Docker container creating method and creating system
A docker container and system-defined technology, applied in the creation system and the field of Docker container creation, can solve hidden dangers, and the security issues left by Docker containers, so as to achieve the effect of strengthening security, avoiding security threats, and simplifying the mandatory access control process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
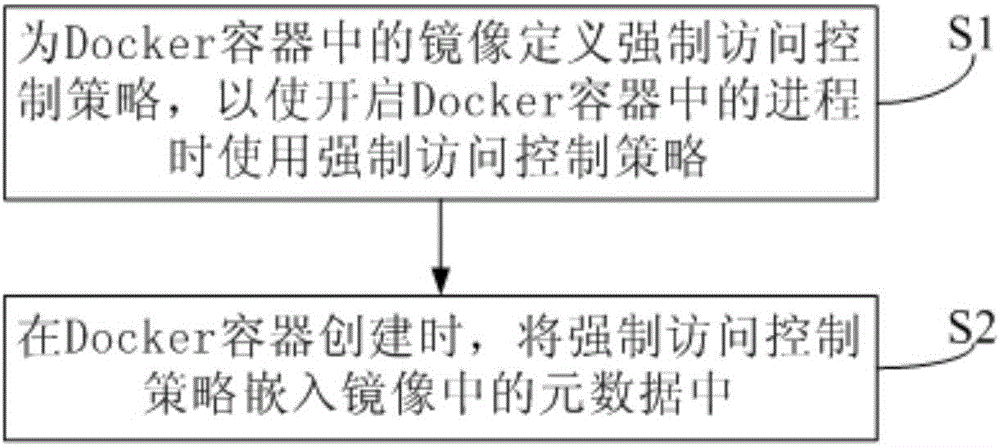
[0047] This embodiment provides a method for creating a Docker container, such as figure 1 shown, including:
[0048] Step S1: Define a mandatory access control policy for the image in the Docker container, so that the mandatory access control policy is used when starting the process in the Docker container.
[0049] Step S2: When the Docker container is created, the mandatory access control policy is embedded in the metadata in the image.
[0050] The method for creating the Docker container provides a customized mandatory access control policy for the mirror image in the Docker container, so that the mandatory access control policy can be used when running the mirror image in the process, thereby avoiding When the process in the Docker container is run during the call, it poses a threat to the security of the Docker container, and strengthens the security of the Docker container; at the same time, it also simplifies the mandatory access control process when the system calls...
Embodiment 2
[0052] This embodiment provides a method for creating a Docker container, including:
[0053] Step S1: Define a mandatory access control policy for the image in the Docker container, so that the mandatory access control policy is used when starting the process in the Docker container.
[0054] In this step, defining mandatory access control policies for images in Docker containers includes:
[0055] Step S11: Define a name for the mandatory access control policy according to the function of the image.
[0056] For example: policy_module(docker_apache, 1.0), that is, the name of the mandatory access control policy is docker_apache, which means that the Apache service program is running in the Docker container.
[0057] Step S12: Define the mandatory access control type of the image.
[0058] For example, virt_sandbox_domain_template(httpd_t), which defines the mandatory access control type of the image as httpd_t.
[0059] Step S13: Define the upper bound of the type authori...
Embodiment 3
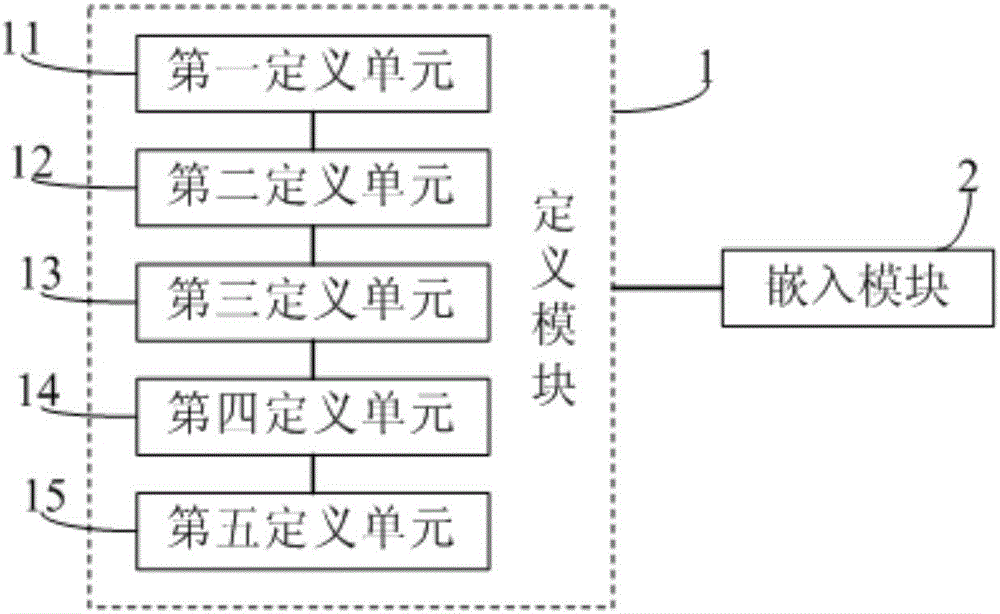
[0080] This embodiment provides a system for creating a Docker container, such as image 3 As shown, it includes: definition module 1, which is used to define the mandatory access control policy for the image in the Docker container, so that the mandatory access control policy is used when starting the process in the Docker container. The embedding module 2 is used to embed the mandatory access control policy into the metadata in the image when the Docker container is created.
[0081] The creation system of the Docker container can provide a customized mandatory access control policy for the image in the Docker container by setting the definition module 1 and the embedding module 2, so that the mandatory access control policy can be used when running the image in the process, thereby avoiding host When the kernel (such as the Linux operating system) runs the process in the Docker container in different system calls, it poses a threat to the security of the Docker container, w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com