Network monitoring log updating method
A network monitoring and updating method technology, applied in hardware monitoring, database updating, structured data retrieval and other directions, can solve problems such as low efficiency, and achieve the effect of ensuring real-time and validity, efficient retrieval and query
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
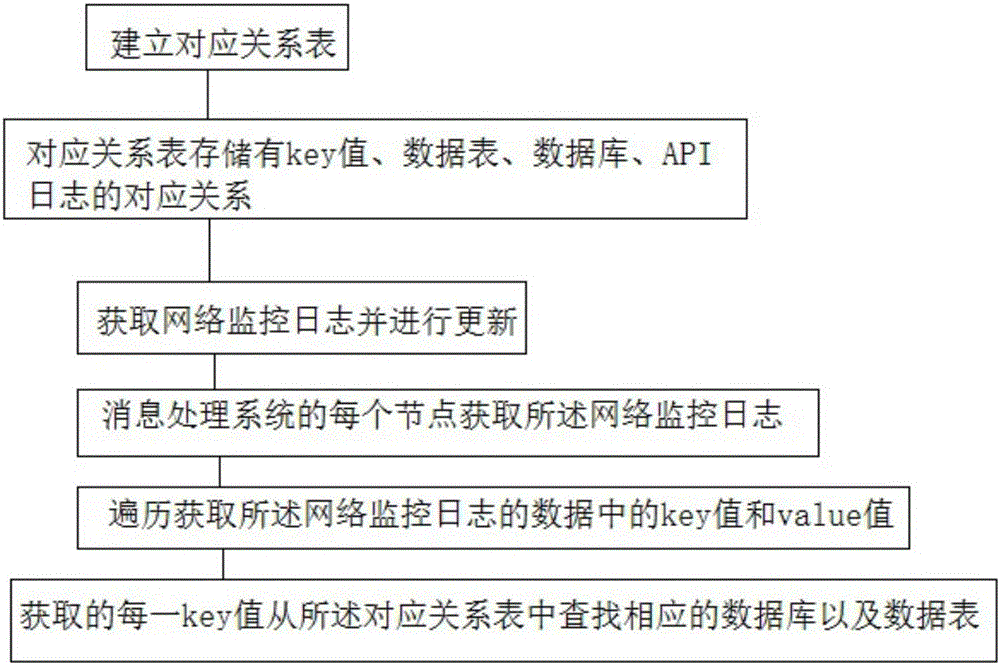
[0011] Such as figure 1 As shown, embodiment 1: the technical scheme that the present invention adopts is: a kind of update method of network monitoring log, it is characterized in that, establishes correspondence table, and described correspondence table stores key value, data table, database, API log Corresponding relationship, each database includes a plurality of data tables, each data table is recorded with a value value corresponding to the key value, and the update method also includes the following steps: S1. Obtain and update the network monitoring log, and the The network monitoring log is sent to the message processing system; S2, each node of the message processing system obtains the network monitoring log; S3, traverses and obtains the key value and value value in the data of the network monitoring log; S4, according to S3 Each key value obtained searches the corresponding database and data table from the corresponding relationship table; S5, generating a list of ...
Embodiment 2
[0012] Embodiment 2: the technical scheme that the present invention adopts is: a kind of update method of network monitoring log, it is characterized in that, establishes correspondence table, and described correspondence table stores the correspondence relation of key value, data table, database, API log , each database includes a plurality of data tables, each data table is recorded with a value value corresponding to the key value, and the update method also includes the following steps: S1, obtaining and updating the network monitoring log, and updating the network monitoring log to send to the message processing system; S2, each node of the message processing system obtains the network monitoring log; S3, traverses and obtains the key value and value in the data of the network monitoring log; S4, according to each node obtained in S3 A key value searches corresponding database and data table from described correspondence table; S5, generate credible file list: comprise th...
Embodiment 3
[0013] Embodiment 3: the technical scheme that the present invention adopts is: a kind of update method of network monitoring log, it is characterized in that, establish correspondence table, described correspondence table stores the correspondence relation of key value, data table, database, API log , each database includes a plurality of data tables, each data table is recorded with a value value corresponding to the key value, and the update method also includes the following steps: S1, obtaining and updating the network monitoring log, and updating the network monitoring log to send to the message processing system; S2, each node of the message processing system obtains the network monitoring log; S3, traverses and obtains the key value and value in the data of the network monitoring log; S4, according to each node obtained in S3 A key value searches corresponding database and data table from described correspondence table; S5, generate credible file list: comprise the foll...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com