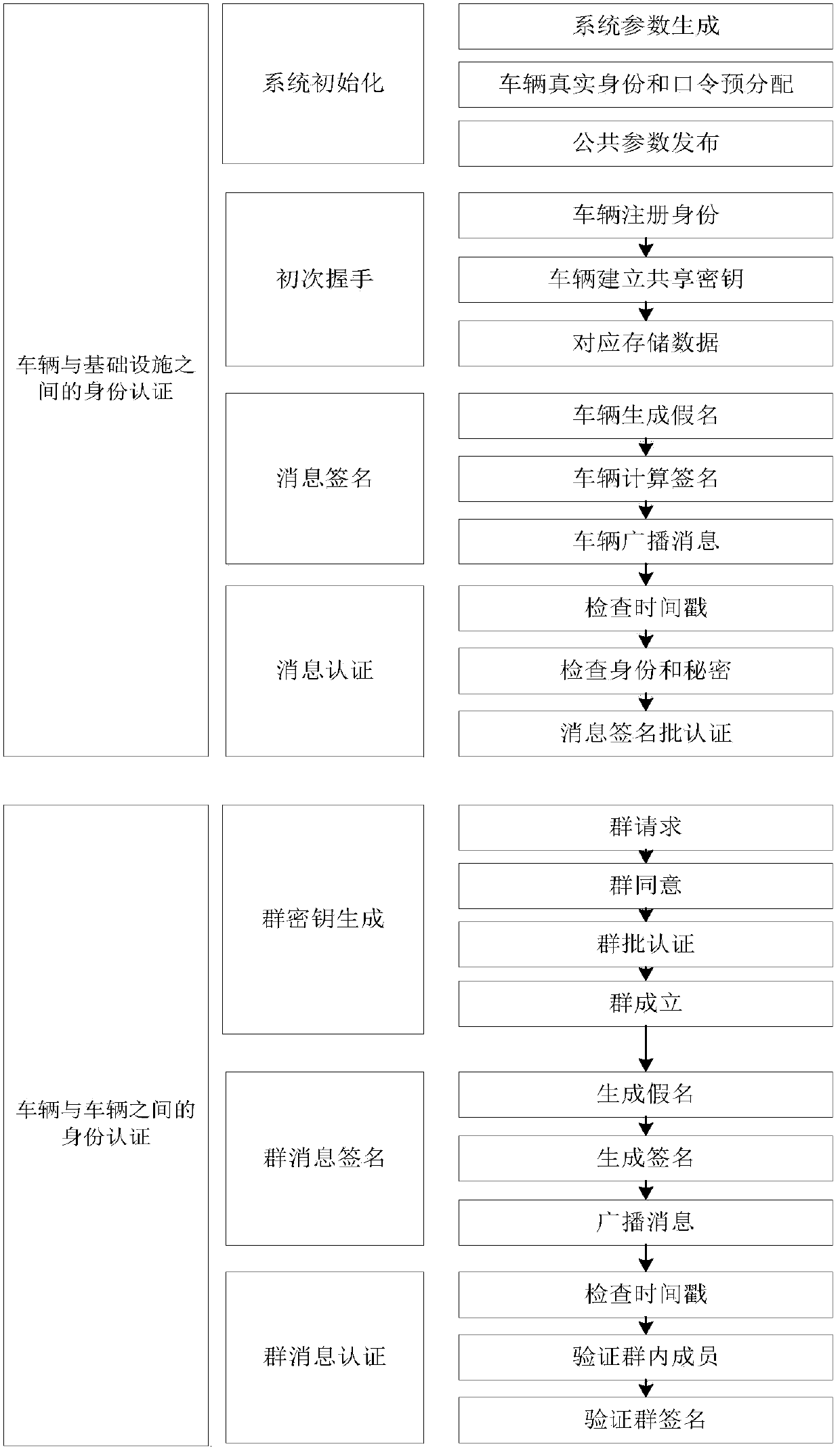
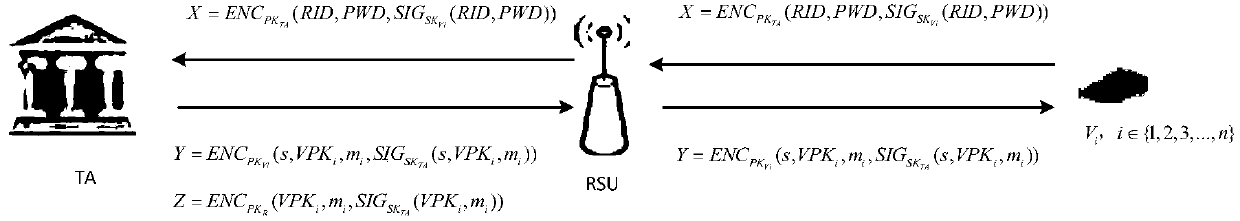
[0075] Such as figure 2 As shown, a kind of vehicle-mounted ad hoc network security authentication method based on Cuckoo filter of the present invention has two steps, are respectively: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com