Identifier generating method and apparatus
A technology of identifiers and application identifiers, applied in the field of communication, can solve the problems of inability to judge the legitimacy of mobile phones, non-unique identifiers, functional logic problems, etc., and achieve the effect of ensuring uniqueness and accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
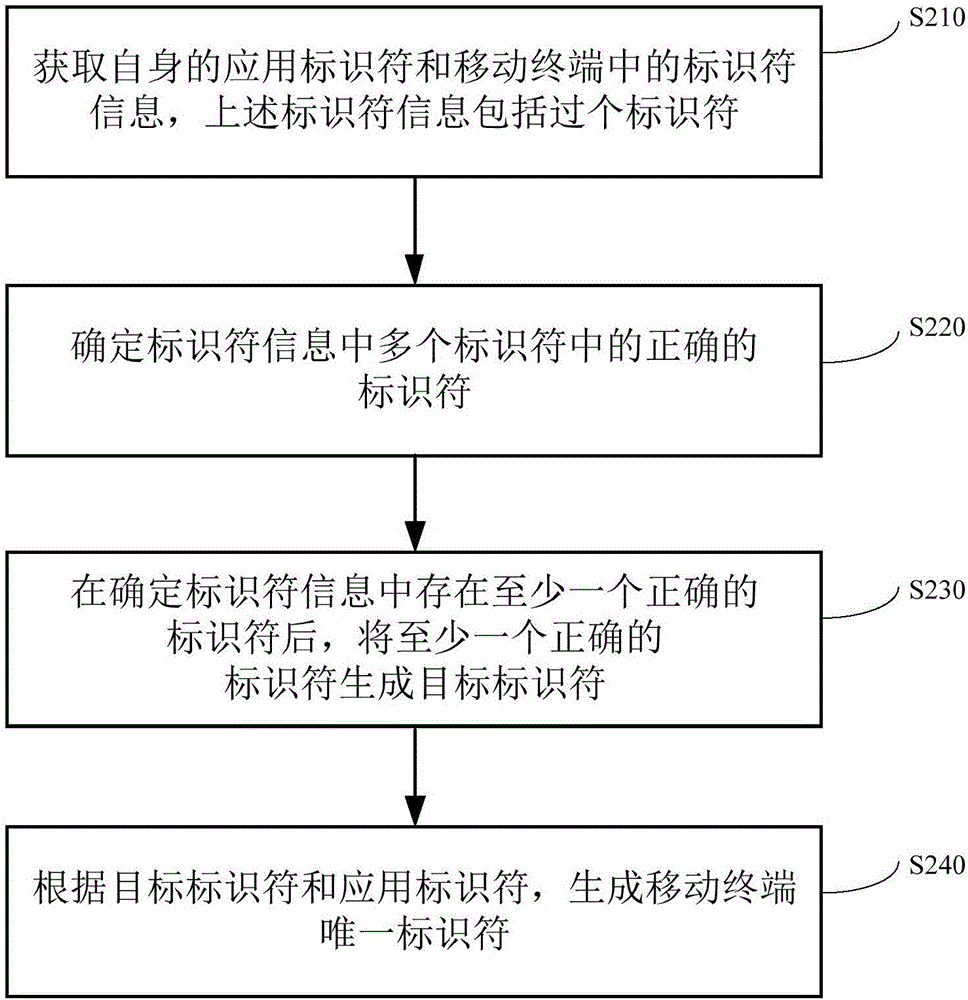
[0068] According to one embodiment, the target identifier and the application identifier are combined using a first encryption algorithm to obtain an encrypted identifier. The encrypted identifier is encrypted by using the second encryption algorithm to obtain the unique identifier of the mobile terminal. For example, the target identifier in step S230 is simply combined with its own application identifier, and the string after the simple combination is encrypted using an MD5 algorithm or a hash algorithm to obtain an encrypted string, and then using the US data encryption standard ( DES algorithm) encrypts the above-mentioned encrypted string again to obtain the unique identifier of the mobile terminal. In one embodiment, the application in the mobile phone is a paid application. The application in the mobile phone obtains the unique identifier of the mobile phone and sends it to the server. The server will save the unique identifier. When the application in the mobile phone ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com