Proxy interception
A technology of proxy nodes and codes, applied in the field of intercepted protocols, which can solve problems such as lack of migration paths
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0120] In the following detailed description, different embodiments of the present disclosure will be described in more detail with reference to the accompanying drawings. Specific details, such as specific examples and techniques, are described for purposes of illustration and not limitation, to provide a thorough understanding.
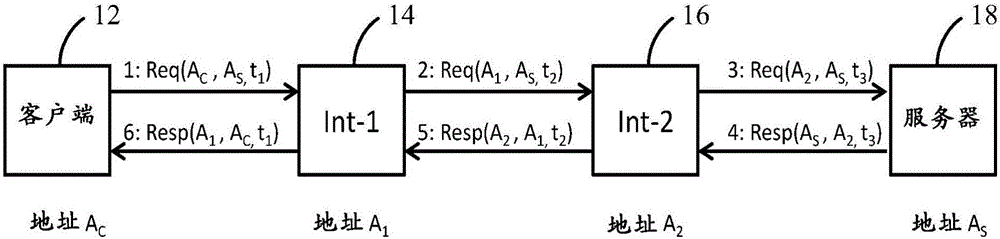
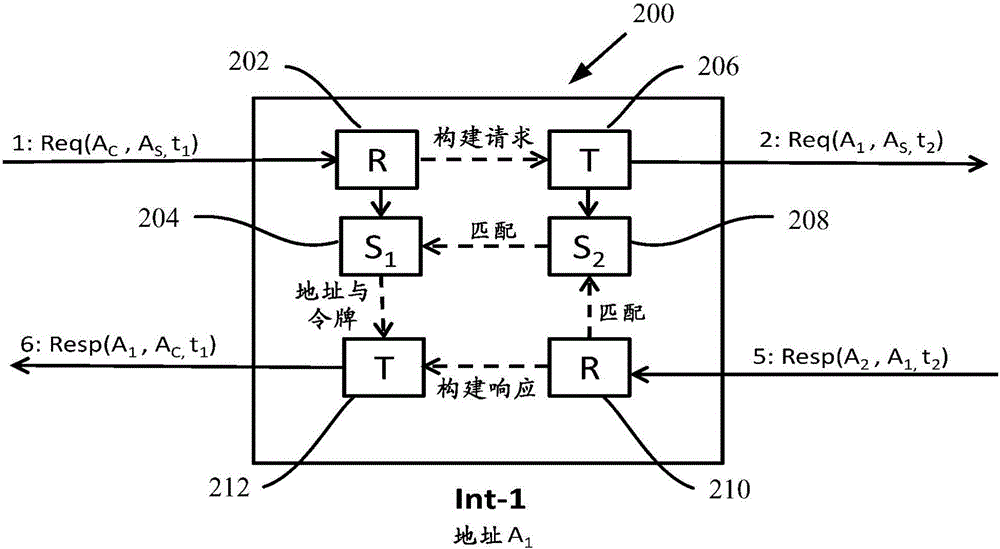
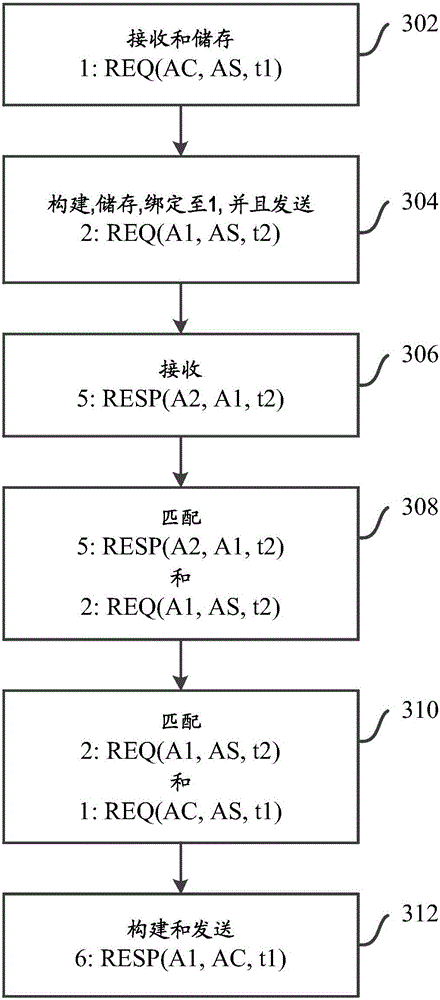
[0121] Embodiments of the present disclosure address at least some of the above-described problems of existing proxy network connections through an inventive non-transparent proxy that intercepts connectionless protocols such as CoAP over UDP / IP or NetInf.
[0122] Embodiments enable communication between a client node, a proxy node, and a server node on an end-to-end path between a client node and a server node without necessarily being in any of the client node or neighboring proxy nodes Configure the address of the proxy node, or do not have to configure a new routing protocol to reach the proxy node. Furthermore, the solution allows expansion b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com