Identification method and identification device for cheating behavior
An identification method and identification device technology, applied in the computer field, can solve the problem of ignoring the sequence of account history behavior and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
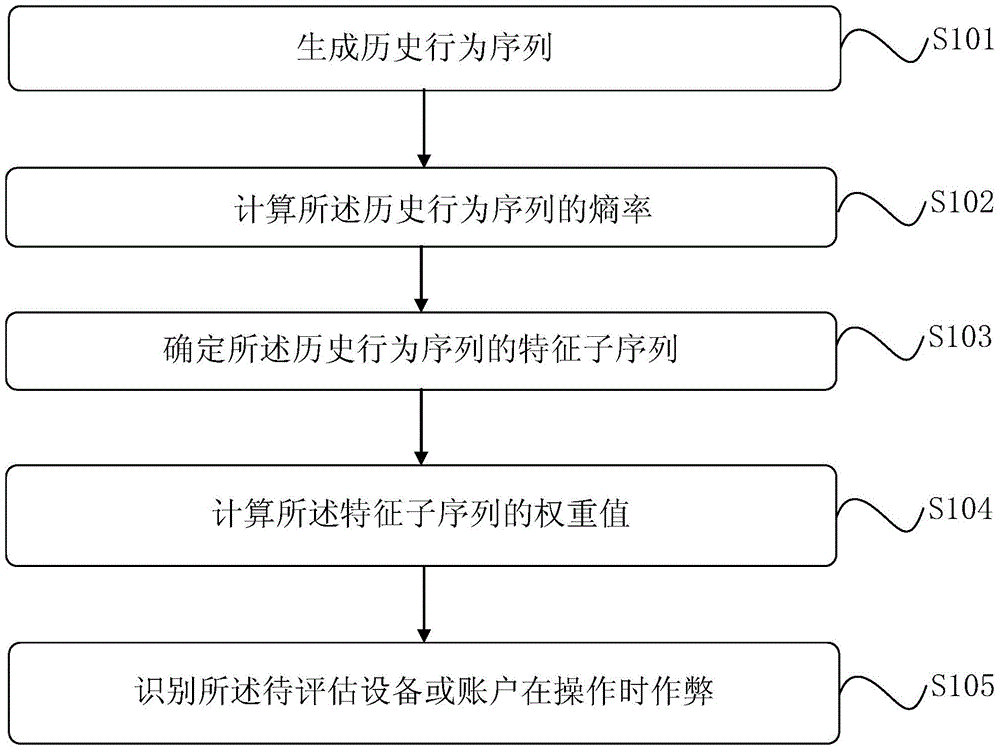
[0083] In the embodiment of the present invention, it is possible to identify whether the device to be evaluated or the account is cheating by calculating the entropy rate value of the historical behavior event. In order to further improve the recognition probability, historical feature behaviors in the equipment to be evaluated or historical behavior events of accounts can be mined. Combining the weight value of the historical characteristic behavior and the entropy rate value to identify whether the device to be evaluated or the account implements a cheating behavior. The specific implementation steps are as figure 1 shown, including:
[0084] Step S101: Generate a historical behavior sequence according to the historical behavior of the device or account to be evaluated.
[0085] In actual situations, cheaters can use one account to cheat on one device, or use one account to cheat on multiple devices, or use multiple accounts to cheat on one device. Additionally, cheaters...
Embodiment 2
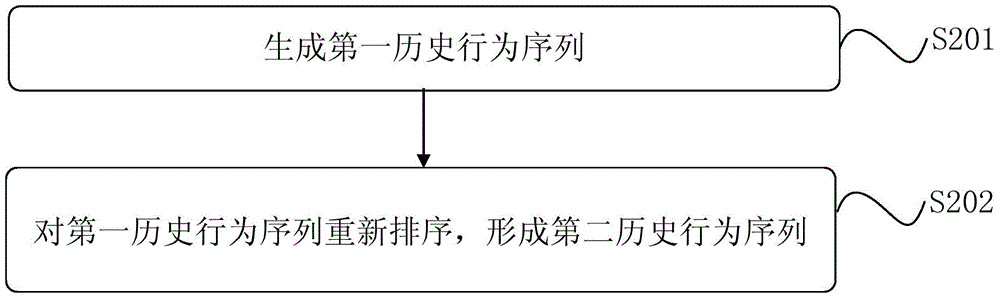
[0117] In order to further consider the sequentiality of the historical behavior sequence, the historical behavior sequence is segmented in the method for calculating the entropy rate in the above embodiment. Combining the weight value of the historical characteristic behavior and the entropy rate value to identify whether the device to be evaluated or the account implements a cheating behavior.
[0118] In this embodiment, multiple different entropy rates can be obtained according to different segmentation results of the historical behavior sequence, and the minimum value of the multiple entropy rates can be used as the entropy rate of the historical behavior sequence. Of course, this embodiment is not limited thereto, and other methods may also be used to determine the entropy rate of the historical behavior sequence.
[0119] The implementation method steps of this embodiment are the same as those of the previous embodiment. Step S101 is the same as the specific implementa...
Embodiment 3
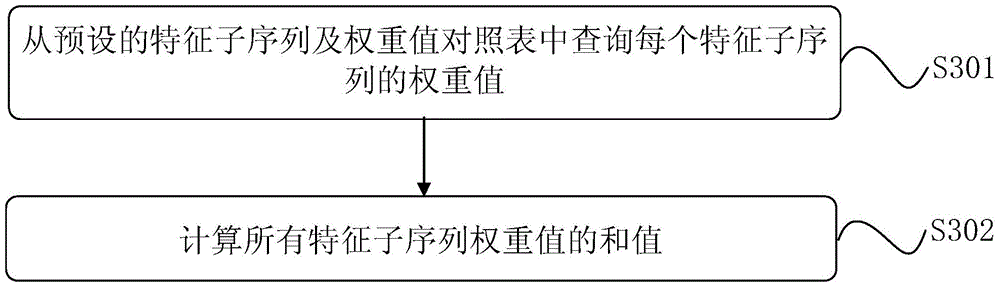
[0161] In the second method embodiment, the extraction of feature subsequences may not be considered, and only the entropy value of the historical behavior time is calculated in segments, and the cheating behavior of the device or account to be evaluated may also be identified. The third embodiment of the method for identifying cheating is introduced below, such as Figure 7 As shown, there are five steps:
[0162] Step S701: Generate a historical behavior sequence according to the historical behavior events of the device or account to be evaluated.
[0163] The implementation manner is the same as that of step S101, and will not be repeated here.
[0164] Step S702: According to different orders, perform segmentation processing corresponding to the order on the historical behavior sequence to form different segmentation results.
[0165] The implementation manner is the same as that of step S401, and will not be repeated here.
[0166] Step S703: Calculate the corrected co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com