An embedded terminal encryption system and encryption method combining software and hardware
An embedded terminal and encryption system technology, applied in encryption devices with shift registers/memory, transmission systems, digital transmission systems, etc., can solve problems such as product cracking, increasing the difficulty of cracking products, and unsatisfactory encryption effects. , to achieve the effect of preventing competitors, low encryption cost, and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
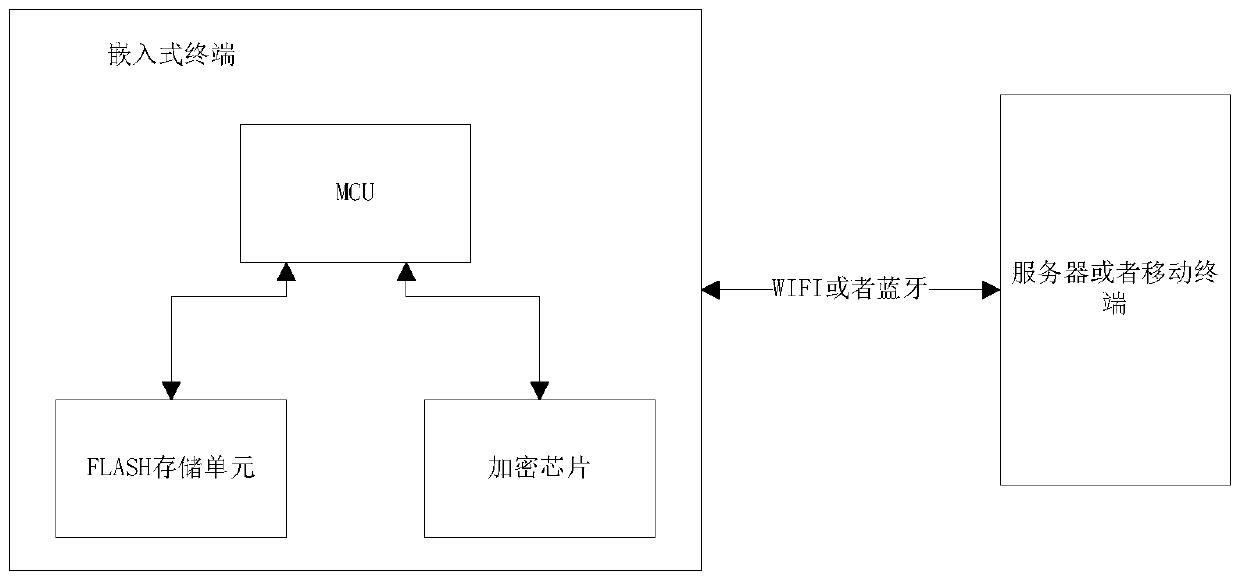
[0050] Such as figure 1 As shown, an embedded encryption system includes an embedded terminal and a server or a mobile terminal, and the two communicate through WIFI or Bluetooth.
[0051] Embedded terminal includes MCU, FLASH storage unit, encryption chip. The MCU is the main control unit, which is connected with the FLASH storage unit and the encryption chip to transmit data and command information; the FLASH storage unit is used to store valid information that needs to be saved, and is controlled by the MCU. The encryption chip is responsible for the encryption operation, and the encryption method is selected through the control of the MCU.
[0052] The server or mobile terminal communicates with the embedded terminal to realize the verification of encrypted information between the two to ensure the security of the system.
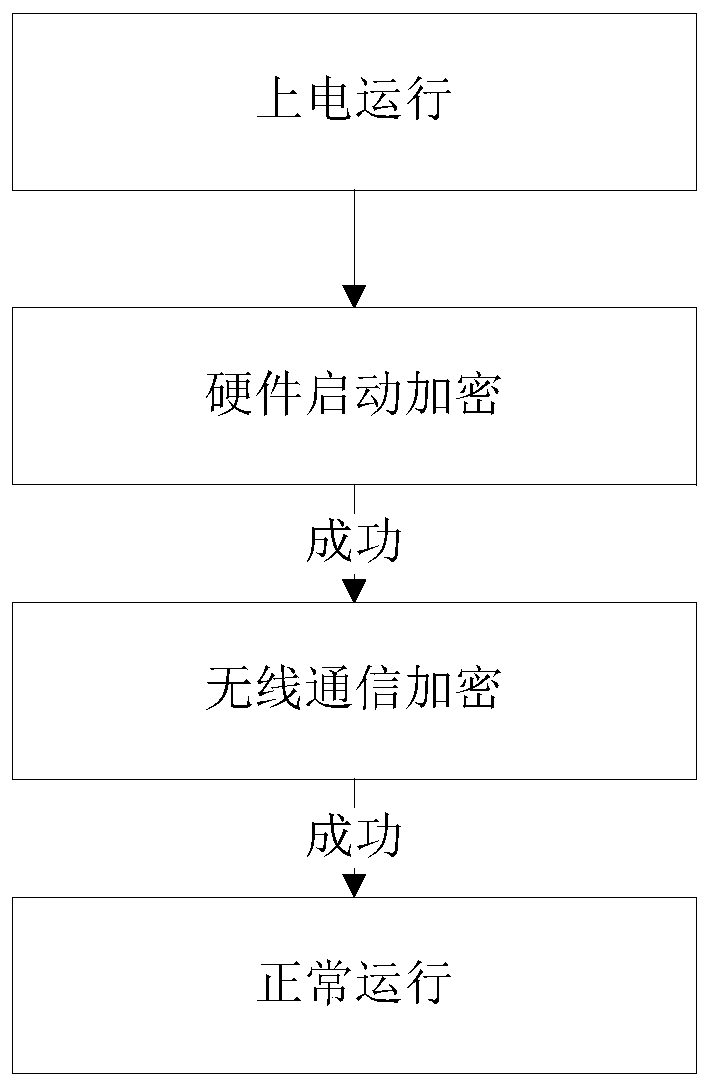
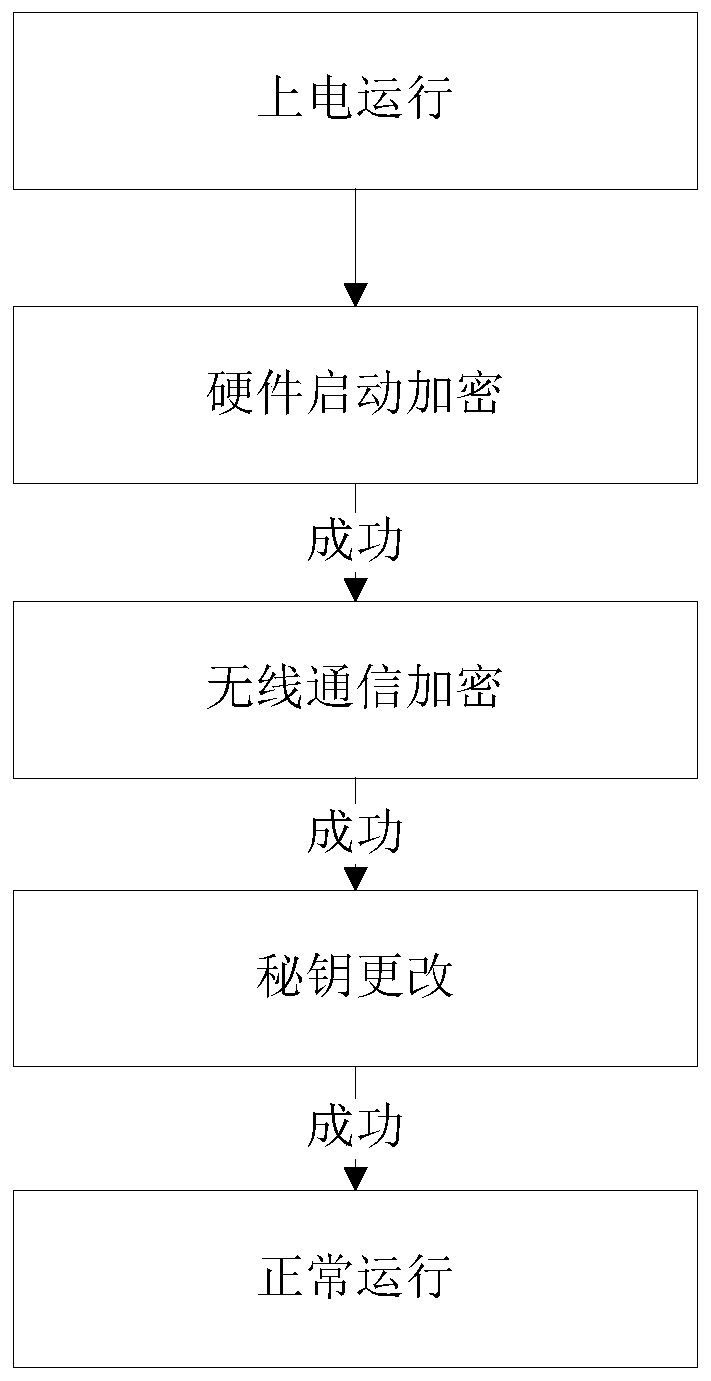
[0053] Such as figur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com