Role optimization method and apparatus in RBAC permission system
An optimization method and role technology, applied in the direction of digital data authentication, etc., can solve the problems of the same or overlapping permissions, increase user access permissions, system security risks, etc., and achieve the effect of reducing system security risks and reducing the same or overlapping permissions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] In order to make the above objects, features and advantages of the present application more obvious and comprehensible, the present application will be further described in detail below in conjunction with the accompanying drawings and specific implementation methods.
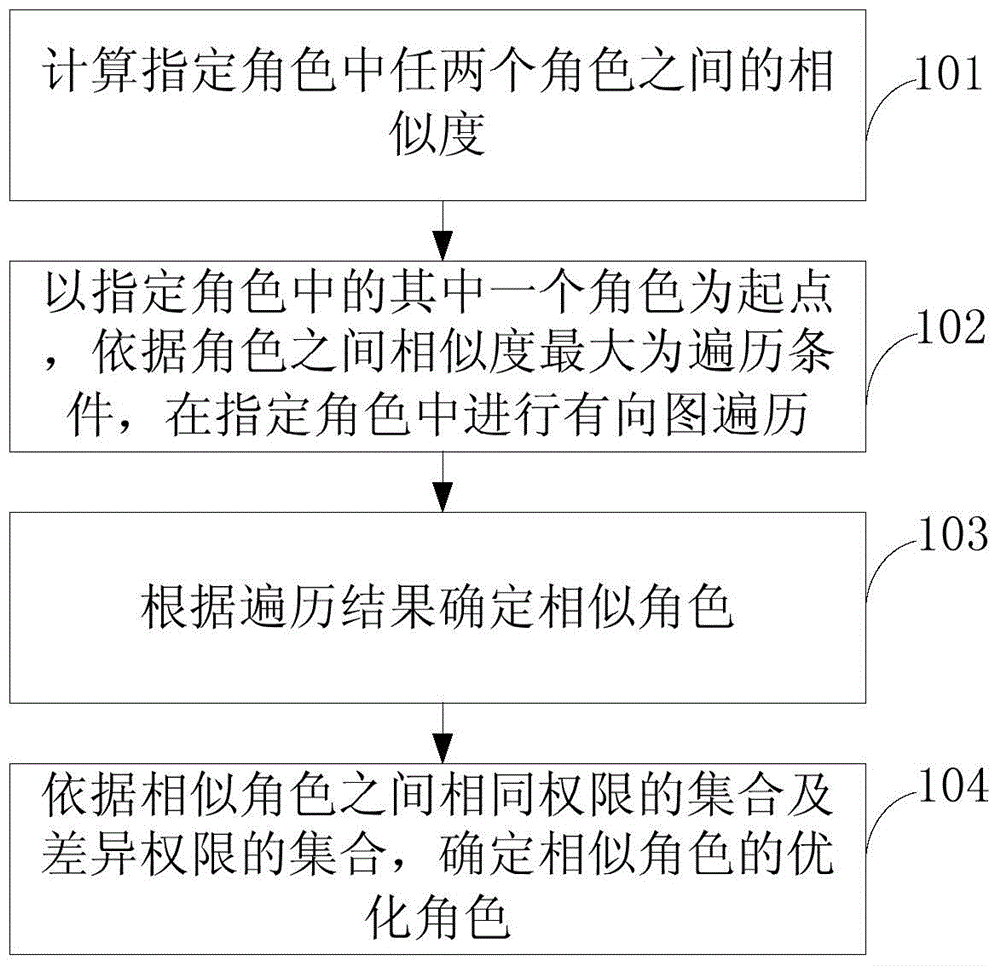
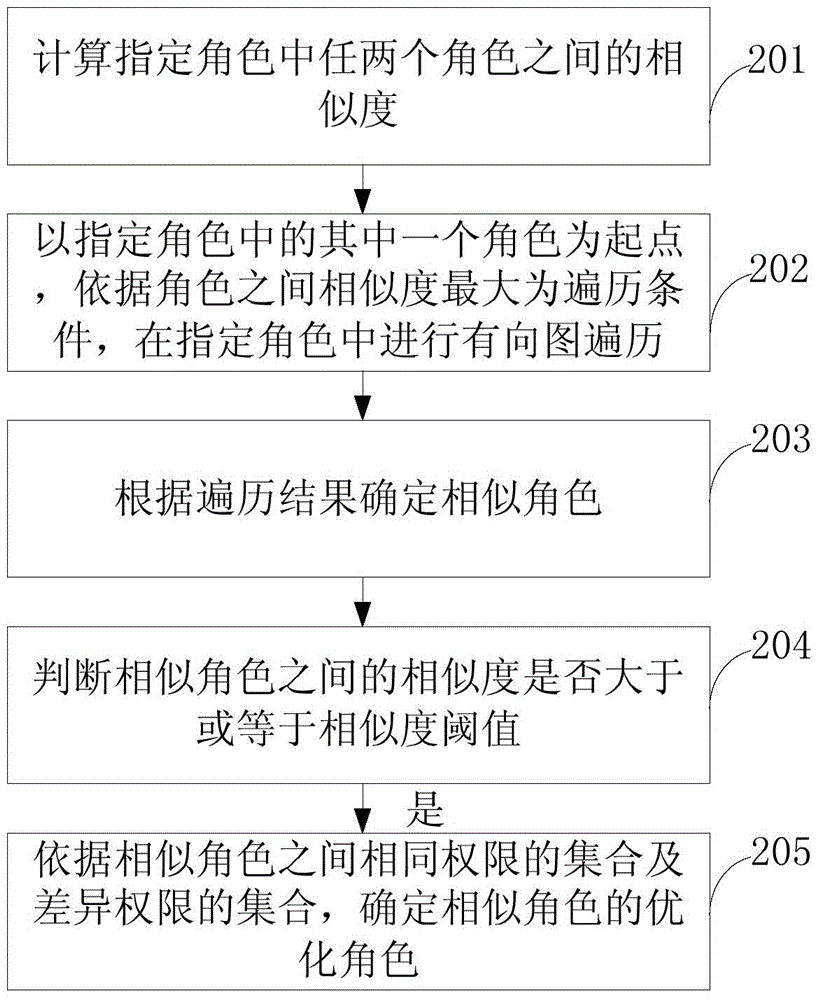
[0052] refer to figure 1 , which shows a flow chart of the steps of an embodiment of a role optimization method in an RBAC authority system of the present application, which may specifically include the following steps:
[0053] Step 101, calculating the similarity between any two roles in the specified roles.
[0054] In this step, the specified role may be all roles or some roles that need to be optimized in the role-permission relationship table of a certain system under the RBAC authority system. The similarity between two roles can be calculated based on the permission sets of the two roles. Take the calculation of jaccard similarity as an example:
[0055] I ( ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com