Method and device for processing security services
A security business and processing method technology, applied in the field of security business processing methods and devices, to achieve the effects of protecting security, reducing audit errors, and improving audit accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
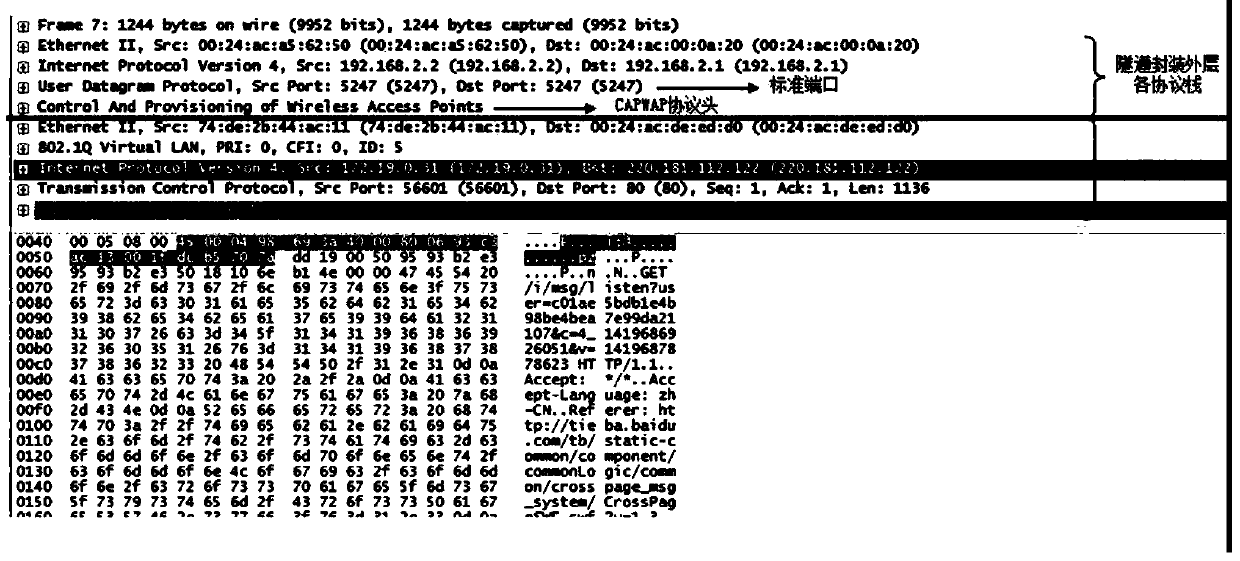
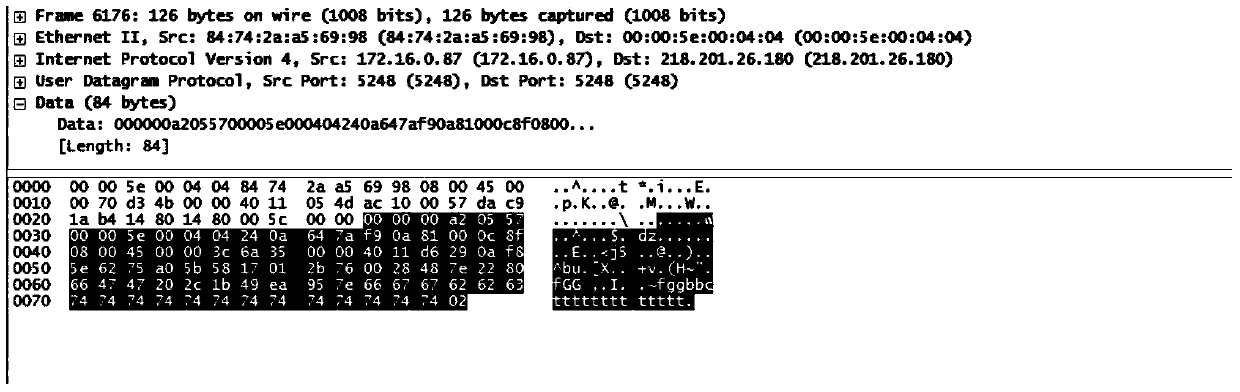
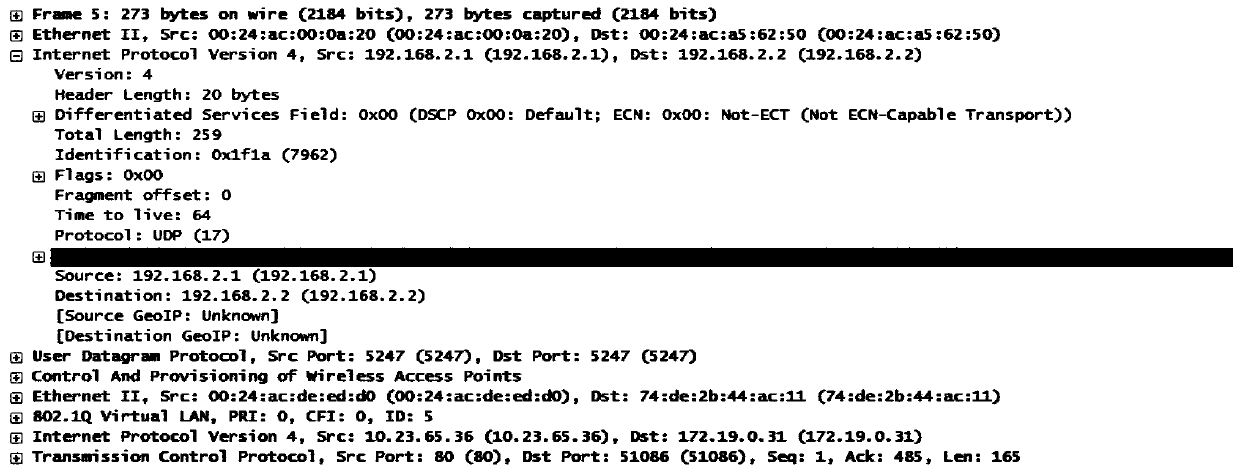
[0038]Aiming at the problems existing in the prior art, an embodiment of the present invention proposes a method for processing security services, which can be applied to a system including AC, AP and security audit equipment, and the security audit equipment is located between AC and AP . The security audit device is used to process the security services of the data packets encapsulated by the tunnel technology transmitted between the AC and the AP. Wherein, the AC and the AP may use a tunnel protocol to encapsulate the data message, for example, use the CAPWAP tunnel protocol to encapsulate the data message. The security audit device obtains the data packets encapsulated by the tunnel protocol, and performs security service processing on this type of data packets. like Figure 5 As shown, it is a schematic diagram of the format of a data packet transmitted between the AP and the AC, and the data packet includes tunnel outer layer information and tunnel inner layer informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com