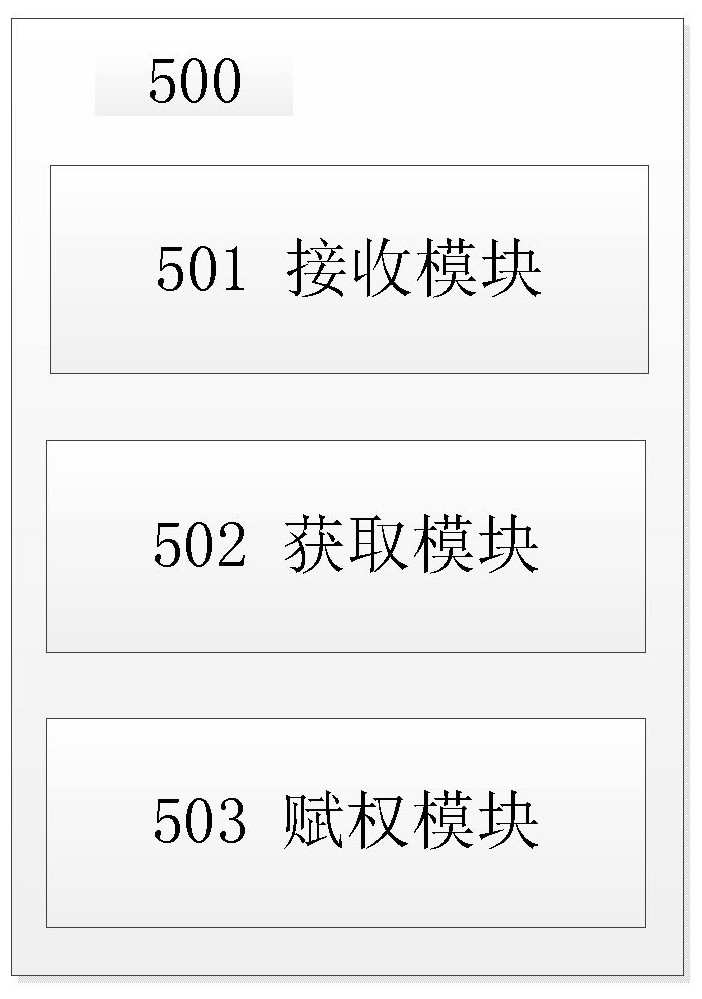
Patents
Literature
43results about How to "Prevent malicious cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
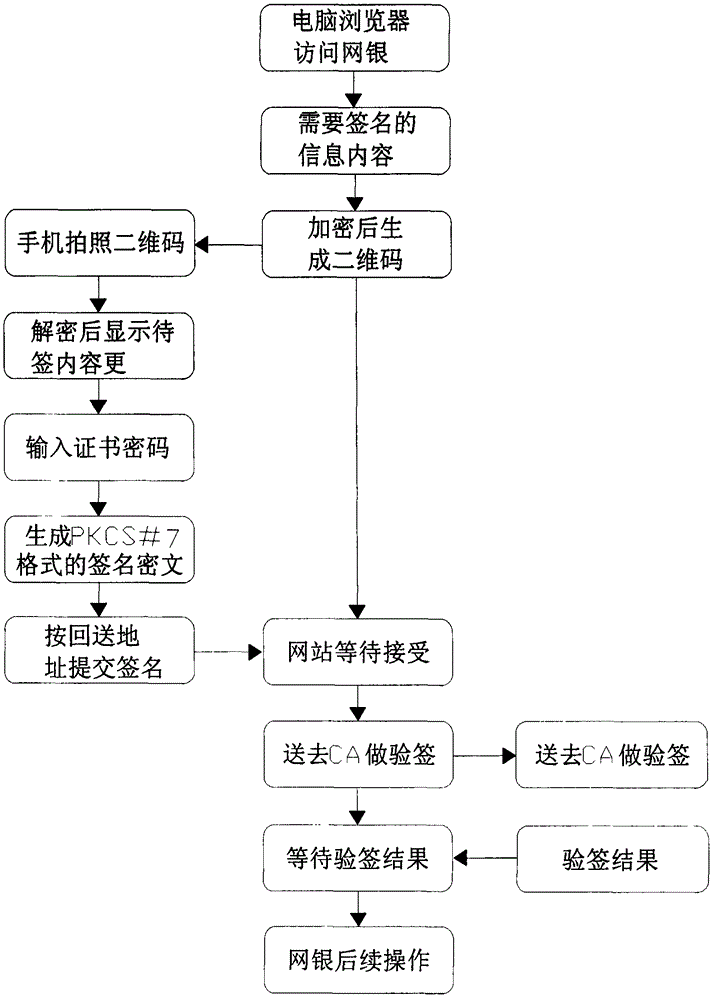
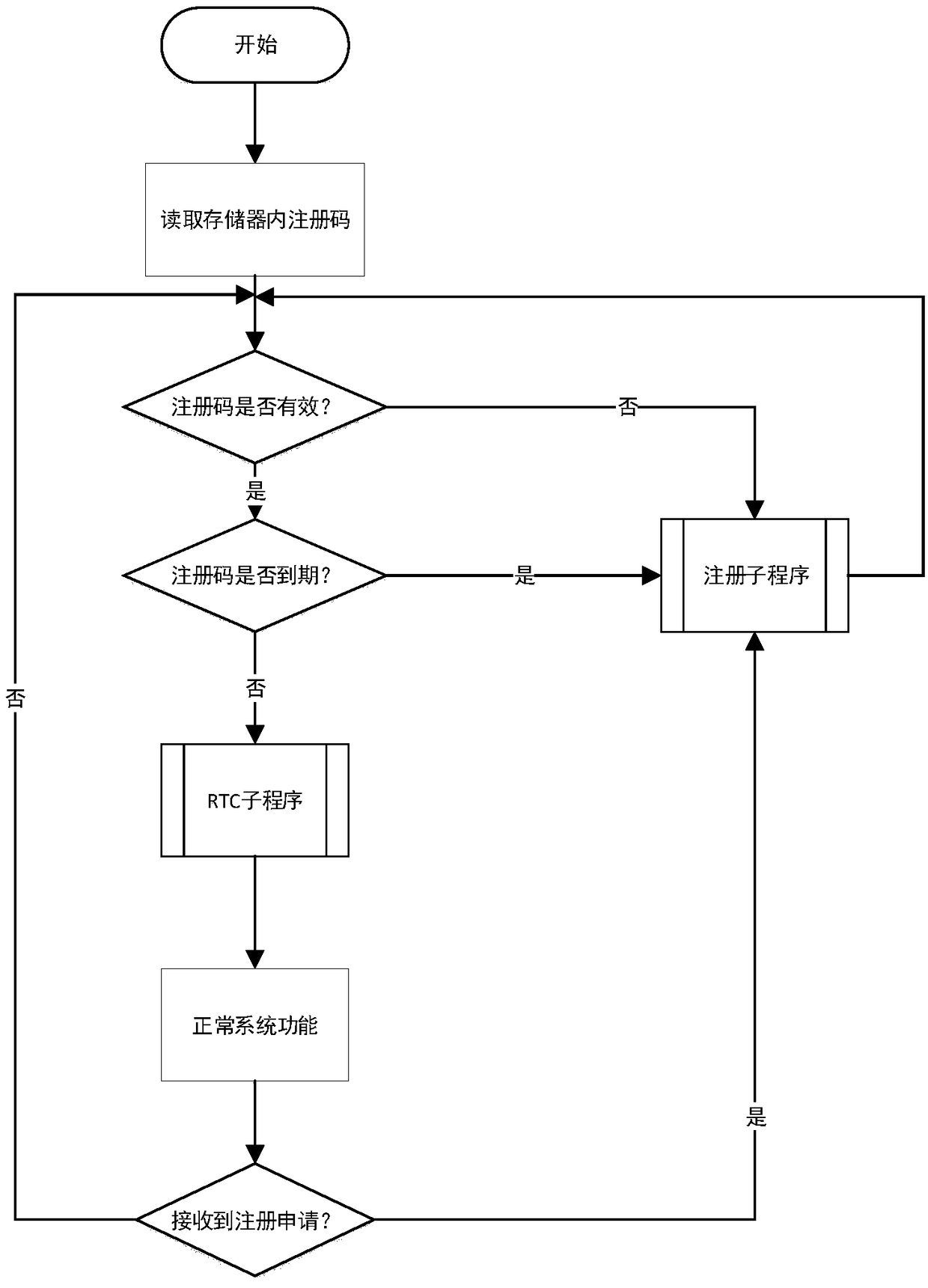
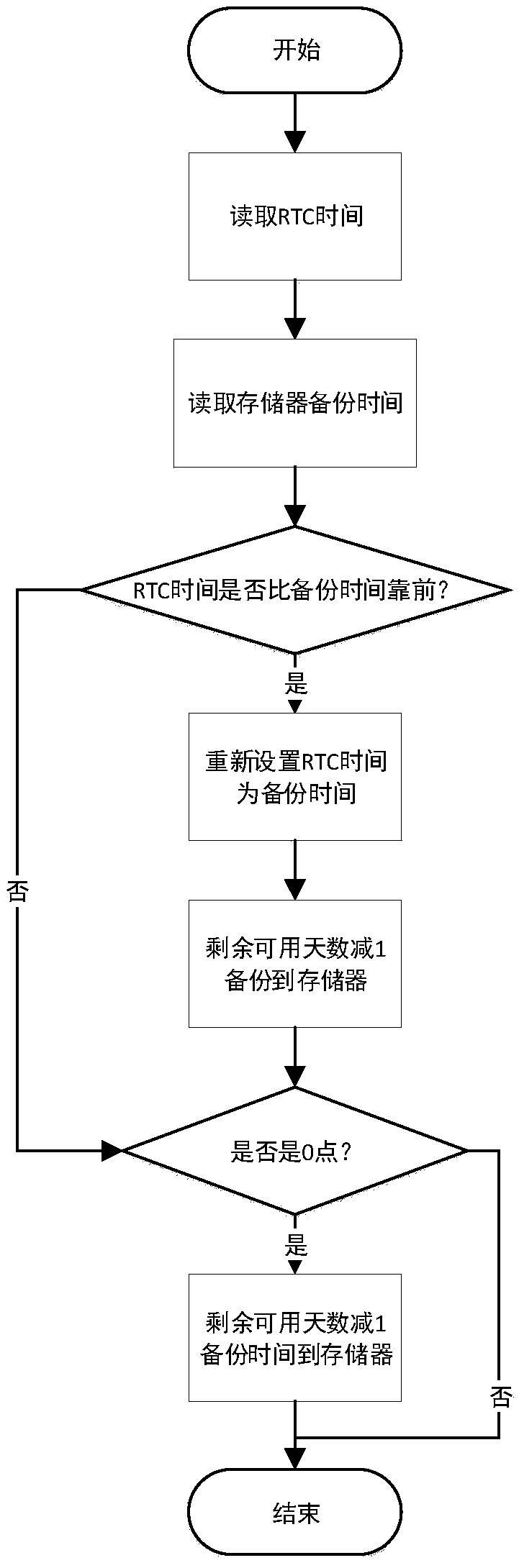
Mobile terminal digital certificate electronic signature method
ActiveCN105323062AIngenious ideaReasonable ideaUser identity/authority verificationIssuing bankInternet privacy
The invention relates to a mobile terminal digital certificate electronic signature method. According to the method, based on the characteristics of public keys and private keys and on the premise of not violating the rules prescribed by the electronic signature law, for example, a private key should be generated in a user terminal and should not leave the user terminal, a private key should not be transmitted via the network, and the like, a private key is discarded and locally and discretely stored after encryption, and the cloud uses strategies such as storing the public key and certificate to ensure that the private key is not locally cracked. In the transport layer, strategies such as double key and one-time pad are adopted to ensure that important information is not intercepted and decoded in network transmission. The identity of a certificate applicant is verified through the interface of an issuing bank, the user identity verification result of the bank counter is inherited, and therefore, remote online certificate issuing is realized in the system. The method not only can ensure that all the links of certificate applying, certificate issuing, certificate storing and certificate using are safe, but also can prevent hackers and Trojans from stealing certificate files, prevent network package-capture parsing, prevent password intercepting through screen capture and prevent an algorithm from being known through software decompiling.
Owner:BANKEYS TECH
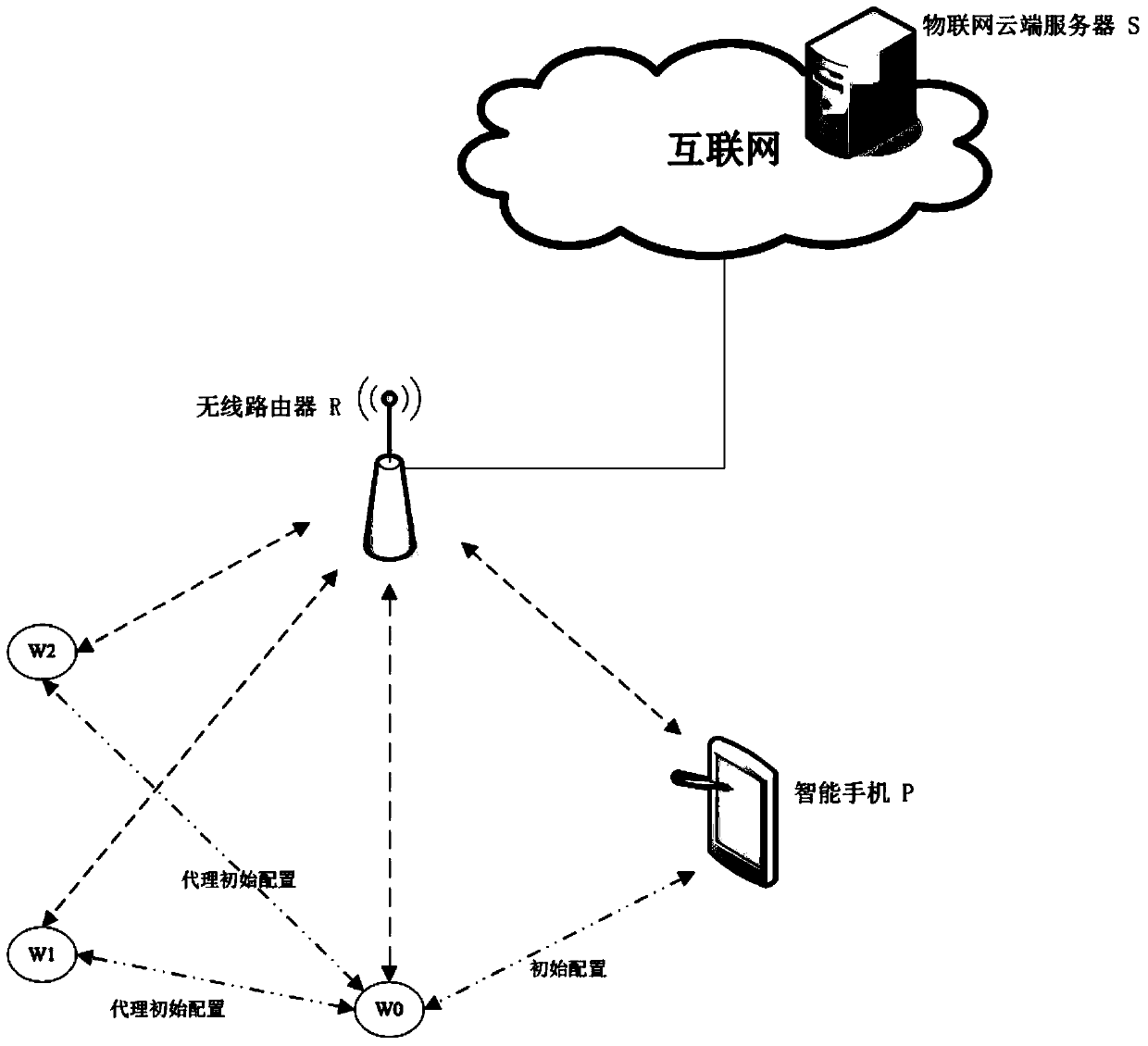
Implementation method of safe batch configuration of Wi-Fi Internet of Things system
ActiveCN104202308AProtect transmission securityPrevent malicious crackingTransmissionWi-FiComputer hardware
The invention discloses an implementation method of safe batch configuration of a Wi-Fi Internet of Things system, a master device in the Wi-Fi Internet of Things is configured through a safe manner, and then authentication and configuration are carried out on other devices in the Wi-Fi Internet of Things by the master device through a point-to-multipoint manner; the master device utilizes two different MAC (Media Access Control) addresses and synchronously supports two working modes including Wi-Fi Soft-AP and Wi-Fi STA; a mobile terminal of a user carries out initial configuration on the master device of the Wi-Fi Internet of Things in the Wi-Fi Soft-AP mode; and the master device is connected to other devices in the same group through the other Wi-Fi function to help other devices to complete agent initial configuration. According to the implementation method, a large amount of Wi-Fi Internet of Things devices are completed through a form of exponential growth, privacy data security is guaranteed and a large amount of manual cost can be saved.
Owner:ESPRESSIF SYST SHANGHAI
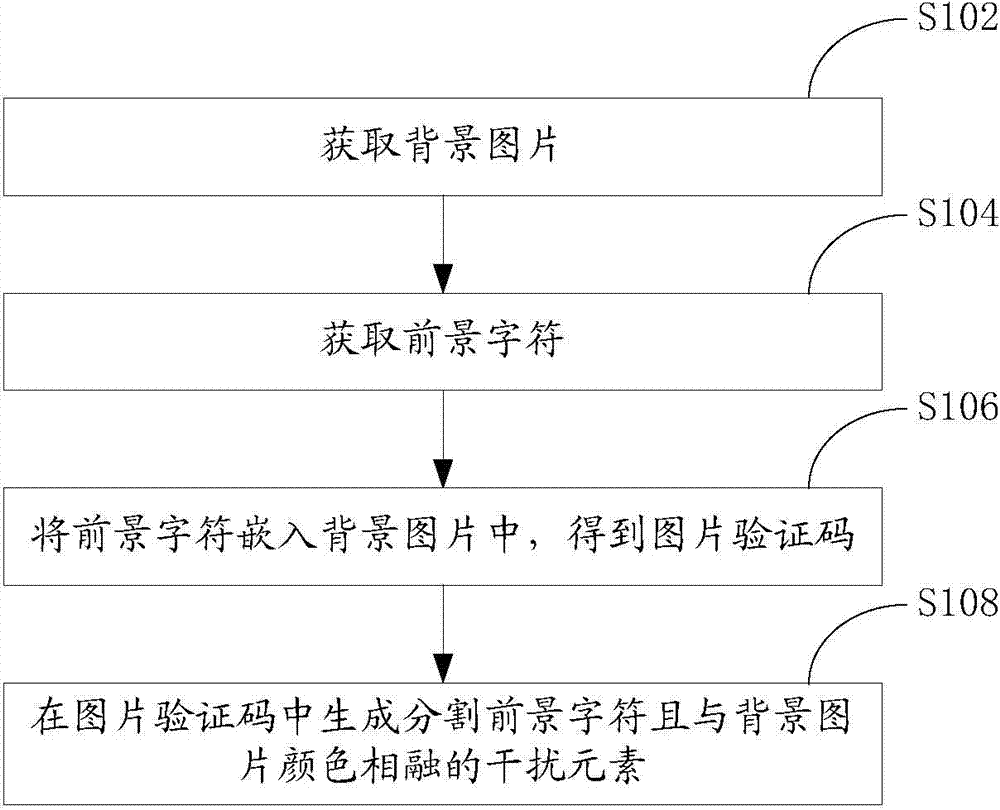
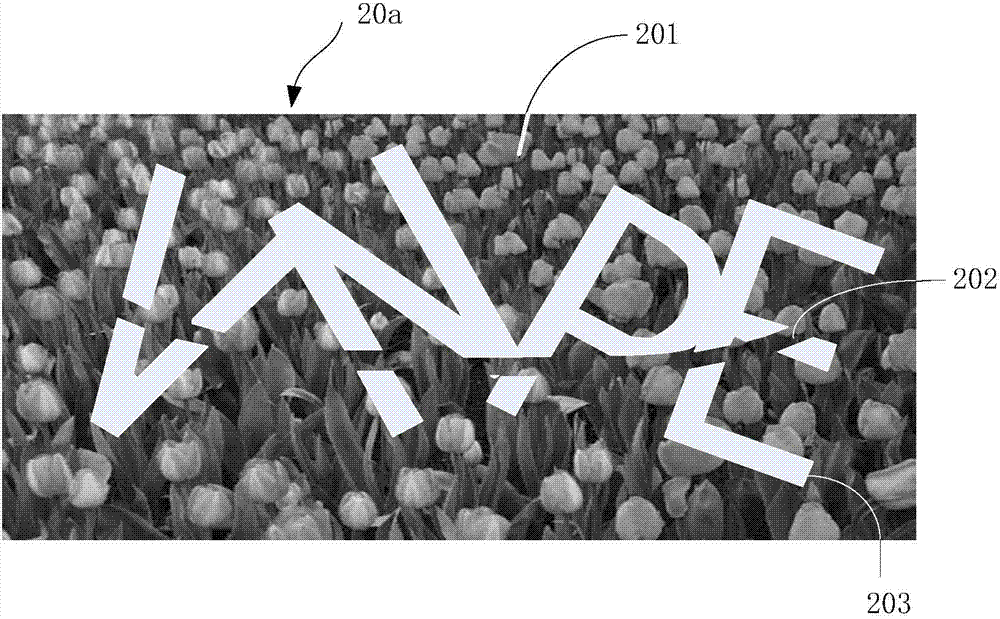
Picture identifying code generation method and system, and verify method and client side, and server
InactiveCN104852889AIncrease the difficultyDifficulty will not increaseUser identity/authority verificationImage data processing detailsComputer graphics (images)Validation methods
A picture identifying code generation method comprises the following steps: obtaining a background picture; obtaining foreground characters; embedding the foreground characters in the background picture so as to obtain a picture identifying code; generating interference element used for cutting the foreground characters and integrating with background picture color. The method uses the interference element integrating with the background picture color in the picture identifying code to cut the foreground characters, so an automatic machine can only extract foreground character fragments in the picture identifying code without extracting the whole foreground characters, thus increasing automatic machine difficulty of declassifying picture identifying code; the foreground characters are cut, yet a whole layout formed by the foreground character fragments allow the image identifying code to be easily recognized by a user, so the difficulty of the user identifying the picture identifying code is not increased; in addition, the invention also provides a picture identifying code generation system, a verify method based on the picture identifying code, a client side, and a server.
Owner:TENCENT TECH (SHENZHEN) CO LTD
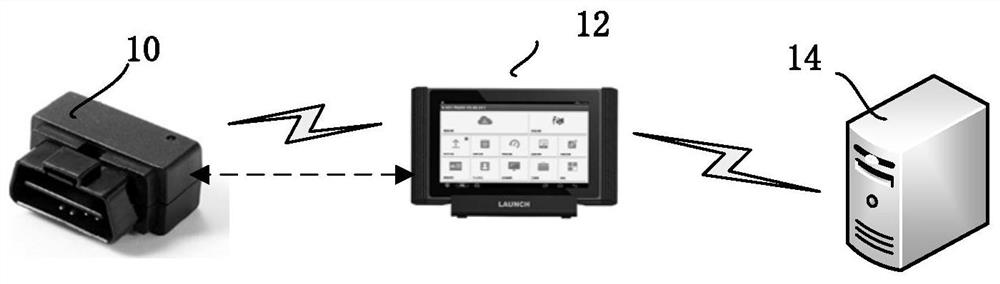
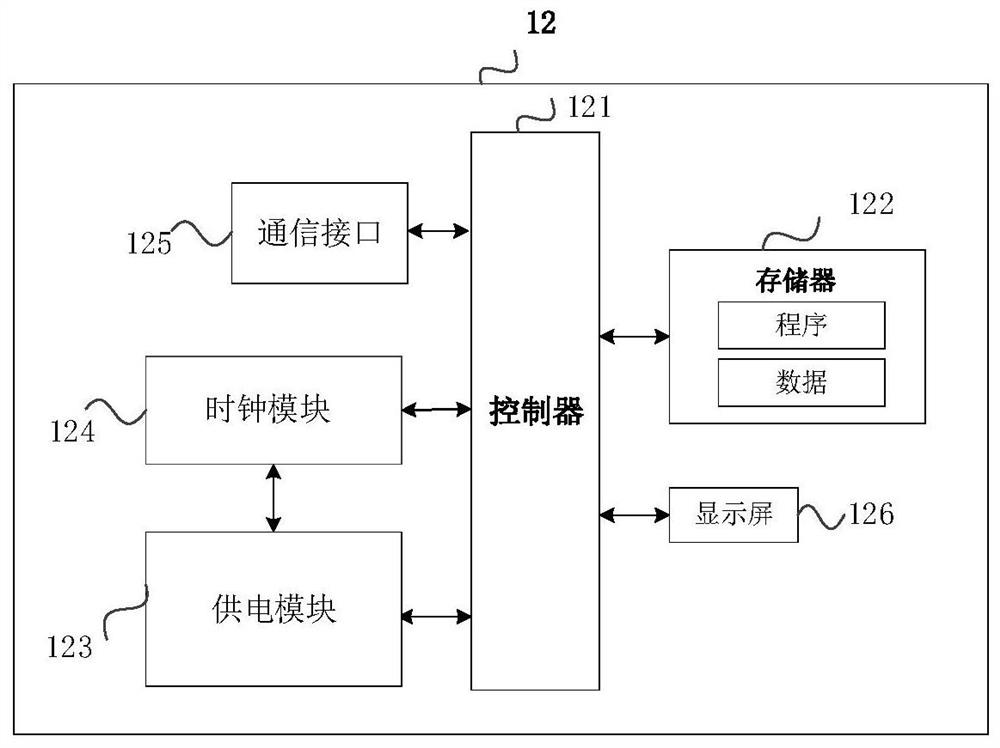
OBDII code reading card device and system and method for upgrading same
InactiveCN103577233AAchieve unlimited upgradesPrevent malicious crackingProgram loading/initiatingThird partySecurity validation
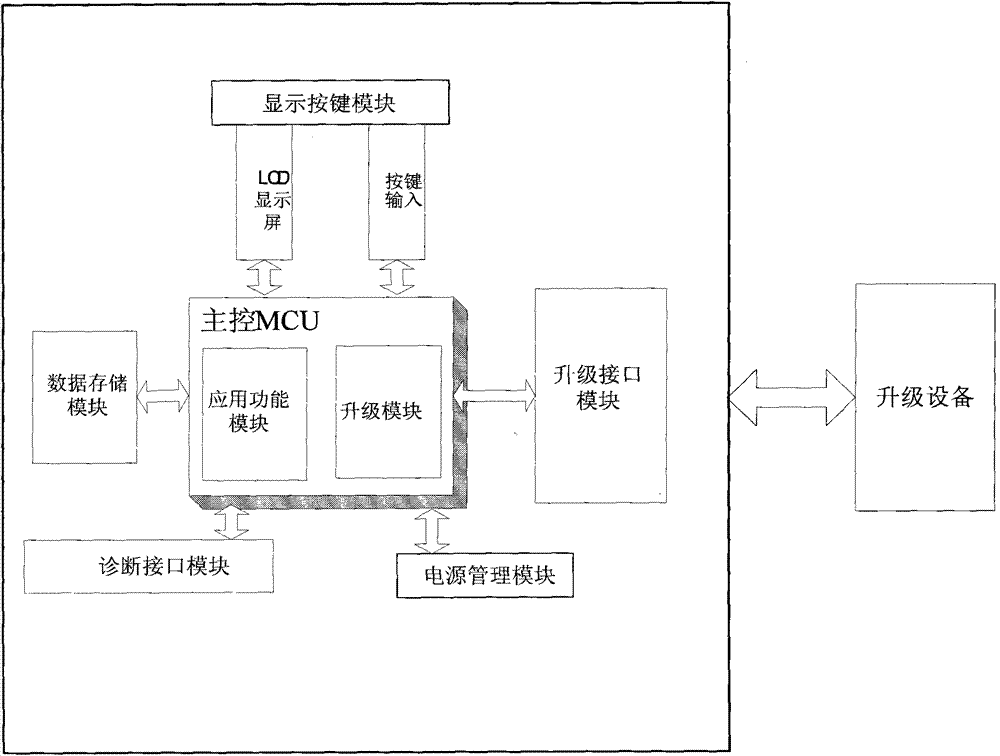
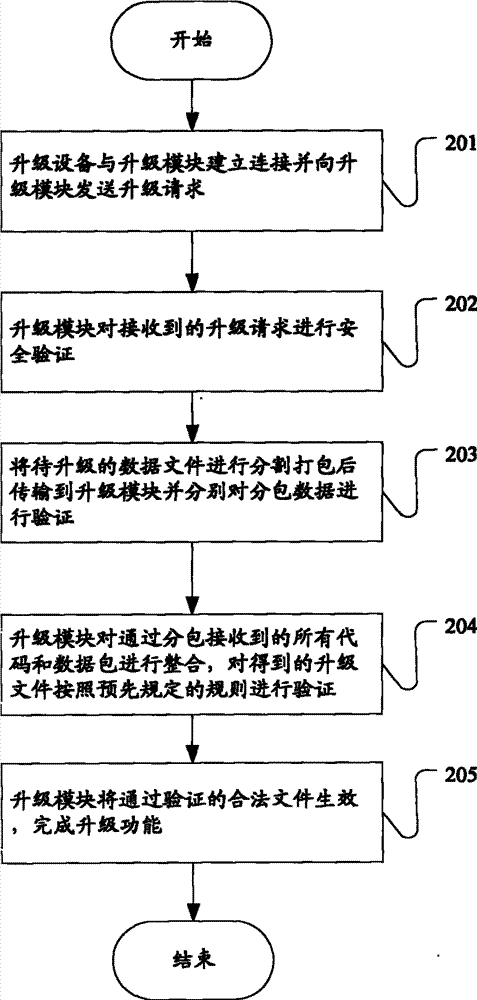
The invention provides an OBDII code reading card device and a system and method for upgrading the OBDII code reading card device. The device comprises a master control MCU, a data storage module, a display key module, a diagnosis interface module and a power management module, wherein the data storage module, the display key module, the diagnosis interface module and the power management module are connected with the master control MCU respectively. The master control MCU comprises an application function module and an upgrade module, wherein the upgrade module comprises an upgrade interface module and is used for providing interfaces for upgrading codes and data for the outside and providing interfaces for upgrading the data and the codes for the inside, and the application function module is used for achieving the diagnosis application function of an OBDII code reading card. By carrying out safety verification on a file to be upgraded, unlimited times of upgrade of the OBDII code reading card is achieved, timely upgrade of the product is guaranteed, the problem of abnormal upgrade caused by equipment exception, misoperation of a user and the like is also prevented, malicious cracking and interference of a third party on the upgrade process can be effectively prevented, and therefore the safety and security of the product are guaranteed.
Owner:LAUNCH TECH CO LTD
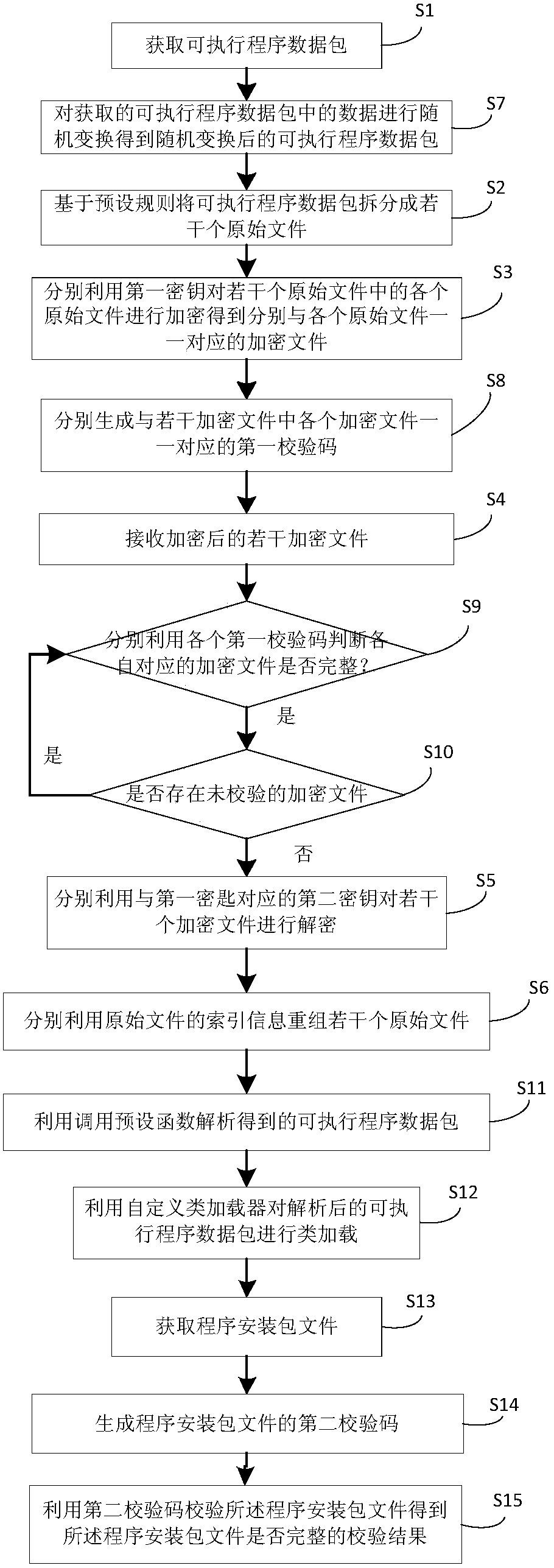
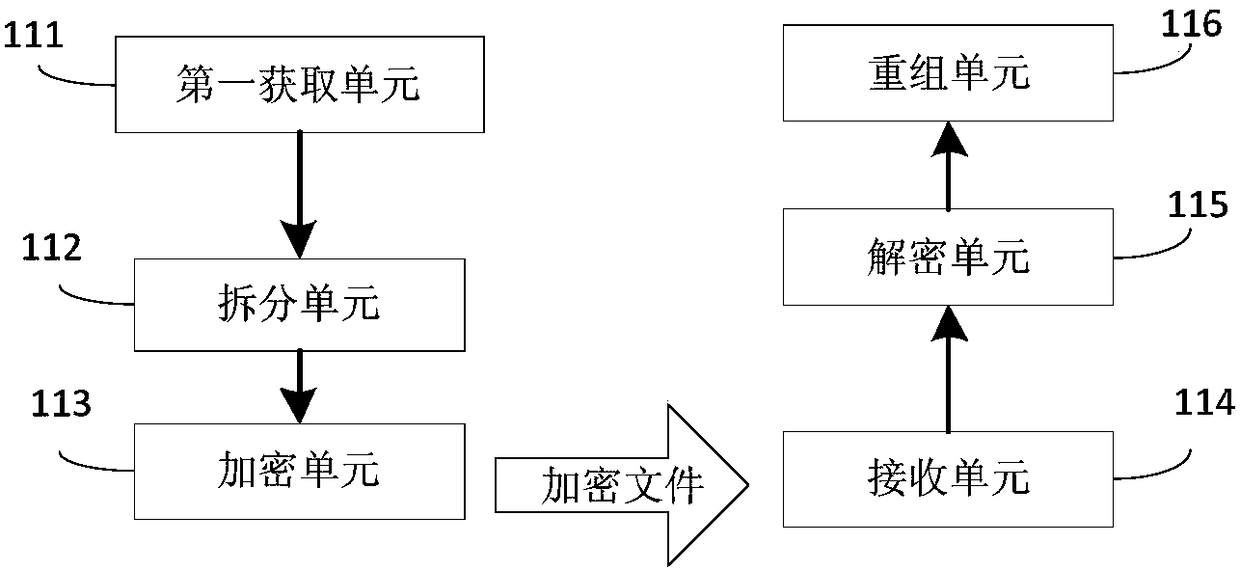
Method and device for encryption/decryption of executable program data package
ActiveCN106055936AGuaranteed confidentialityPrevent malicious crackingDigital data protectionProgram/content distribution protectionMultiple encryptionNetwork packet
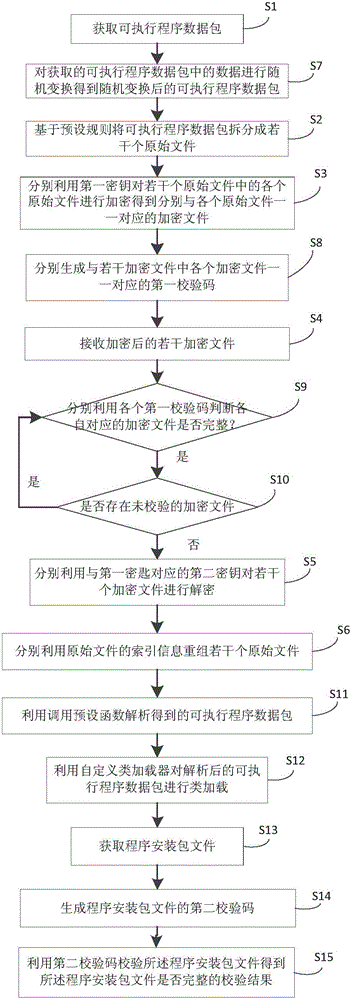
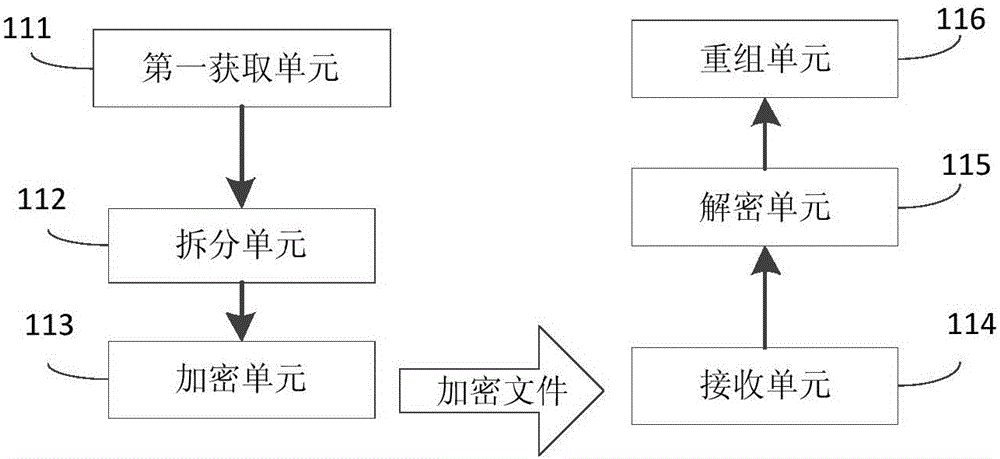
The invention provides a method and device for encryption / decryption of an executable program data package. The method comprises the steps that the executable program data package is acquired; based on preset rules, the executable program data package is divided into multiple original documents; a first secret key is used to encrypt the multiple original documents respectively, so that encryption documents which have one-to-one correspondence relations with each original document respectively can be obtained; the multiple encrypted encryption documents are received; a second secret key corresponding to the first secret key is used to decrypt the multiple encryption documents respectively, so that the multiple original documents which have the one-to-one correspondence relations with the encryption documents can be obtained; and index information of the original documents are used respectively to reform the multiple original documents, so that the executable program data package can be obtained. The method and the device provided by the invention have the advantages that vicious decryption of the executable program data package caused by theft of a single secret key in the executable program data package can be prevented; a probability of the vicious decryption of an application program can be reduced; and data safety of the application program can be enhanced.
Owner:SHENZHEN UNIV
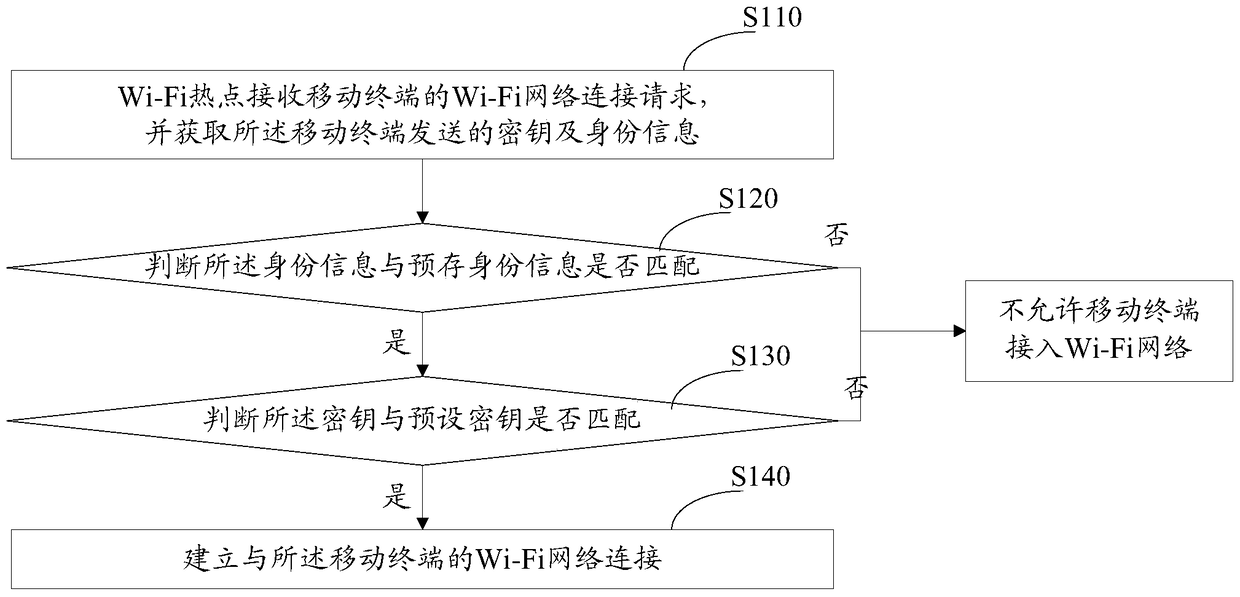
Connecting method and system for wireless fidelity network
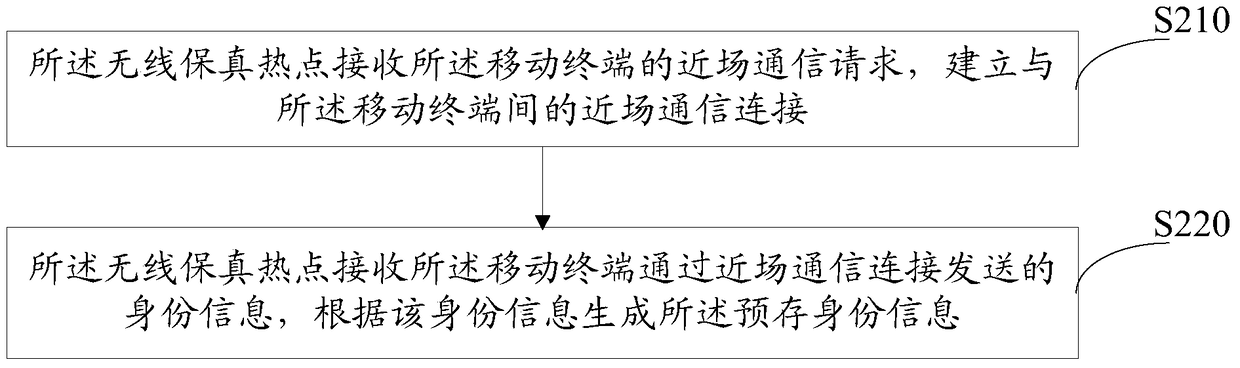
ActiveCN105072615AImprove securityImprove experienceConnection managementTransmissionWi-FiNetwork connection
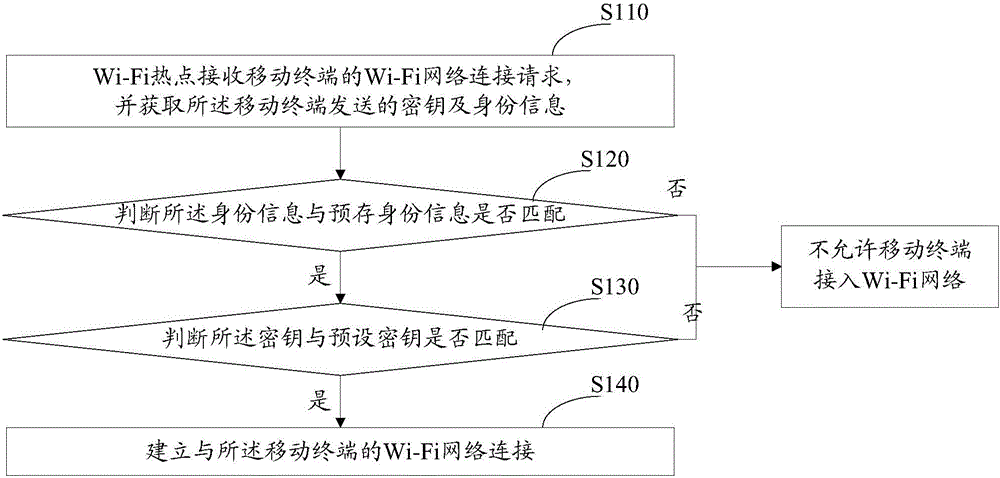
The invention relates to a connecting method and system for a wireless fidelity network. The method comprises the steps that a wireless fidelity hotspot receives a wireless fidelity network connecting request of a mobile terminal, and acquires a secret key and identity information sent by the mobile terminal; the wireless fidelity hotspot judges whether the identity information is matched with prestored identity information, and judges whether the secret key is matched with a prestored secret key; and if the identity information is matched with the prestored identity information, and the secret key is matched with the preset secret key, the wireless fidelity hotspot establishes a wireless fidelity network connection with the mobile terminal. Due to dual authentication mechanisms of identity information and secret key, the Wi-Fi network connection security is sharply improved, the Wi-Fi hotspot can be effectively prevented from being cracked maliciously, the data traffic of the user is prevented from being used maliciously, and the user experience is further improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
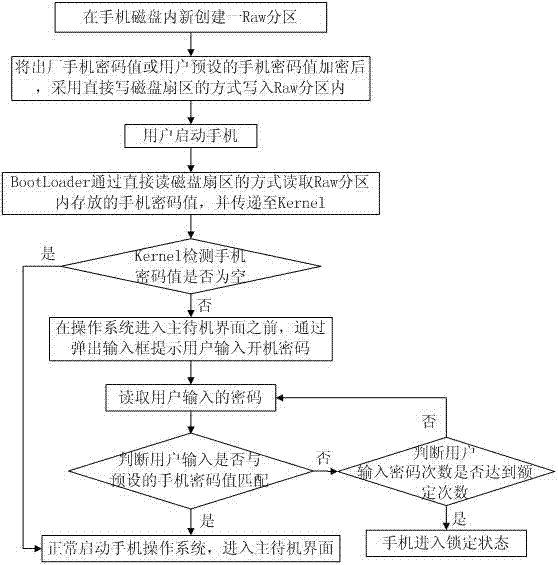
Cell phone password protection method based on Android system
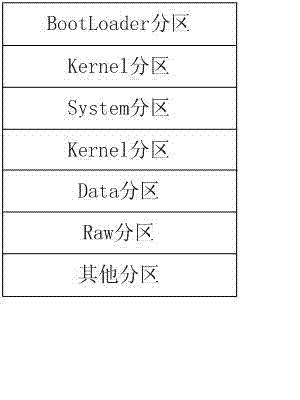
ActiveCN102970414APrevent malicious crackingImprove protection securityEncryption apparatus with shift registers/memoriesSubstation equipmentComputer hardwareOperational system
Provided is a cell phone password protection method based on an Android system. A cell phone disk comprises a guiding partition of a guiding loading program for loading an operation system, a system kernel partition containing an operation system kernel, a system partition and a user data partition. The method includes the steps that a password partition is built in the cell phone disk, and the password partition is an exposed partition independent from and different from the system partition and the user data partition; preset passwords are encrypted and written into a password partition through a method of writing a disk sector directly; when the cell phone operation system is started, the guiding loading program reads the cell phone passwords through a method of reading the disc sector directly, and the cell phone passwords are transmitted to the operation system kernel; and the operation system kernel matches passwords input by users with the preset cell phone passwords. The cell phone password protection method effectively achieves a purpose of preventing cracking of power-on passwords maliciously, cuts off a path for eliminating the power-on passwords maliciously, and improves information protection safety of a cell phone.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
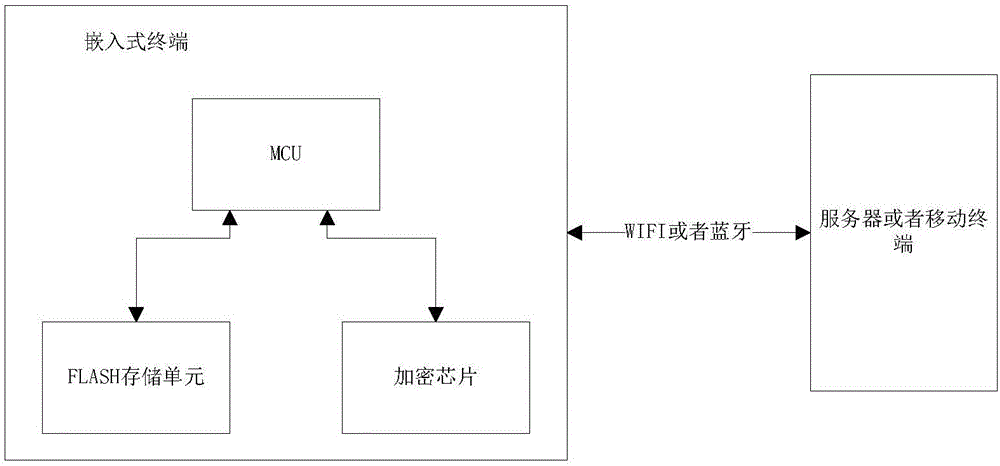
Software and hardware combination embedded terminal encryption system and encryption method
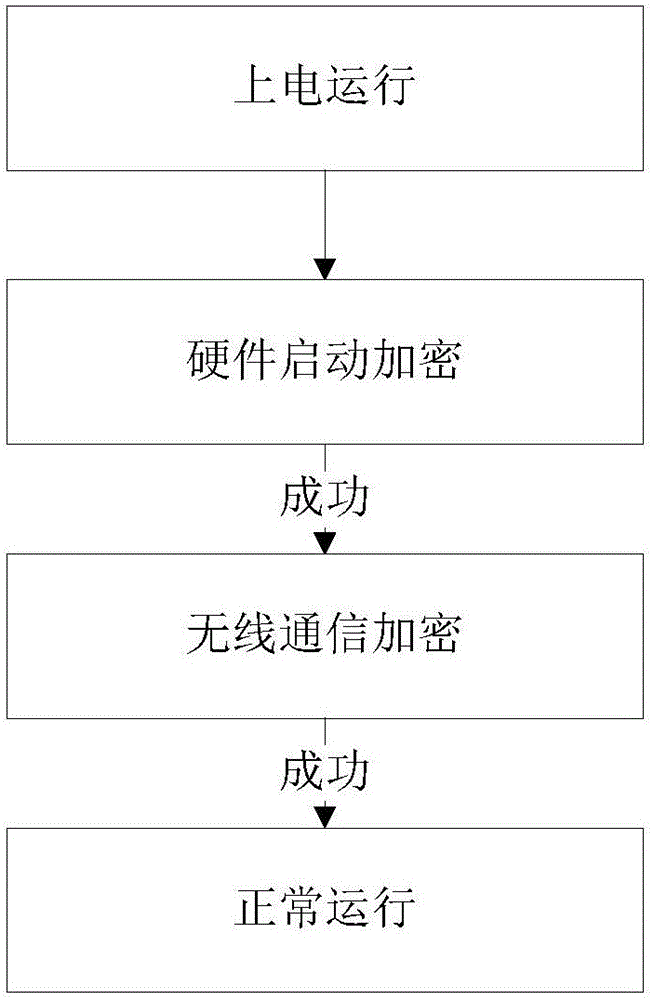
ActiveCN106507349AGuaranteed uptimeGuaranteed not to leakEncryption apparatus with shift registers/memoriesUser identity/authority verificationDisk encryptionSoftware
The invention discloses a software and hardware combination embedded terminal encryption system and an encryption method. The software and hardware combination embedded terminal encryption system comprises an embedded terminal communicating with a server or a mobile terminal, wherein the embedded terminal comprises an MCU; the MCU is connected with a FLASH storage unit and an encryption chip respectively and is used for transmitting data and command information; the FLASH storage unit is controlled by the MCU; the encryption chip is used for encryption operation and can select an encryption mode according to a control instruction of the MCU; when working, the embedded terminal firstly passes through hardware startup encryption verification, then passes through wireless communication encryption verification and finally operates normally; by the combination of hardware startup encryption and wireless communication encryption, encryption of the embedded terminal is realized; due to dual encryption and dual insurance, security and reliability of operation of the embedded terminal are guaranteed; meanwhile, competitors maliciously crack hardware equipment and embedded programs thereof are also effectively prevented; and non-disclosure of a technology is effectively guaranteed.
Owner:康威通信技术股份有限公司
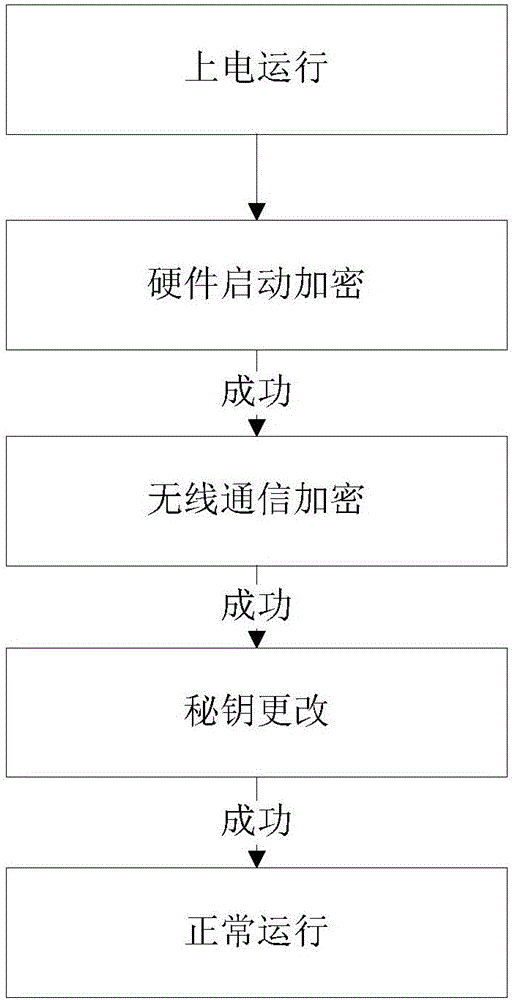
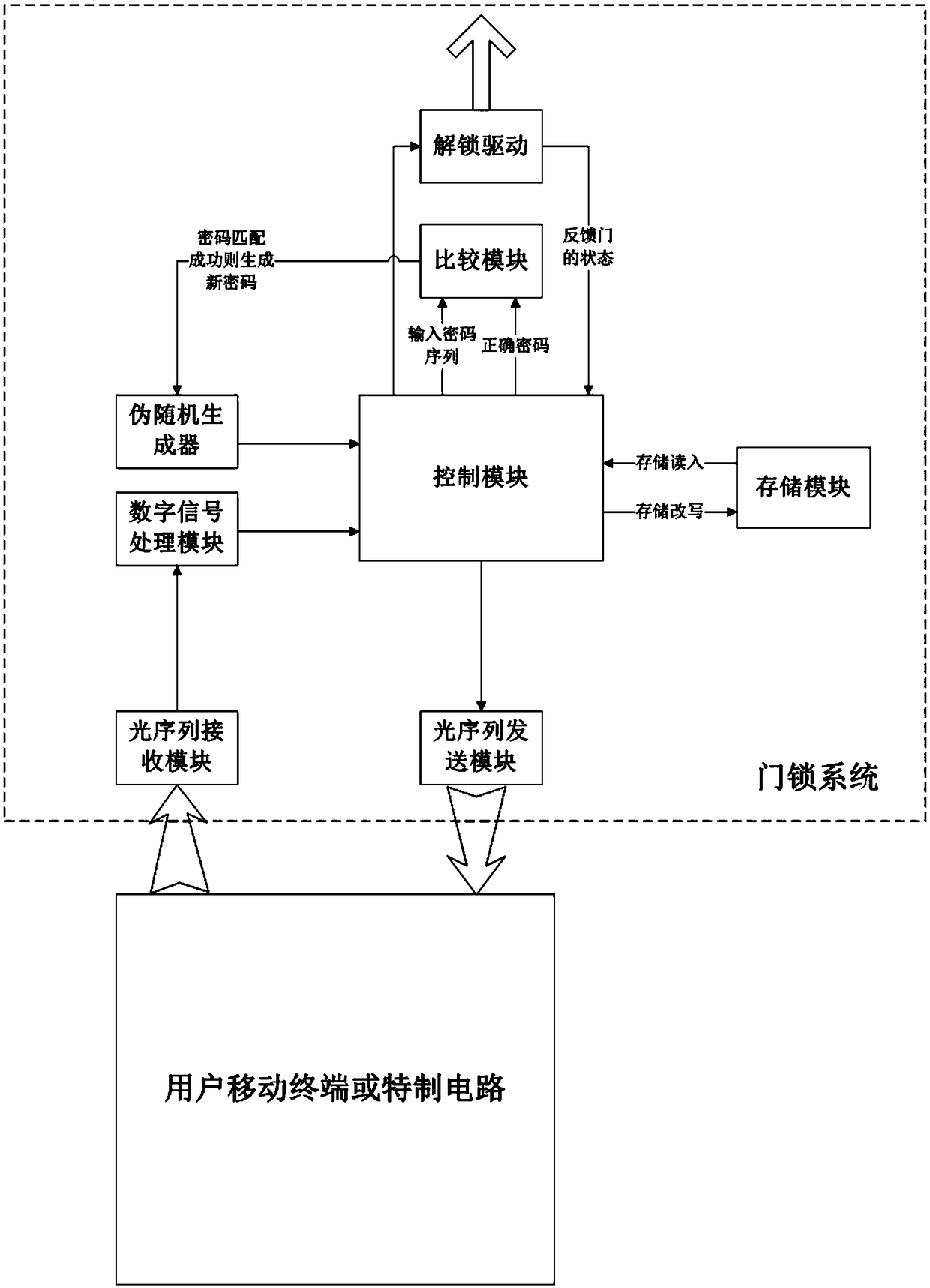
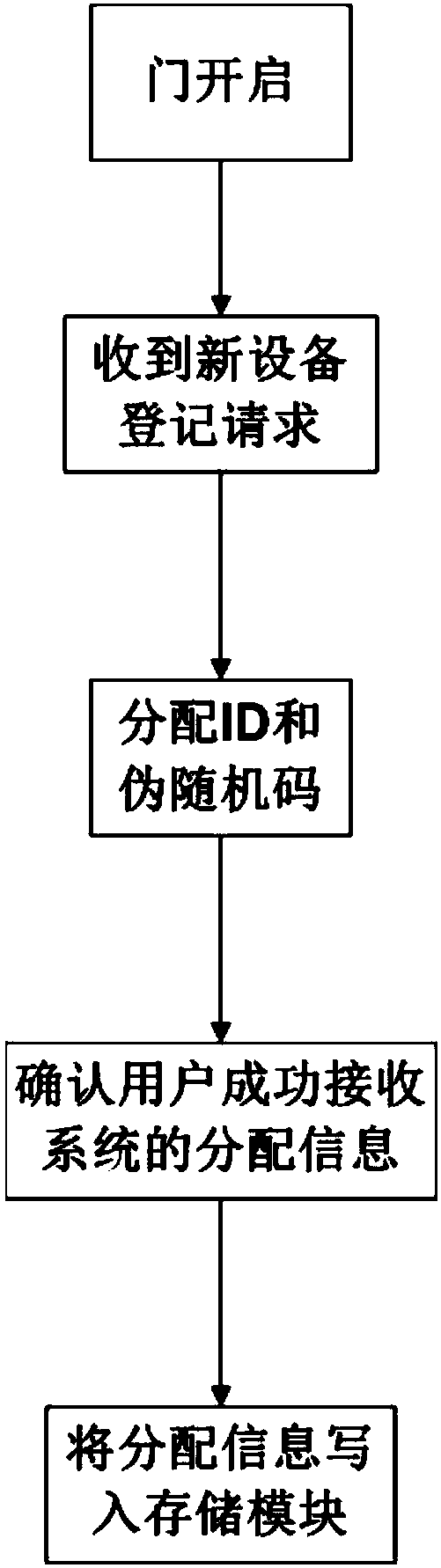
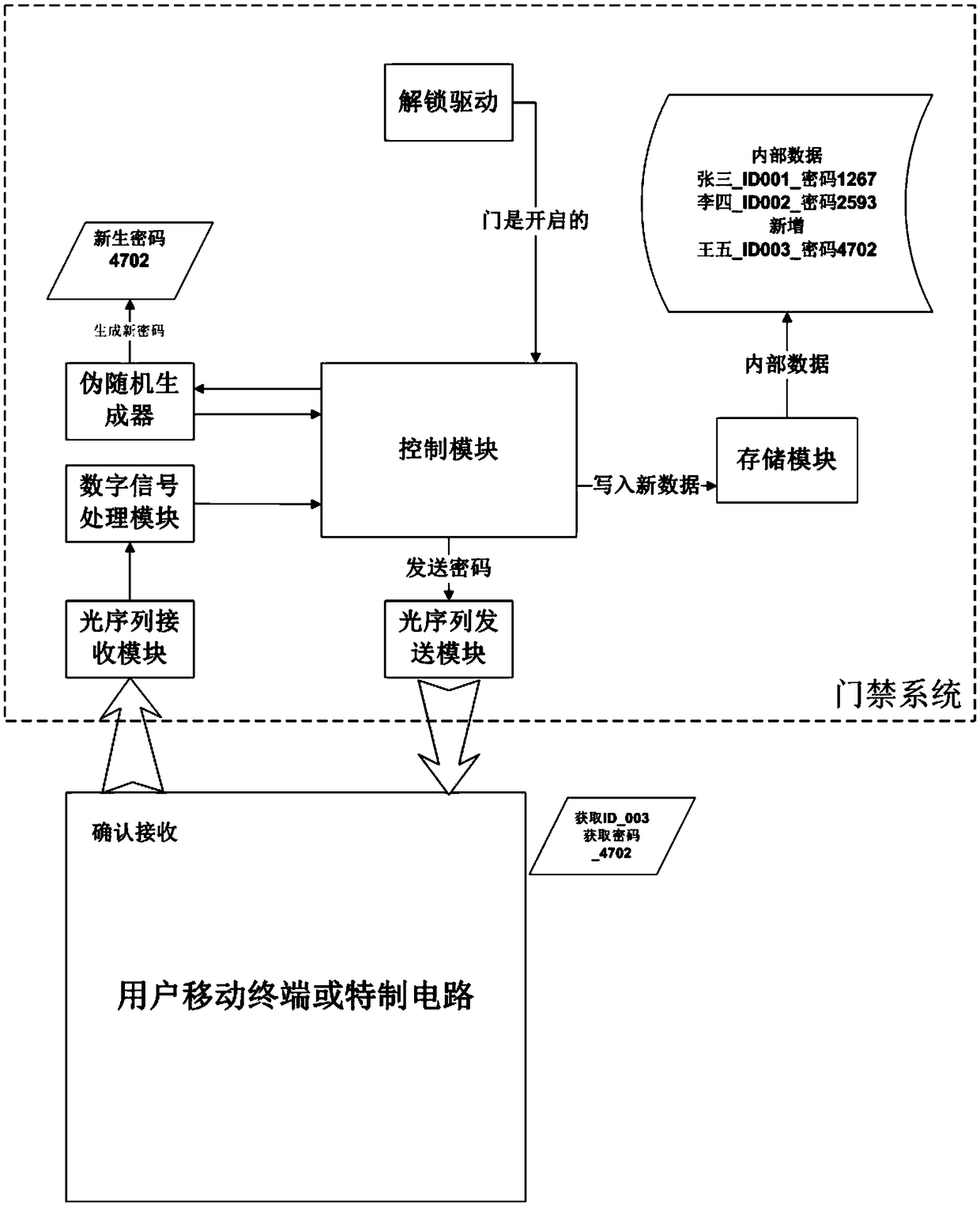
Dynamic password closed circuit access control system based on visible light communication
InactiveCN108520574AAchieve openImprove securityClose-range type systemsIndividual entry/exit registersDigital signal processingVisible light communication
The invention discloses a dynamic password closed circuit access control system based on visible light communication. The access control system comprises two parts of a door lock control system and akey unlocking system, wherein the door lock control system is composed of a visible light sequence receiving module, a visible light sequence sending module, a digital signal processing module, a first control module, a comparison module, a storage module, an unlocking driving module and a random number generation module; the key unlocking system is composed of a camera, a flash lamp and a secondcontrol module and also can be a mobile terminal with a camera and a flash lamp or a special key circuit. By means of the dynamic password closed circuit access control system, a user can flash towards a door to unlock the door through the mobile terminal or the special key; thus, convenience and quickness are achieved; meanwhile, malevolent unlocking is prevented.
Owner:NANJING UNIV OF POSTS & TELECOMM
Software anti-crack method and system
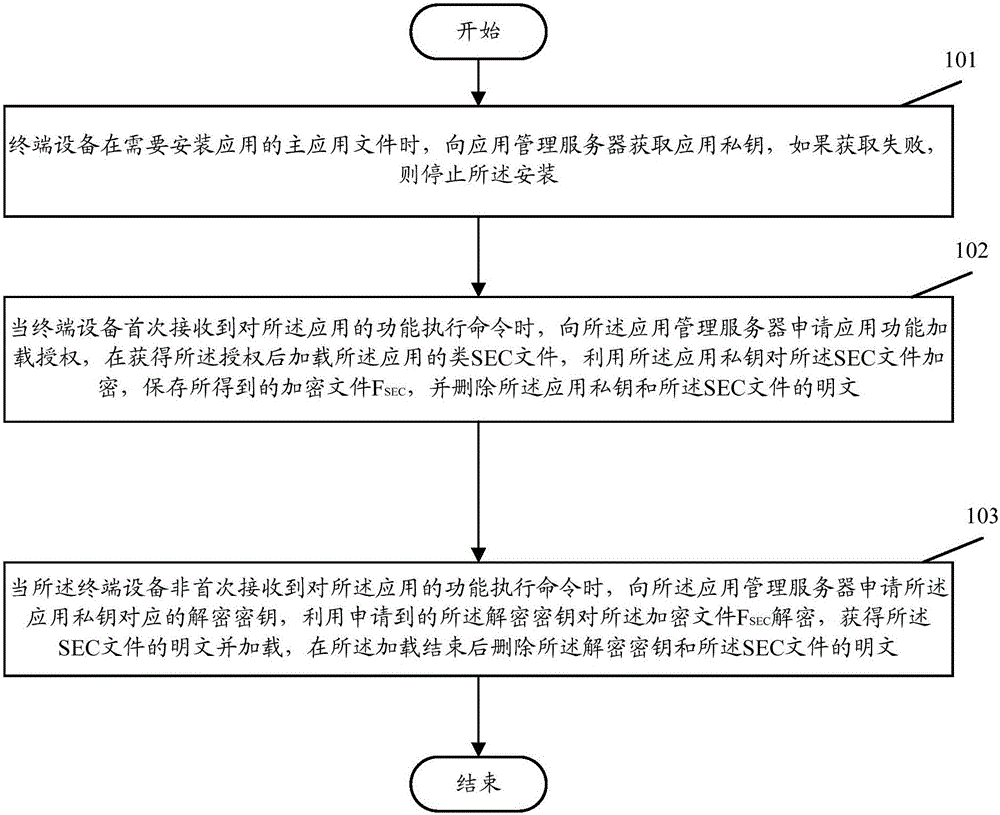
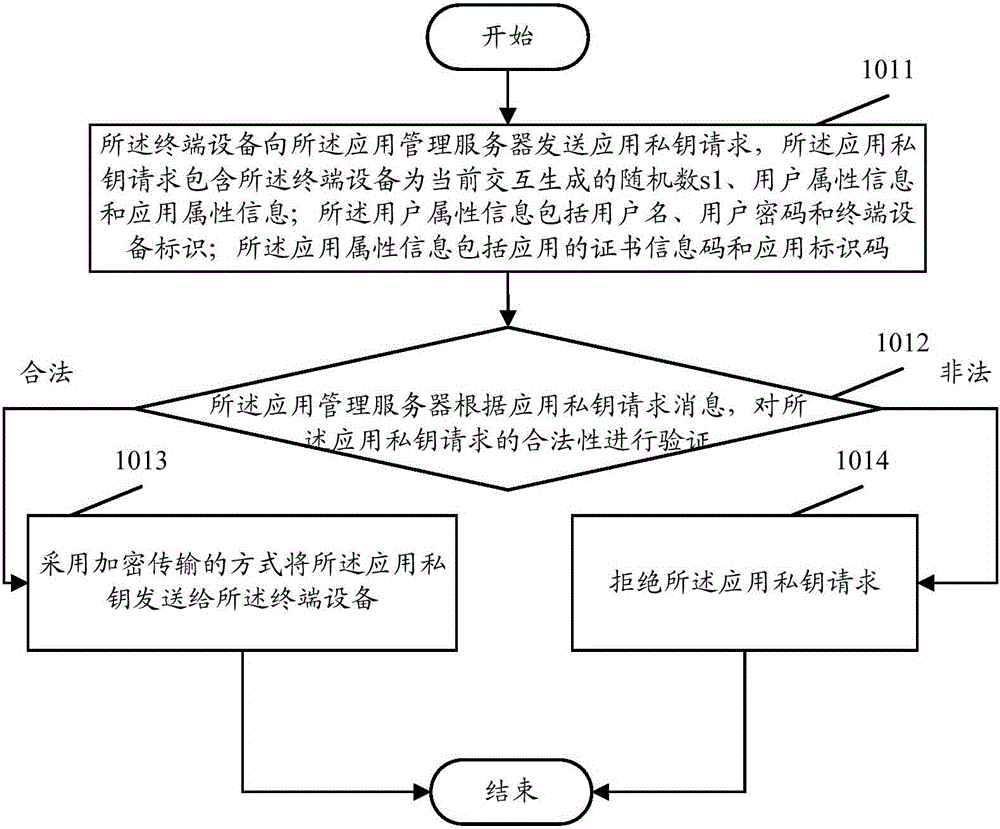
ActiveCN106096336APrevent malicious crackingKey distribution for secure communicationUser identity/authority verificationPlaintextTerminal equipment
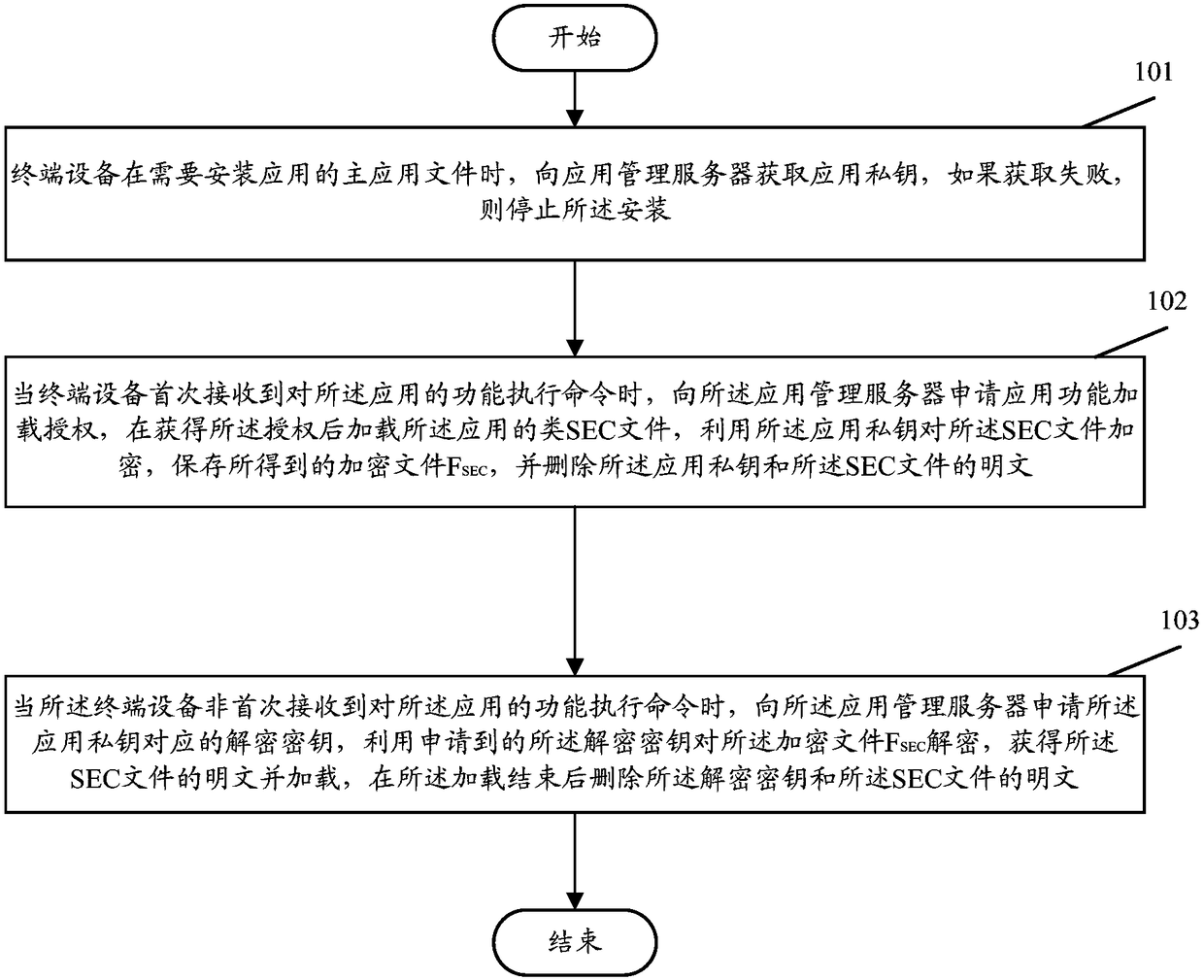
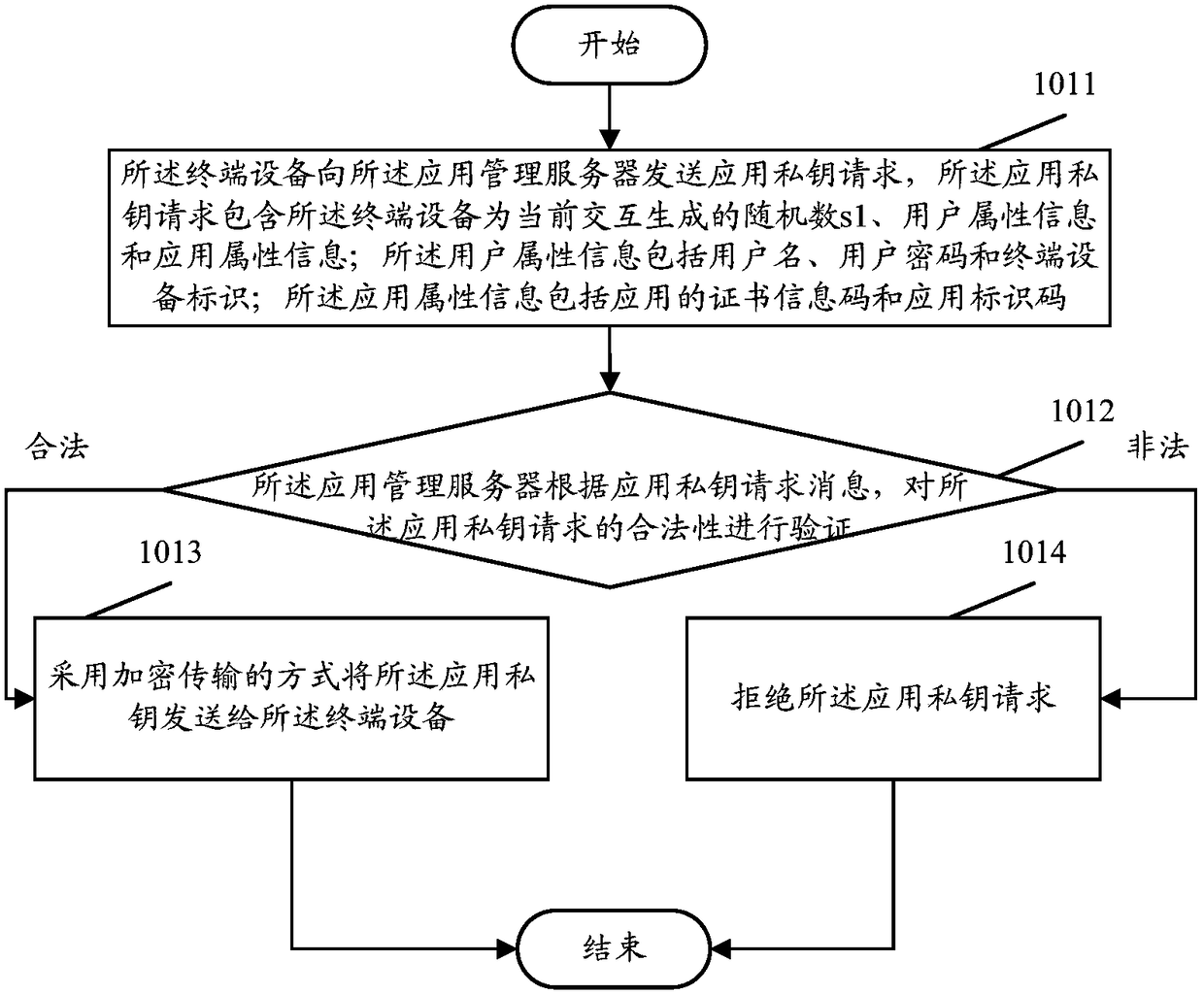
The invention discloses a software anti-crack method and system. The method comprises the steps that terminal equipment acquires an application private key from an application management server when the terminal equipment needs to install a main application file of an application, and if acquiring fails, installation is stopped; when the terminal equipment receives a function execution command to the application for the first time, the terminal equipment applies to the application management server for the application function load authorization, after the authorization is acquired, a class SEC file of the application is loaded, the SEC file is encrypted by means of the application private key, the acquired encrypted file F[SEC] is saved, and the application private key and a plaintext of the SEC file are deleted; when the terminal equipment receives the function execution command to the application not for the first time, the terminal equipment applies to the application management server for a decryption key corresponding to the application private key, the applied decryption key is utilized for decrypting the encrypted file F[SEC], the plaintext of the SEC file is acquired and loaded, and after loading is finished, the decryption key and the plaintext of the SEC file are deleted. By means of the software anti-crack method and system, the software can be effectively prevented from being cracked maliciously.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Method and system for realizing password retrieval based on multiple safety verification ways
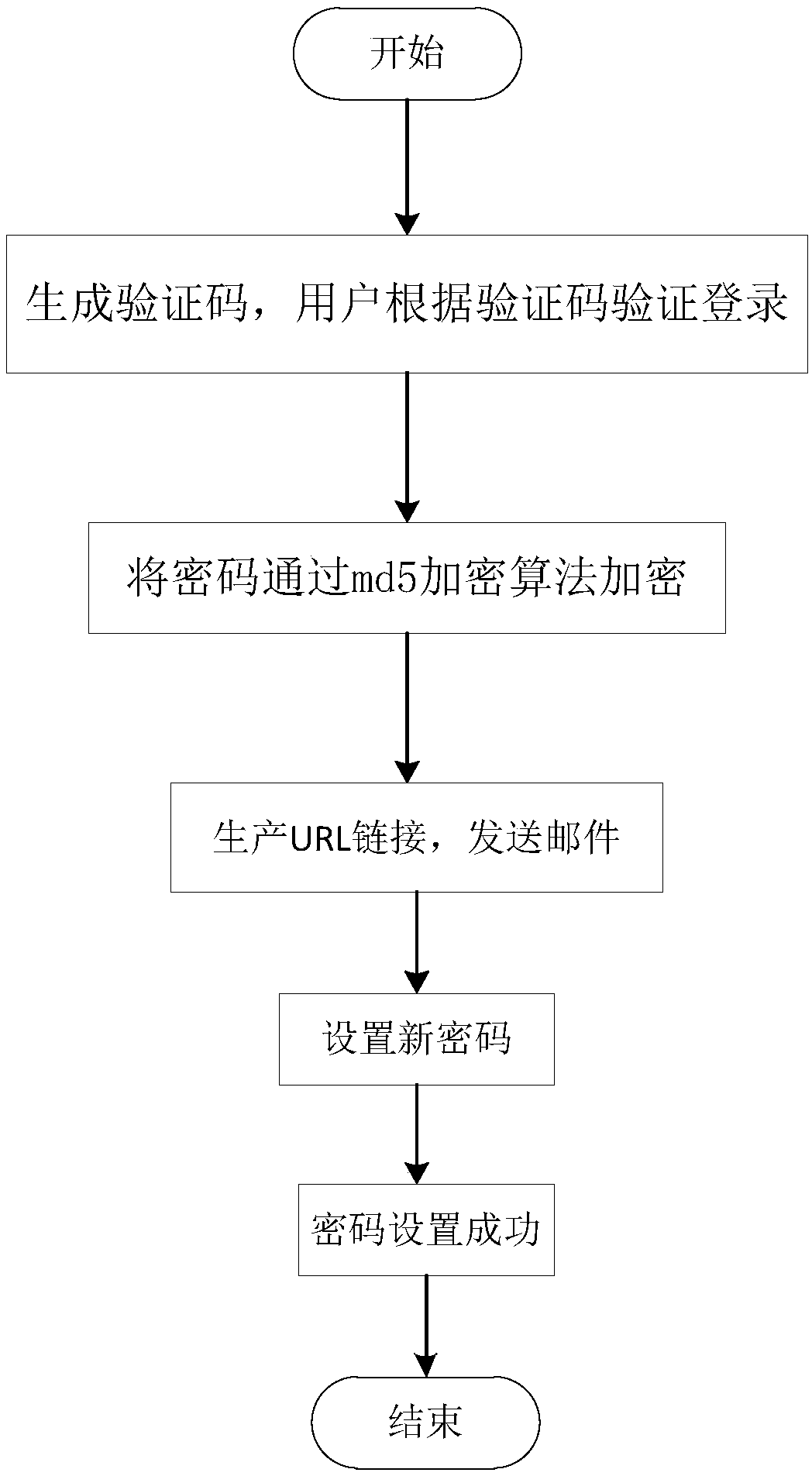
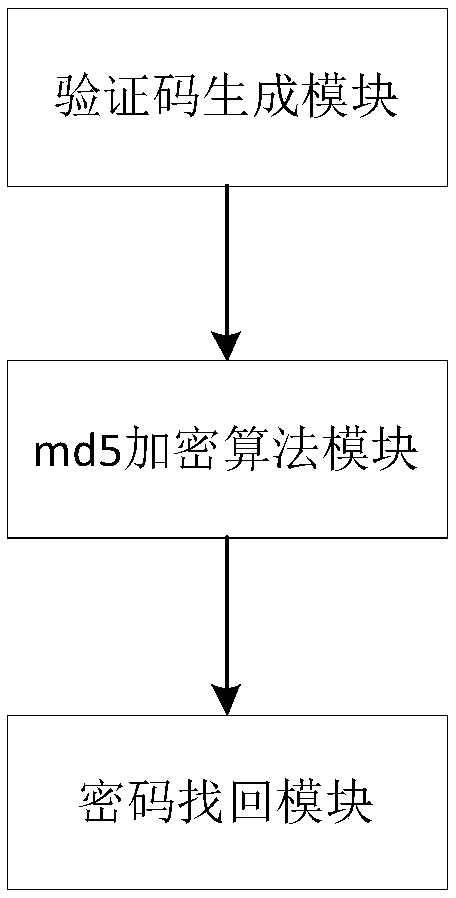
InactiveCN109462620AEnsure safetyPrevent from being stolenKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordCiphertext
The invention discloses a method and system for realizing password retrieval based on multiple safety verification ways, and belongs to the field of the user password verification and password retrieval. A to-be-solved technical problem is how to guarantee the account and data safety better, and an adopted technical scheme is as follows: (1) a method for realizing password retrieval based on multiple safety verification ways mainly comprises the following steps: S1, generating a verification code, and verifying login by a user according to the verification code; S2, encrypting the password through a md5 encryption algorithm, and adding the verification code at the end, encrypting by reusing the md5 encryption algorithm, and transmitting to a background database in a ciphertext way in the network transmission process; and S3, retrieving the password according to a mailbox; (2) a system for realizing password retrieval based on multiple safety verification ways comprises a verification code generation module, a md5 encyrption algorithm module and a password retrieval module, wherein the verification code production module is used for producing the verification code so that the user can verify the login according to the verification code.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
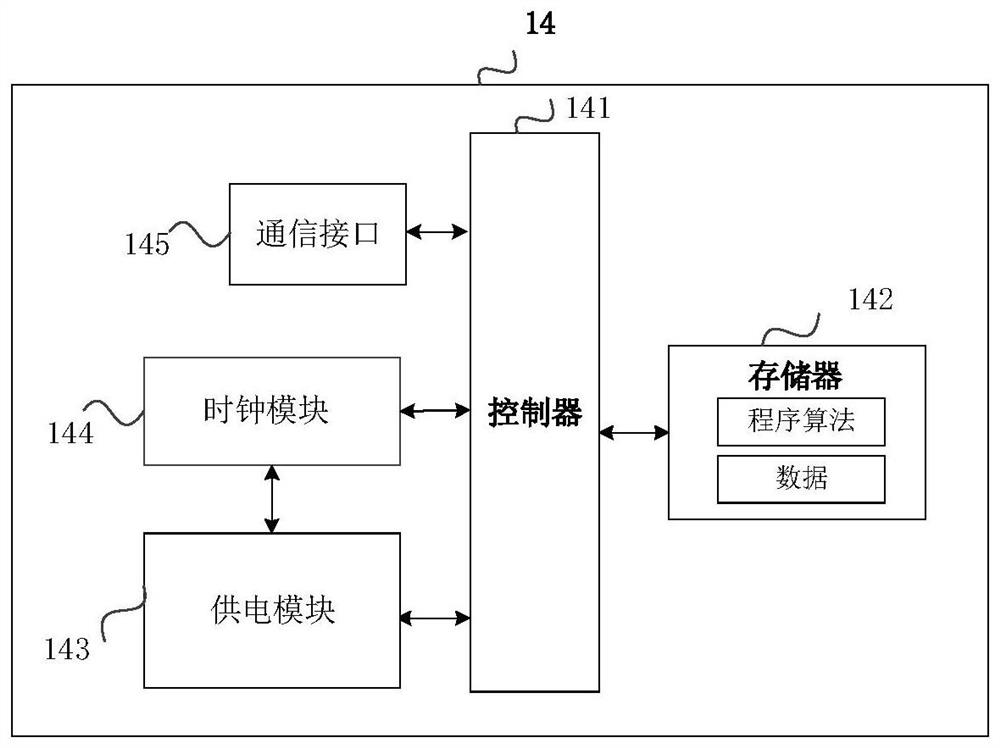
Automobile data diagnosis method and device
ActiveCN110989564APrevent malicious crackingAvoid using effectsProgramme controlElectric testing/monitoringDiagnosis methodsComputer science
The application discloses an automobile data diagnosis method and device. The method comprises the following steps: receiving an access request that is sent by diagnosis equipment and comprises a first digital digest obtained by performing hash operation on to-be-processed data, a joint serial number and an equipment ID of the diagnosis equipment, the joint serial number and the to-be-processed data including vehicle data and indication information for indicating at least one request algorithm; judging whether the equipment ID is legal or not according to the access request; judging whether the access request conforms to a preset strategy or not under the condition that the equipment ID is judged to be legal; processing the vehicle data by using at least one request algorithm to obtain a diagnosis result under the condition of judging that the access request conforms to the preset strategy; and sending the diagnosis result to the diagnosis equipment. According to the invention, the algorithm for diagnosing the automobile data can be prevented from being maliciously cracked and illegally used, and the safety diagnosis of the automobile data is realized.
Owner:LAUNCH TECH CO LTD
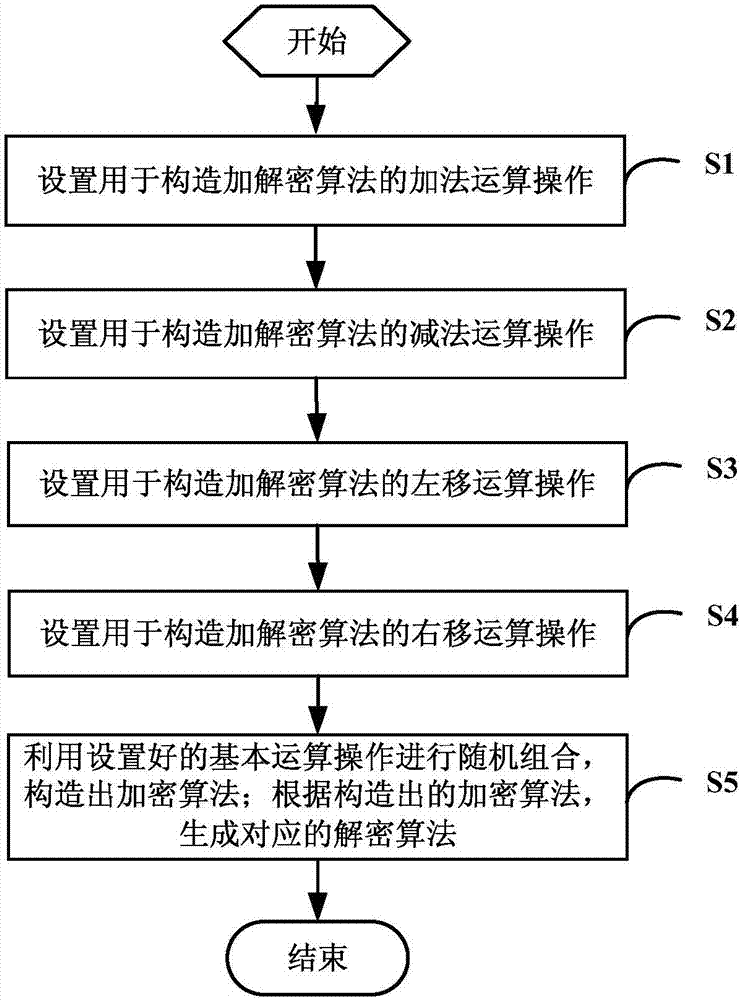
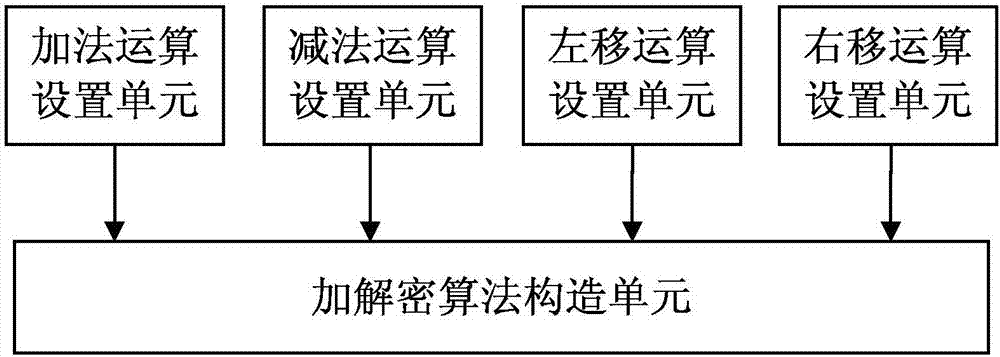
Method and system for constructing data encryption and decryption algorithm based on ARM instruction
ActiveCN106921482APrevent malicious crackingImprove securityCryptographic attack countermeasuresComputer hardwareAlgorithm
The invention discloses a method and system for constructing a data encryption and decryption algorithm based on an ARM instruction, and relates to the technical field of data encryption and decryption. The method comprises the following steps: setting an addition operation, wherein the addition operation is used for realizing addition operation based on the ARM instruction; setting a subtraction operation, wherein the subtraction operation is used for realizing subtraction operation based on the ARM instruction; setting a left shift operation, wherein the left shift operation is used for realizing a data logic left shift operation based on the ARM instruction; setting a right shift operation, wherein the right shift operation is used for realizing a data logic right shift operation based on the ARM instruction; and randomly combining the set basic operations to construct the data encryption and decryption algorithm based on the ARM instruction. By adoption of the method and system disclosed by the invention, the data encryption and decryption algorithm can be effectively prevented from being maliciously cracked, and the security of data encryption and decryption is improved.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
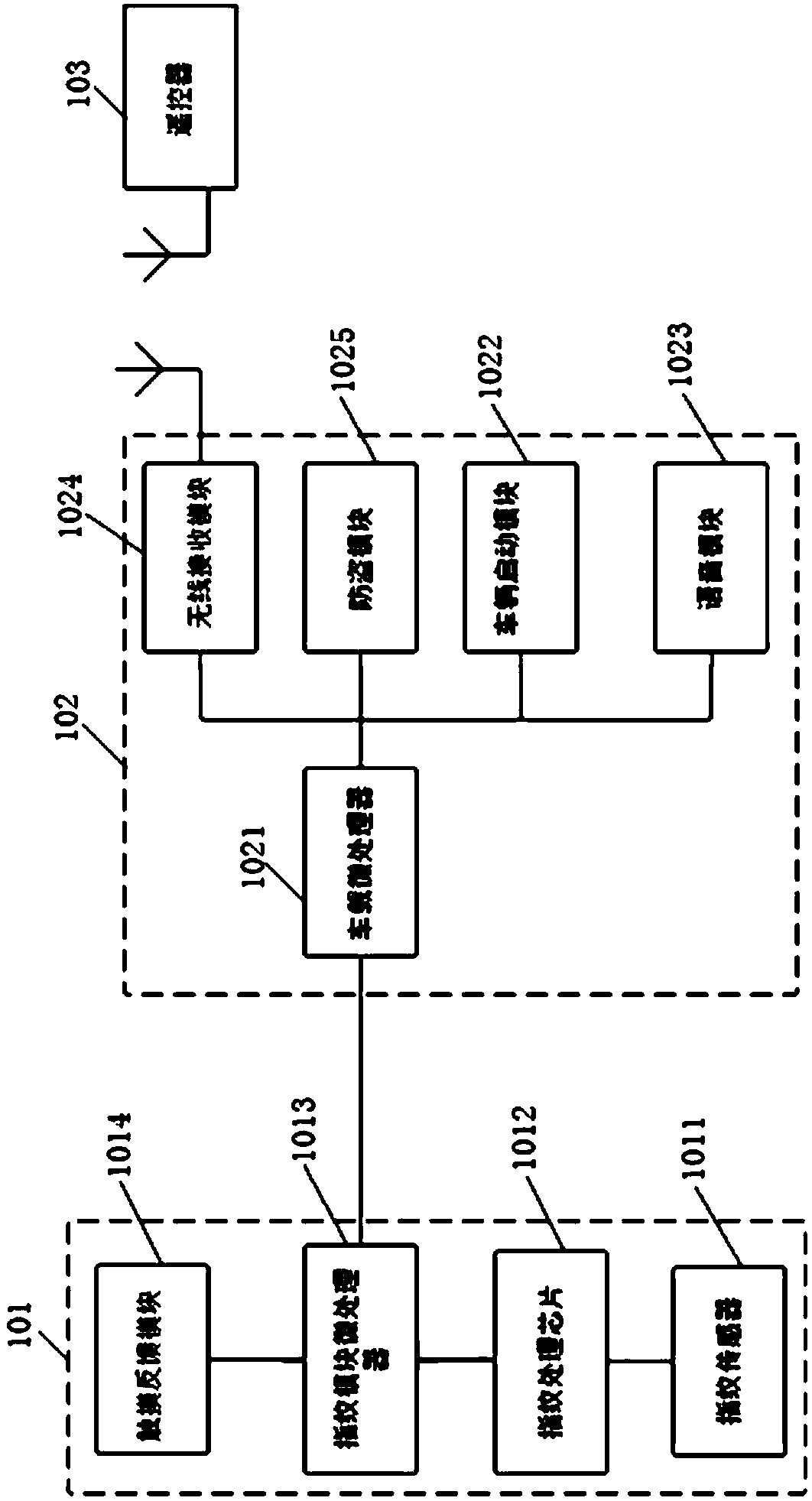
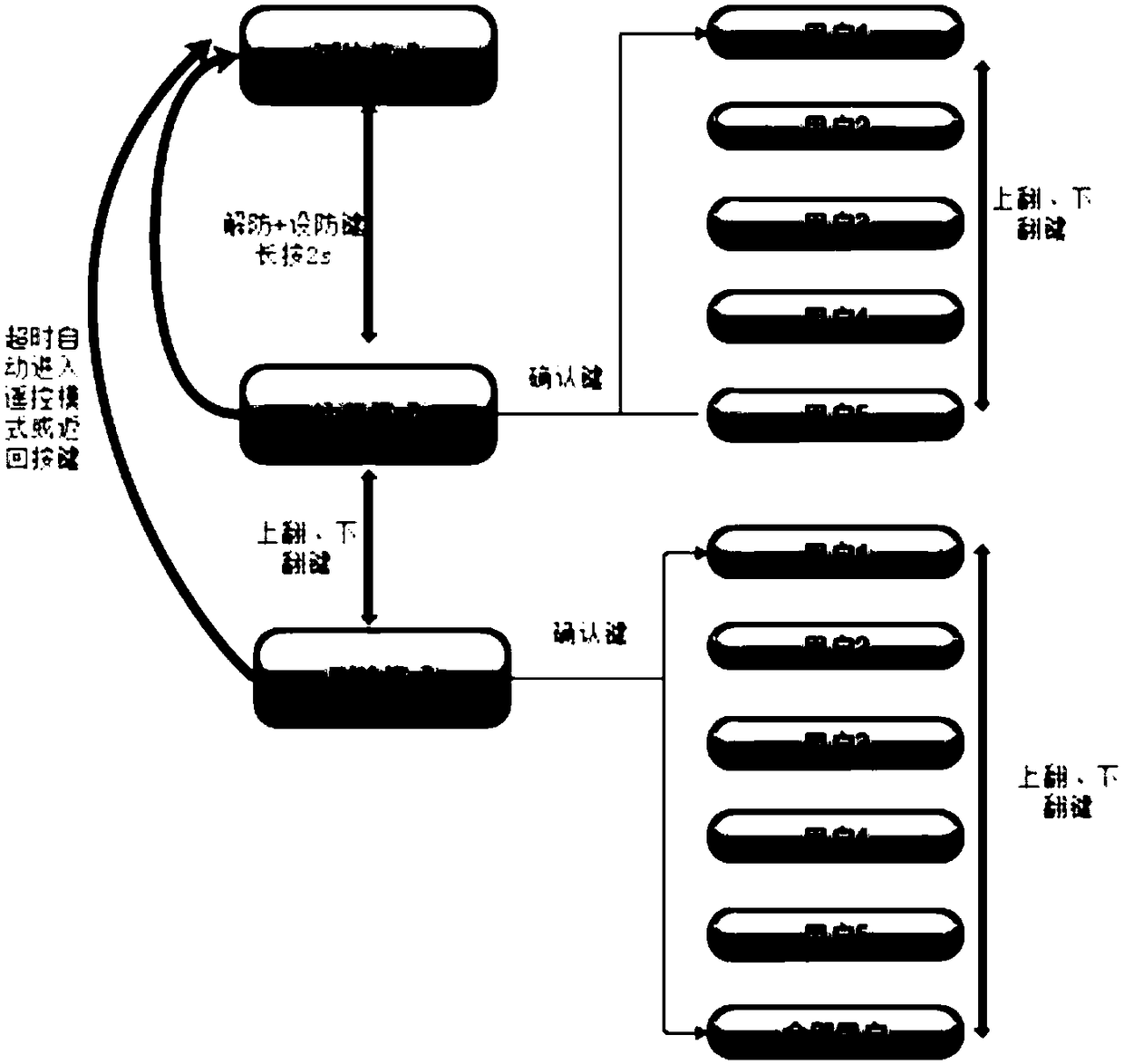
An electric vehicle fingerprint identification intelligent anti-theft system
InactiveCN108974192AImprove securityPrevent illegal managementAnti-theft cycle devicesAnti-theft devicesKey pressingComputer module
The invention discloses an electric vehicle fingerprint identification intelligent anti-theft system. The system uses the feature point information, the vector field information and the fingerprint texture information of the fingerprint image to carry out multi-feature point fusion matching, which greatly reduces the false recognition caused by the false features in the fingerprint identificationmatching process, and enhances the safety of the electric vehicle fingerprint identification. Anti-cracking security mechanism is added to that identification matching process, when the number of times of continuous identification of the matching failure exceed a set value, the fingerprint identification is refused again, and the malicious cracking is effectively prevented; Fingerprint identification module with identification feedback function can give users more intuitive fingerprint identification feedback; The fingerprint management is carried out by using the virtual menu composed of thelogic operation of the traditional remote controller keys or the physical switch on the whole vehicle and the phonetic system, without adding additional visual equipment and input keys, which is simple, easy to use and low in cost. Virtual menu access must be authorized by the first administrator to access, effectively prevent the illegal management of fingerprints.
Owner:YADEA TECH GRP CO LTD
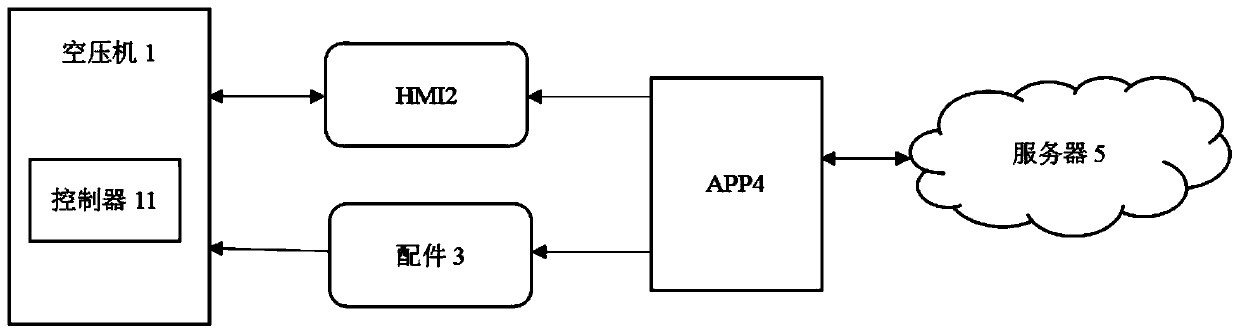
Electromechanical equipment original factory accessory verification method based on cloud computing
PendingCN110490338ASolve the problem of easily being replaced maliciouslyTroubleshooting the presence of good and bad accessoriesKey distribution for secure communicationUser identity/authority verificationThird partySafe operation
The invention discloses an electromechanical equipment original factory accessory verification method based on cloud computing, and the method comprises the following steps: adding an accessory verification algorithm and an accessory-related flag bit to a controller used in electromechanical equipment when the controller leaves a factory, and the controller being connected with an HMI in a wired manner; establishing a plurality of sign accessories effective days in the controller, and storing the sign accessories effective days in the controller; when the accessories are replaced, using a mobile phone APP for scanning bar codes on the accessories and then uploading the bar codes to a server through a network, and the controller monitoring the state of each accessory at set intervals; the server performing database verification according to the SN code uploaded by the APP; and the controller analyzing the input serial number in a normal working state. According to the method, maliciousreplacement of inferior third-party accessories, accessory applicability, accessory quality and safe operation of electromechanical equipment can be guaranteed, and the problems that accessories are unqualified, the quality cannot be guaranteed and potential safety hazards exist when third-party accessories of existing electromechanical equipment are maliciously replaced are solved.
Owner:广东蘑菇物联科技有限公司
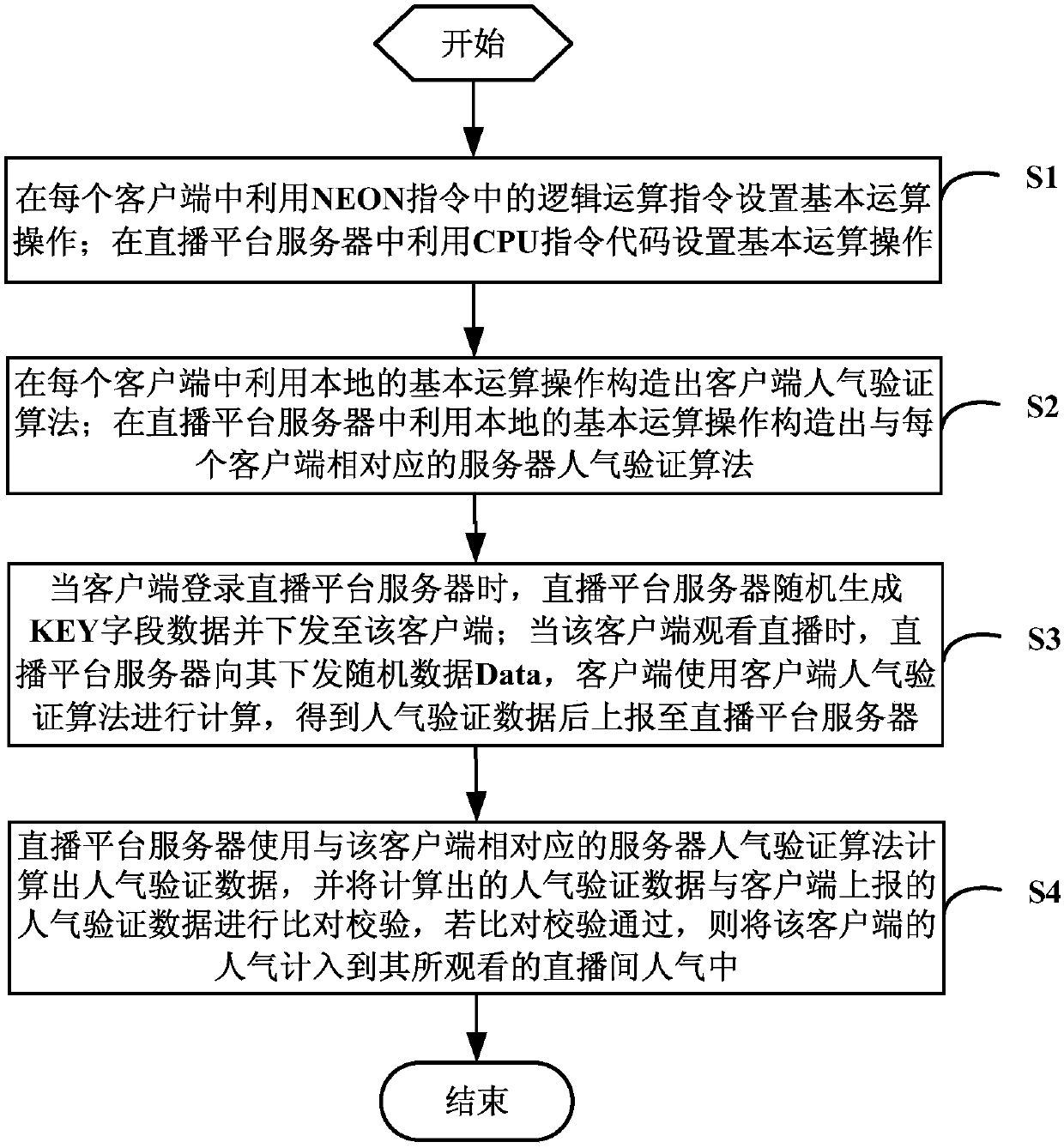
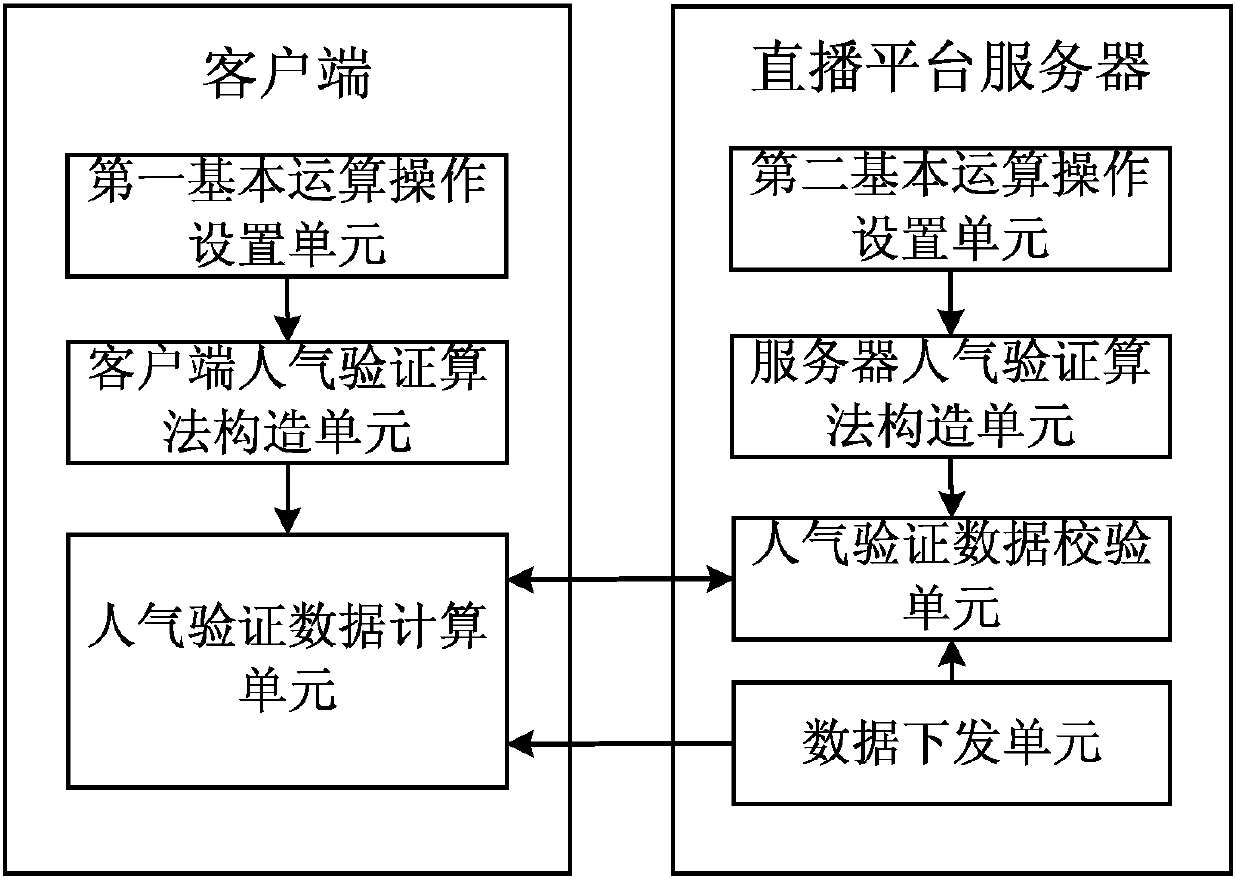
Method, equipment and system for preventing refreshing popularity, and storage medium
ActiveCN108282665APopularity is fairPopularity is reliableSelective content distributionInformation processingPersonal computer
The invention discloses a method, equipment and system for preventing refreshing popularity, and a storage medium, and relates to the technical field of information processing. The method comprises the following steps: using an NEON instruction to set a basic operation and constructing a client popularity verification algorithm in a client; using a CPU instruction code to set the basic operation and constructing a server popularity verification algorithm corresponding to each client in a live broadcast platform server; when the client watches the live broadcast, using the client popularity verification algorithm to calculate popularity verification data and reporting the popularity verification data; and using the server popularity verification algorithm corresponding to the client to calculate the popularity verification data by the live broadcast platform server, comparing the popularity verification data with data reported by the client, and if the comparison is passed, then counting the popularity of the client in the popularity of a watched live broadcast room. The method for preventing refreshing the popularity provided by the invention can effectively prevent a hacker from cracking the popularity verification algorithm through a PC (Personal Computer) client or a PC server, thereby effectively preventing the hacker from maliciously refreshing up the popularity of the live broadcast room.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
File protection method and device
PendingCN112532379AIncrease randomnessPrevent malicious crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringDatabase
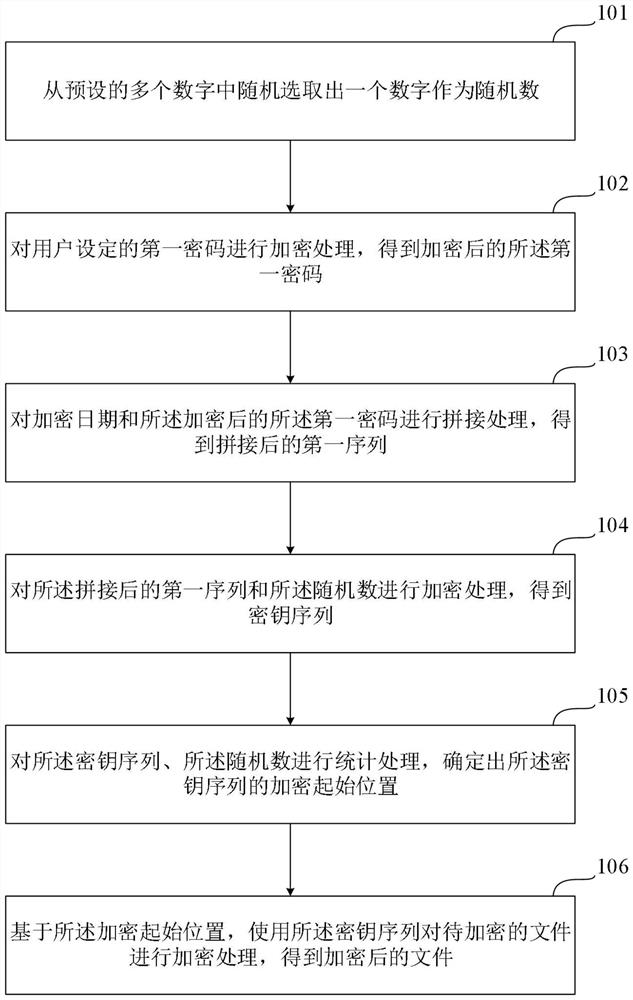
An embodiment of the invention provides a file protection method and device. The file protection method comprises the steps of randomly selecting one number from a plurality of preset numbers as a random number, carrying out the encryption processing of a first password set by a user, acquiring an encrypted first password, splicing an encryption date and the encrypted first password, so as to obtain a spliced first sequence, encrypting the spliced first sequence and the random number to obtain a key sequence, counting the key sequence and the random number to determine an encryption starting position of the key sequence, and encrypting a to-be-encrypted file by using the key sequence based on the encryption starting position to obtain an encrypted file. The key sequence is not fixed and random, so that the flexibility and the unpredictability of the key sequence can be improved, the safety and the reliability of the encrypted file can be greatly improved, and the risk that file data isleaked can be reduced.
Owner:厦门天锐科技股份有限公司
Authorization encryption method of upper computer program of BMS (Battery Management System)
ActiveCN103049683ACopyright protectionEasy to use charging mechanismDigital data authenticationProgram/content distribution protectionPersonal computerAuthorization
The invention discloses an authorization encryption method of an upper computer program of a BMS (Battery Management System). The authorization encryption method comprises the following steps that: a user PC (Personal Computer) is installed with the upper computer program and obtains authorization through an authorization code; the upper computer program reads hardware information of the PC, generates a hardware identification code, puts the hardware identification code in the authorization code and stores a new authorization code in the upper computer program; the PC is connected to the BMS for the first time, the BMS interactively contrasts the authorization code information through the upper computer program and confirms if the PC is legally authorized; and when the BMS is needed to be connected to be written and read, the PC is connected to the BMS to start up the upper computer program, and the BMS checks if the upper computer program is legally authorized. The authorization encryption method of the upper computer program of the BMS can protect the upper computer program technology and use right thereof efficiently, prevent an authorization code file from being decrypted maliciously and reduce a risk of software imitation.
Owner:HUIZHOU EPOWER ELECTRONICS
Embedded software encryption registration method combining with embedded equipment
InactiveCN108897995ASimple encryptionEncryption method is reliableProgram/content distribution protectionEmbedded softwareComputer science
The invention discloses an embedded software encryption registration method combining with embedded equipment. According to the method, embedded software and the core processing unit ID of connected embedded equipment are bonded, the core processing unit ID and time of the embedded equipment are taken as encrypted parameter variables, registration is conducted by using an Rijndael algorithm in anaes algorithm to generate registration codes, secondary packaging encryption is conducted on the generated registration codes and the core processing unit ID of the embedded equipment to prevent errors in the mutual transmission process of the registration codes, the registration encryption of the embedded software is achieved, the normal, safe and reliable operation of the embedded software is ensured, malicious decryption on management software of a malicious opponent is effectively prevented, and the loss of an original producer is reduced.
Owner:河南正来电子科技有限公司
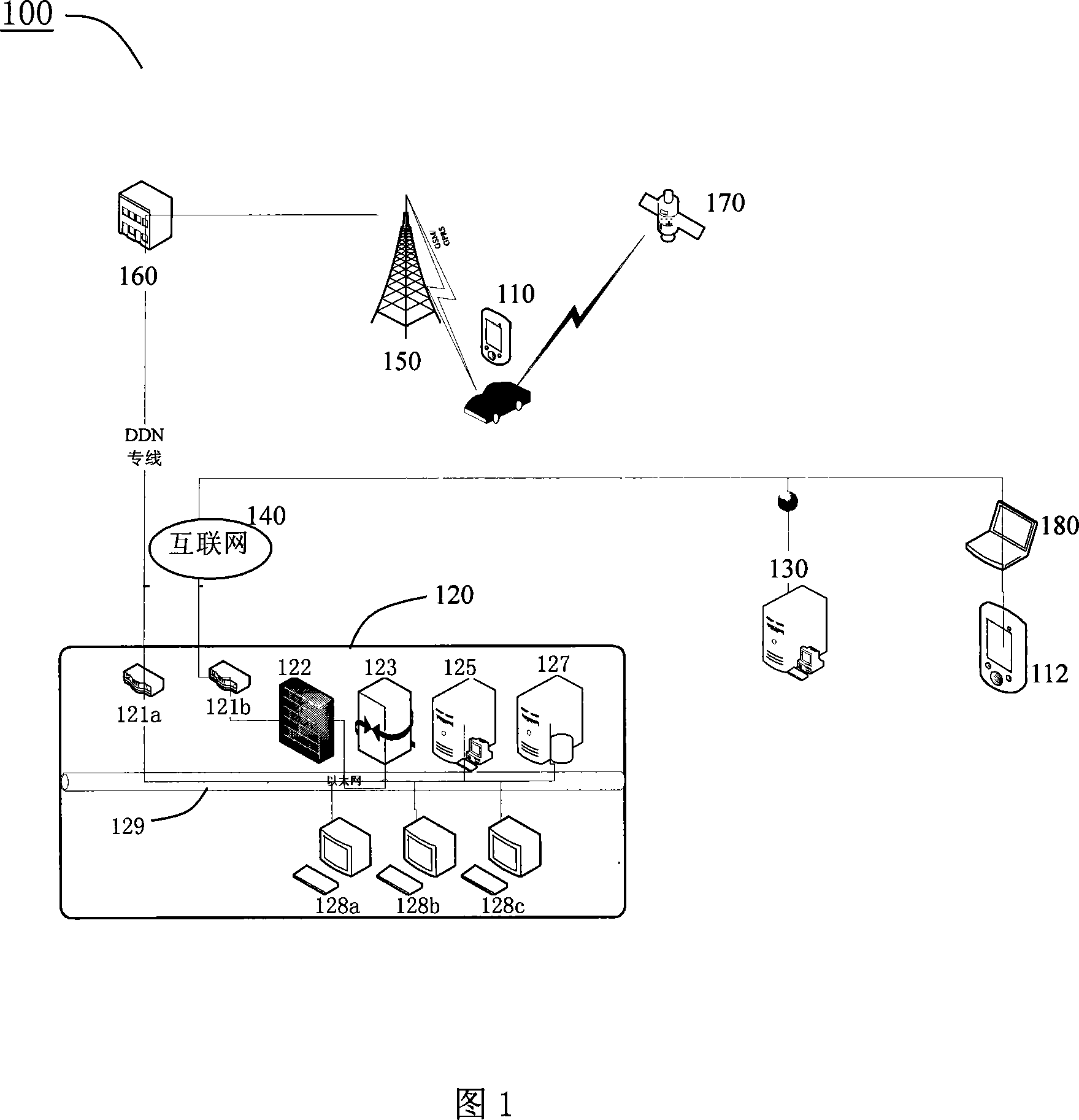
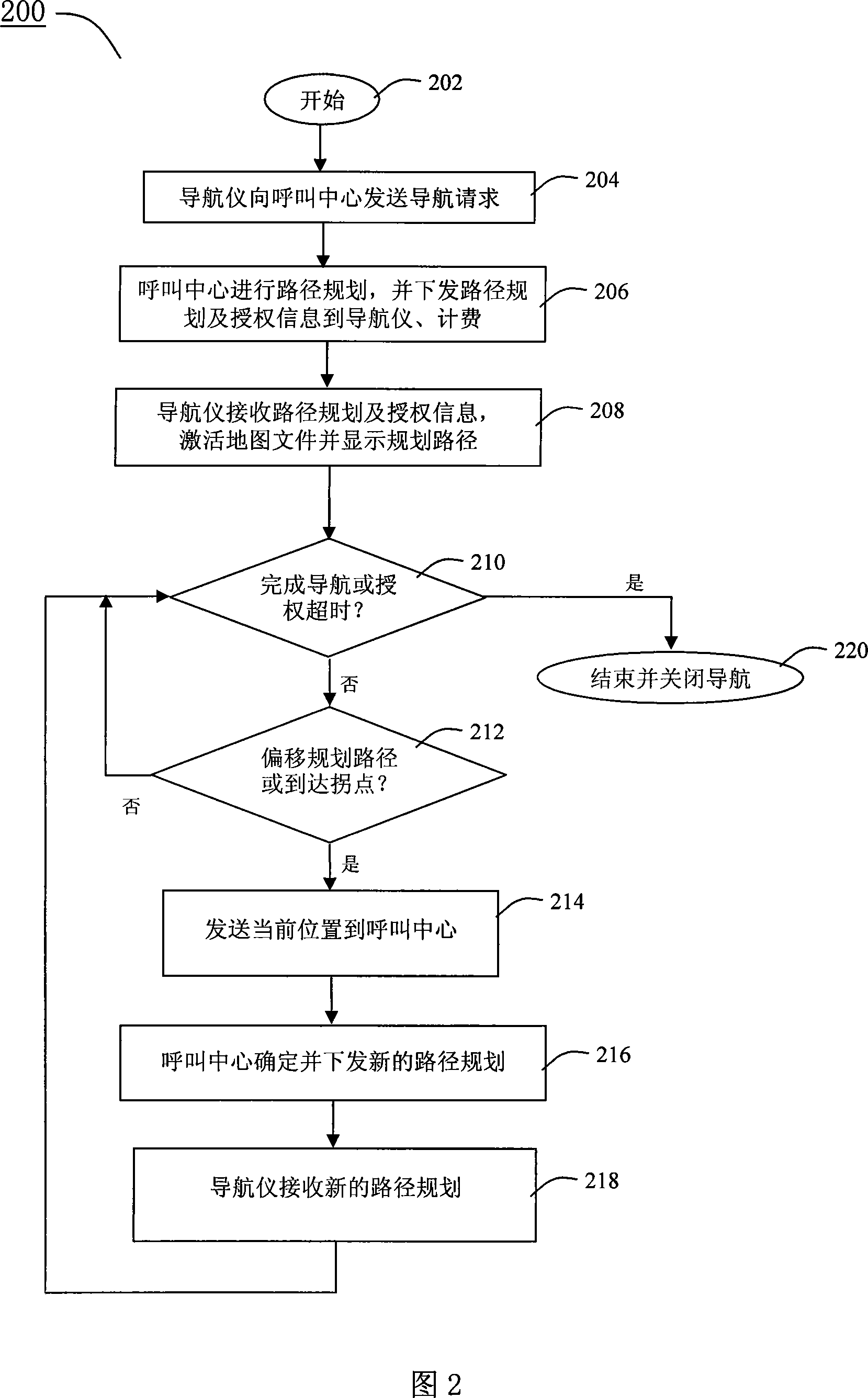
GPS navigation method and system
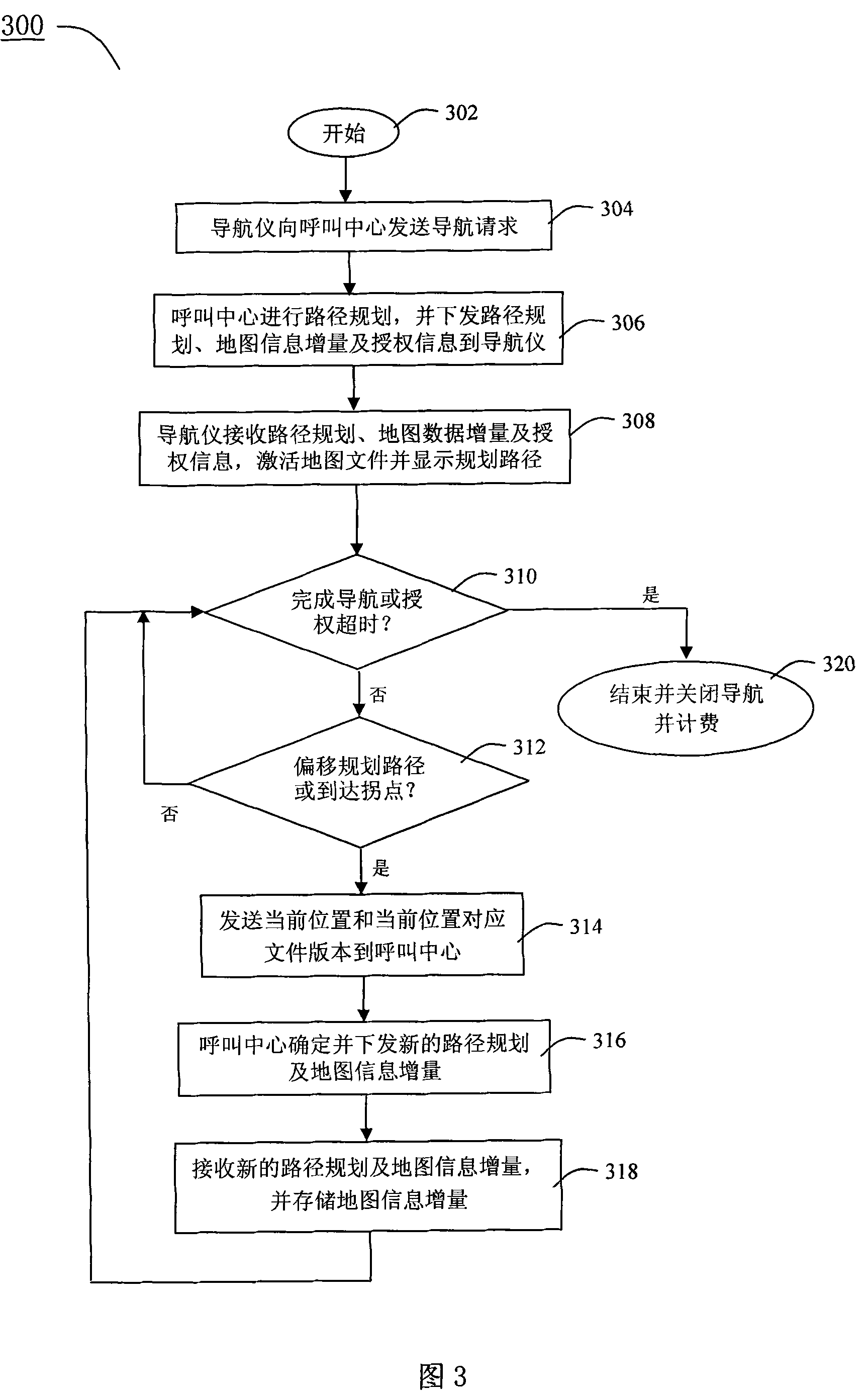
InactiveCN101183011BLess one-time investmentSave resourcesInstruments for road network navigationTariff metering apparatusGps navigationAuthorization
The invention relates to a GPS navigation method and a system and comprises that a navigator sends a navigation requirement to a calling center, wherein, the navigation requirement comprises the information about the present position of the navigator, the information about the position of the destination and the ID information of the navigator; the calling center formulates a routes plan based onthe navigation requirement and a dynamic traffic information; the calling center delivers the routes plan and an authorization information for activating a map file in the navigator to the navigator;the navigator receives the routes plan and the authorization information and activates the map file to display the planed routes; in the running process of the vehicle, the calling center formulates a novel routes plan according to the latest position information and the dynamic traffic information sent out by the navigator and delivers the novel routes plan to the navigator. In addition, the navigator sends out the edition information of the map file corresponding to the road sections around the present position stored in the navigator while sending out the present position information; the calling center compares the received edition information with the edition of the map used by the calling center and then determines the data increment of the map and delivers the data increment to thenavigator.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
Internet of Things intelligent meter safety system and implementation method
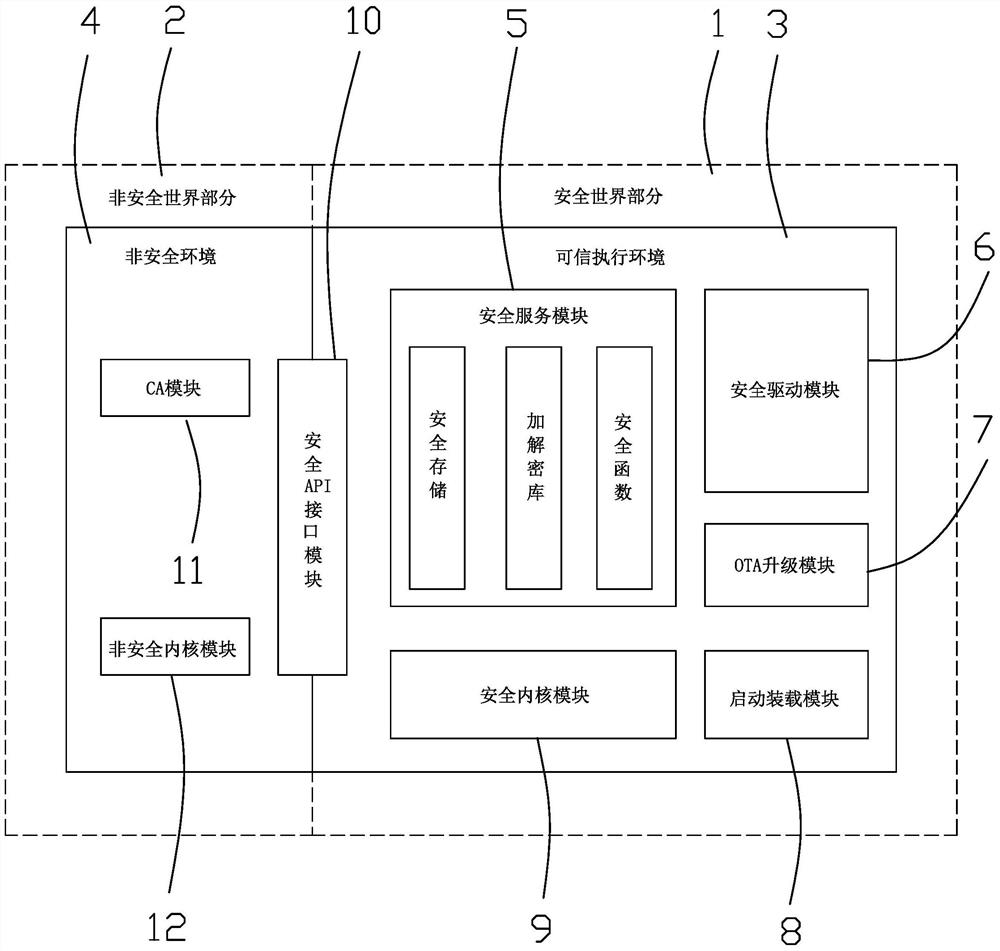
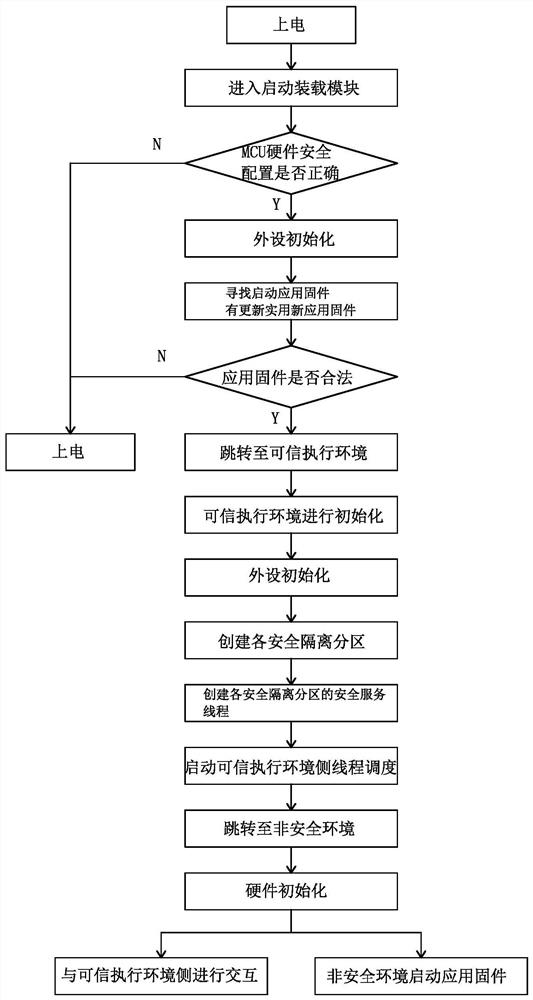
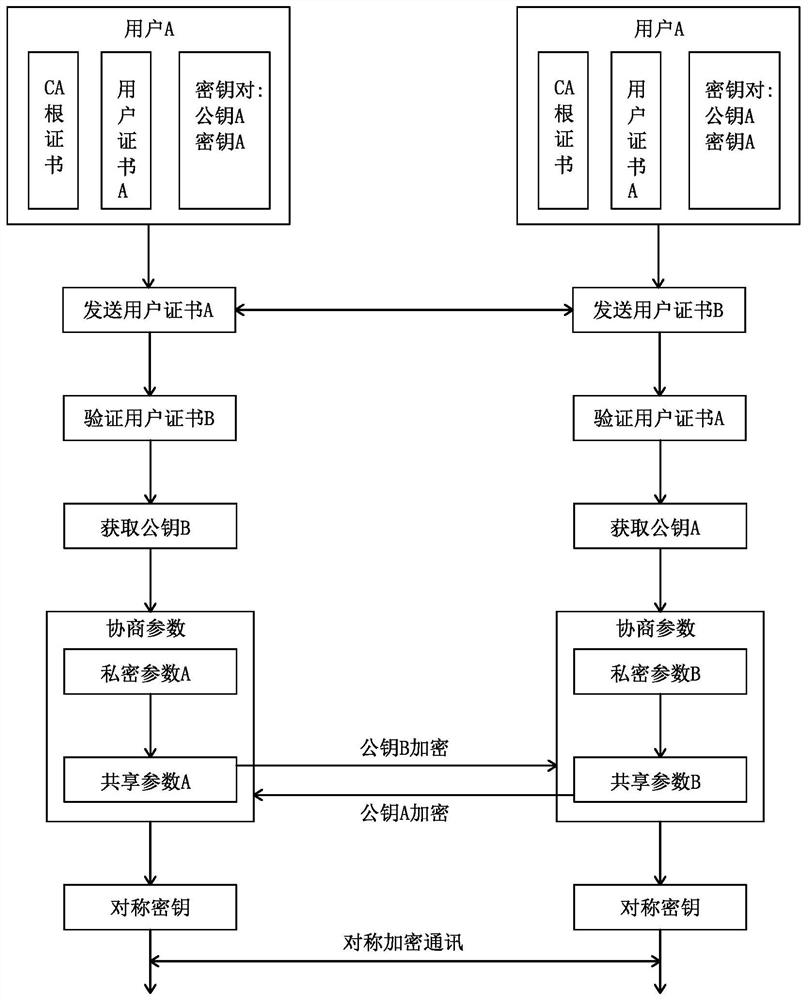
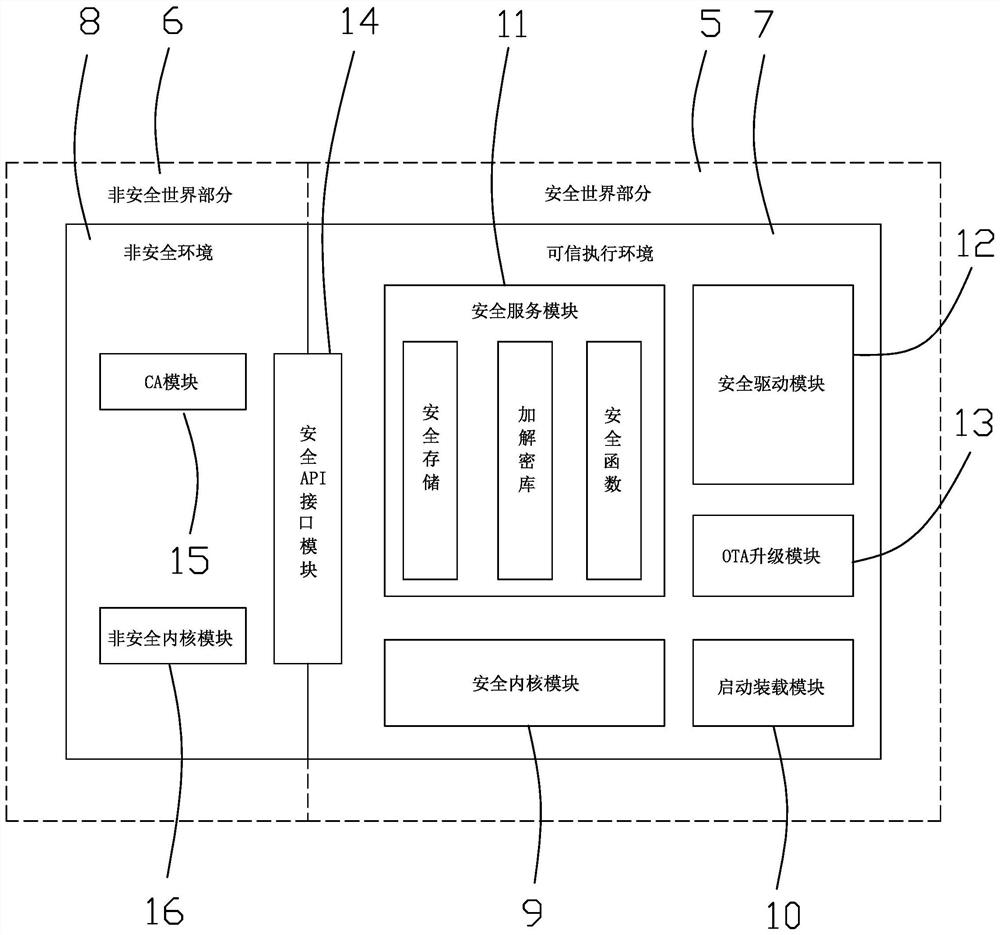
InactiveCN112311752AAvoid manipulationAvoid security breachesUtility meters data arrangementsDigital data protectionSecurity kernelEncryption
The invention discloses an Internet of Things intelligent meter safety system and an implementation method. The problems that existing meter hardware and software have security holes, communication encryption and decryption security is not high, and the efficiency ratio is low are solved. The system comprises a meter end and a cloud end which are in communication connection, the meter end comprises an MCU controller, the MCU controller comprises a safe world part and a non-safe world part, a trusted execution environment is deployed in the safe world part, and a non-safe environment is deployed in the non-safe world part. A security kernel module, a startup loading module, an OTA upgrading module, a security service module, a security driving module and a security API interface module arearranged in the trusted execution environment, and a user application CA module and a non-security kernel module are arranged in the non-security environment. Information between the meter end and thecloud end is communicated in an asymmetric and symmetric encryption and decryption combined mode. Safety protection is carried out on meter hardware, software and communication, so that the hardwareis prevented from being controlled, the software is prevented from being cracked, and information is prevented from being stolen.
Owner:杭州绿鲸科技有限公司
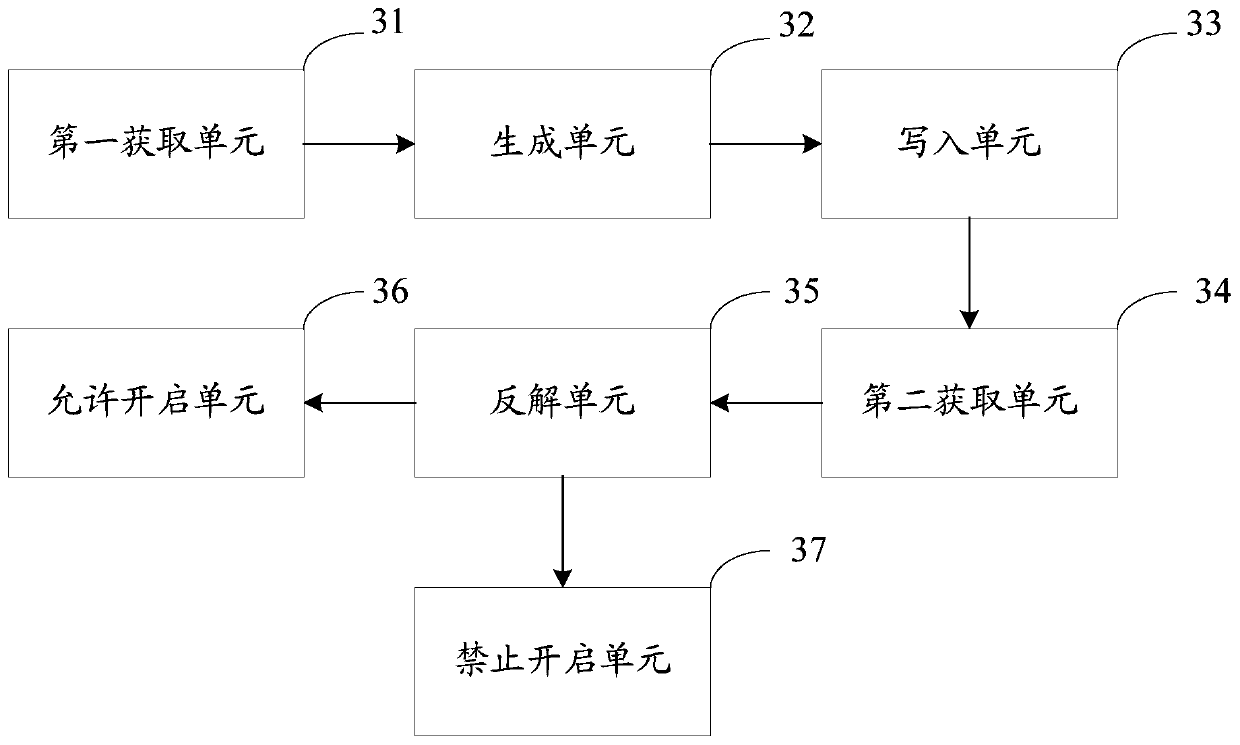
Chip mutual identification method and device, storage medium and mobile terminal
InactiveCN109858233AImprove program securityPrevent malicious crackingDigital data authenticationProgram securityComputer science
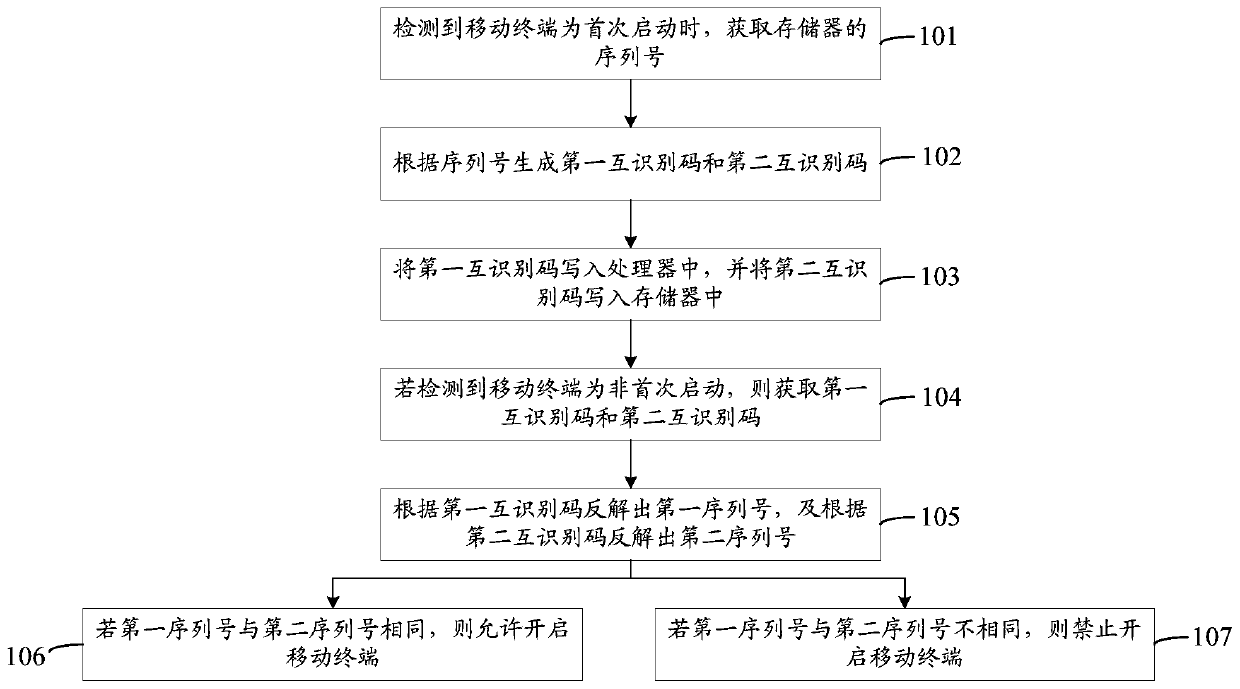
Embodiments of the invention disclose a chip mutual identification method and device, a storage medium and a mobile terminal. The method is applied to the mobile terminal comprising a processor and amemory, and comprises the steps: obtaining the serial number of the memory when detecting that the mobile terminal is started for the first time; generating a first mutual identification code and a second mutual identification code according to the serial number; writing the first mutual identification code into a processor, and writing the second mutual identification code into a memory; if it isdetected that the mobile terminal is not started for the first time, obtaining a first mutual identification code and a second mutual identification code; inversely solving a first serial number according to the first mutual identification code, and inversely solving a second serial number according to the second mutual identification code; if the first serial number is the same as the second serial number, allowing the mobile terminal to be started; and if the first serial number is different from the second serial number, forbidding starting the mobile terminal. Therefore, other people canbe prevented from maliciously cracking the program, and the program security of the mobile terminal is improved.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
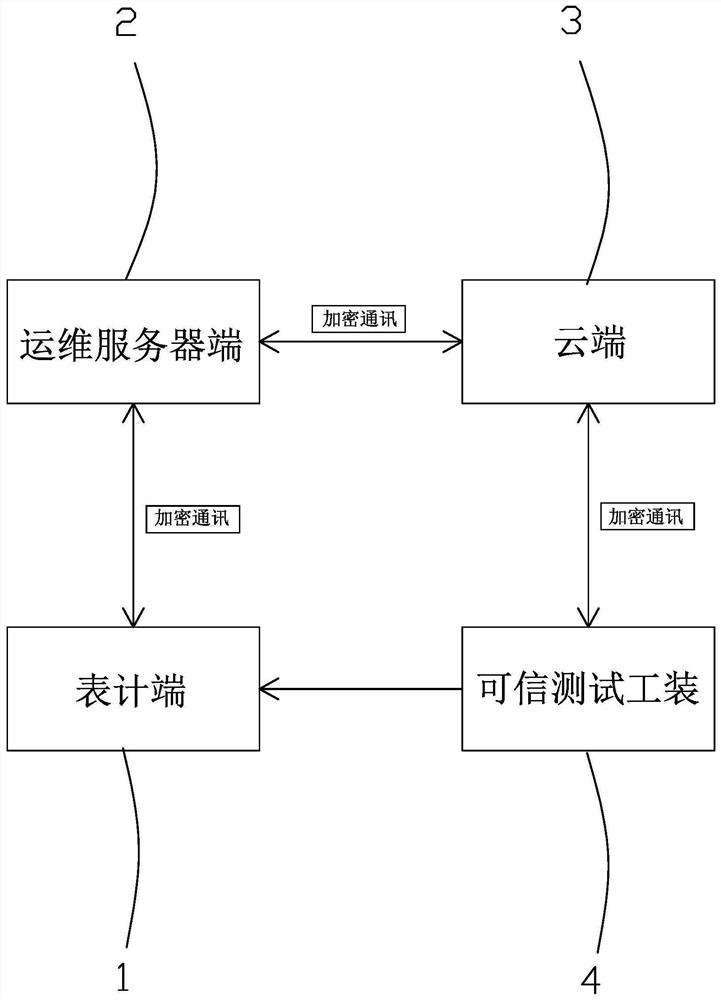
Internet of Things intelligent meter production test system and safety protection method
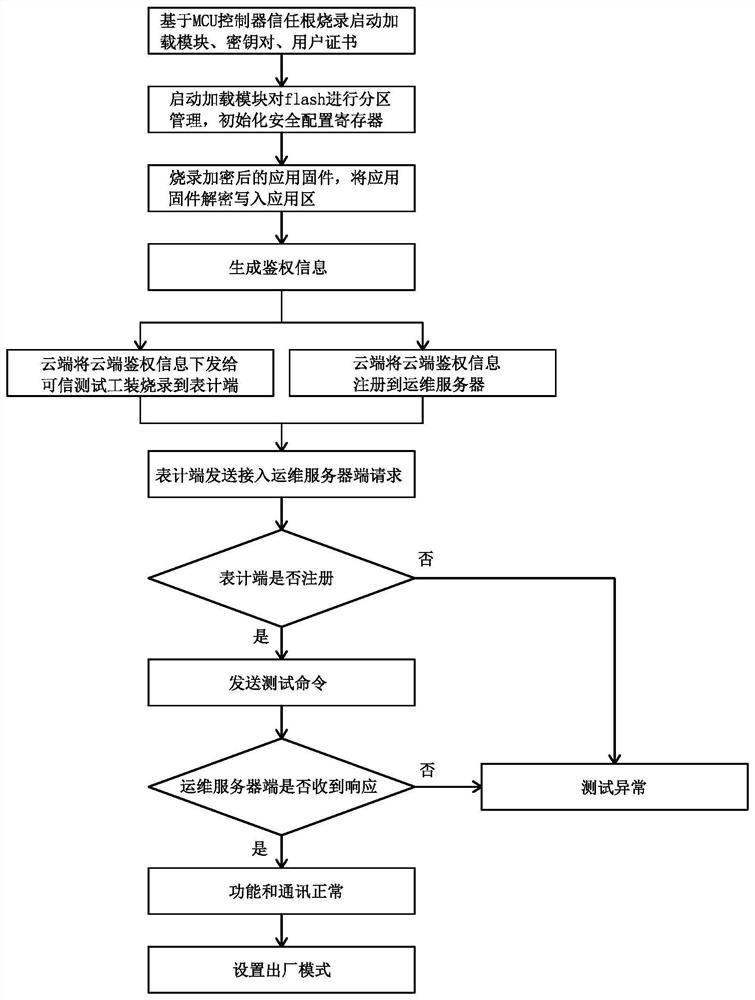
PendingCN112307463AEnsure safetyAddress the security risk of eavesdroppingUser identity/authority verificationDigital data protectionConnection tableEmbedded system
The invention discloses an Internet of Things intelligent meter production test system and a safety protection method. The problems that an existing meter lacks security and secrecy measures in the production test link, and information leakage exists are solved. The system comprises a meter end, an operation and maintenance server end and a cloud end which are sequentially connected through encryption communication, and a credible test tool is connected to the meter end and connected with a cloud end through encryption communication. In the production test period of the meter end, the contentcontacted by an operator is encrypted, all the content burnt into the MCU controller is verified, and all the communication is encrypted communication based on identity authentication, so that the leakage risk is reduced from the source.
Owner:杭州绿鲸科技有限公司
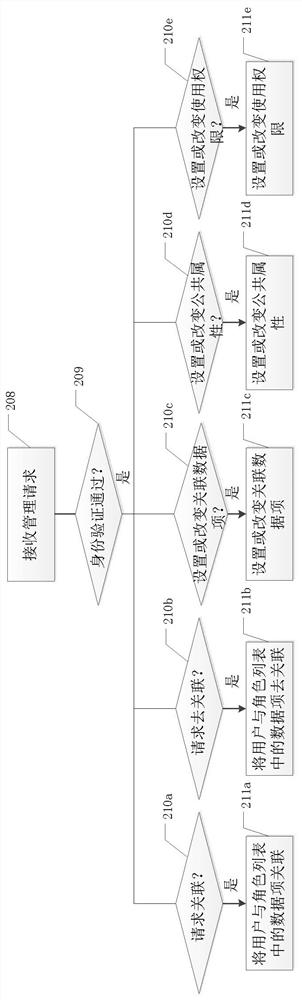
Method, device, and computer-readable storage medium for assigning usage rights to users
ActiveCN111416789BPrevent malicious crackingReduce total usageSecuring communicationEngineeringWorld Wide Web
The present invention provides a method for assigning usage rights to users, including: receiving a request for assigning the user a role among one or more roles that follow predetermined social rules in a virtual social space; A role list of the one or more roles in the virtual social space, wherein each data item in the role list represents one of the one or more roles in the virtual social space and includes the relationship between the one role and the predetermined social interaction Use rights associated with rules: in response to associating the user with a data item in the role list, granting the user the use rights associated with a predetermined social rule of the role included in the data item. The present invention also provides corresponding devices and computer-readable storage media.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for vehicle data diagnosis
ActiveCN110989564BPrevent malicious crackingAvoid using effectsProgramme controlElectric testing/monitoringEmbedded systemDiagnostic equipment
Owner:LAUNCH TECH CO LTD
An intelligent auction method of Dianpai.com
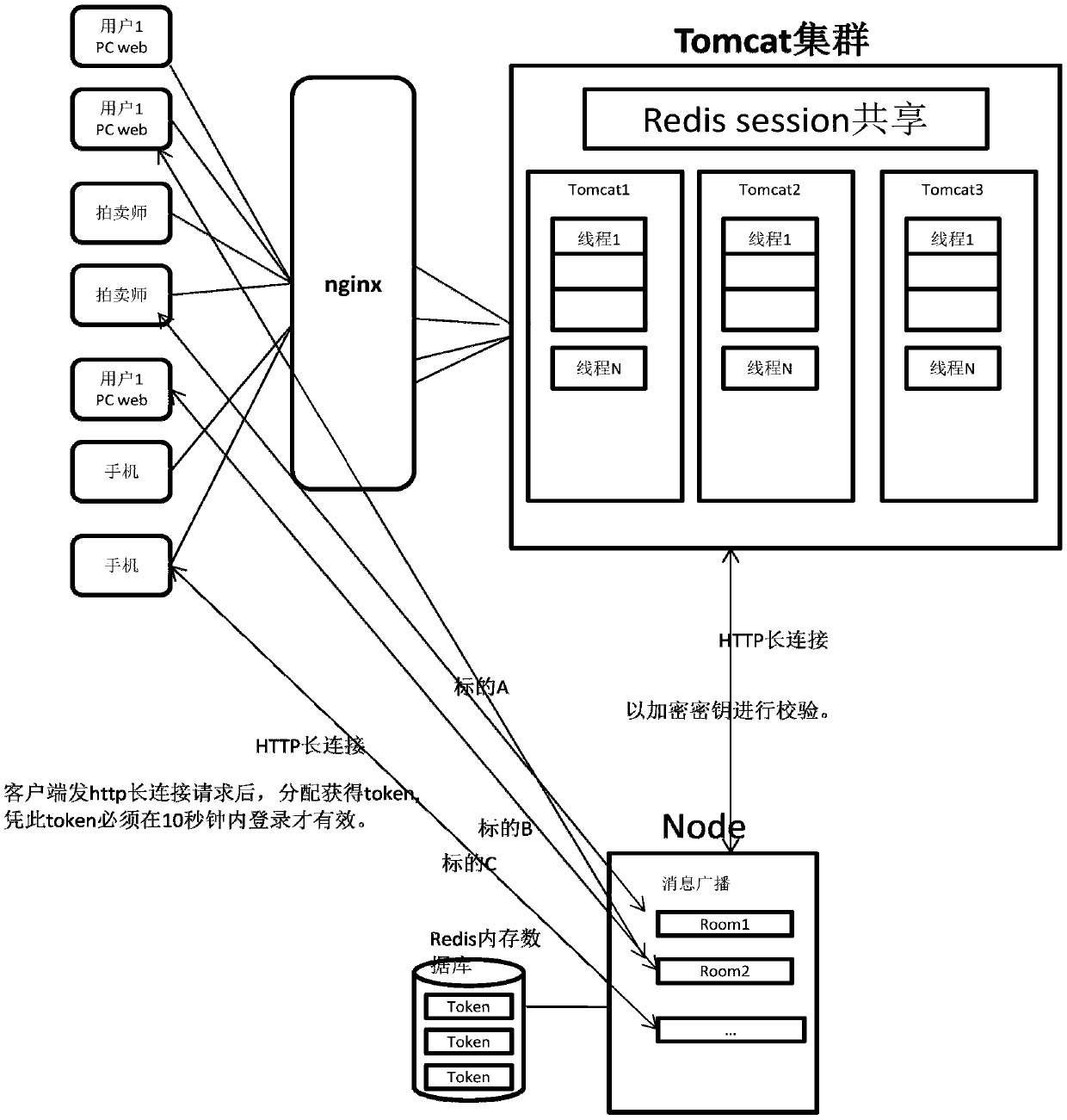
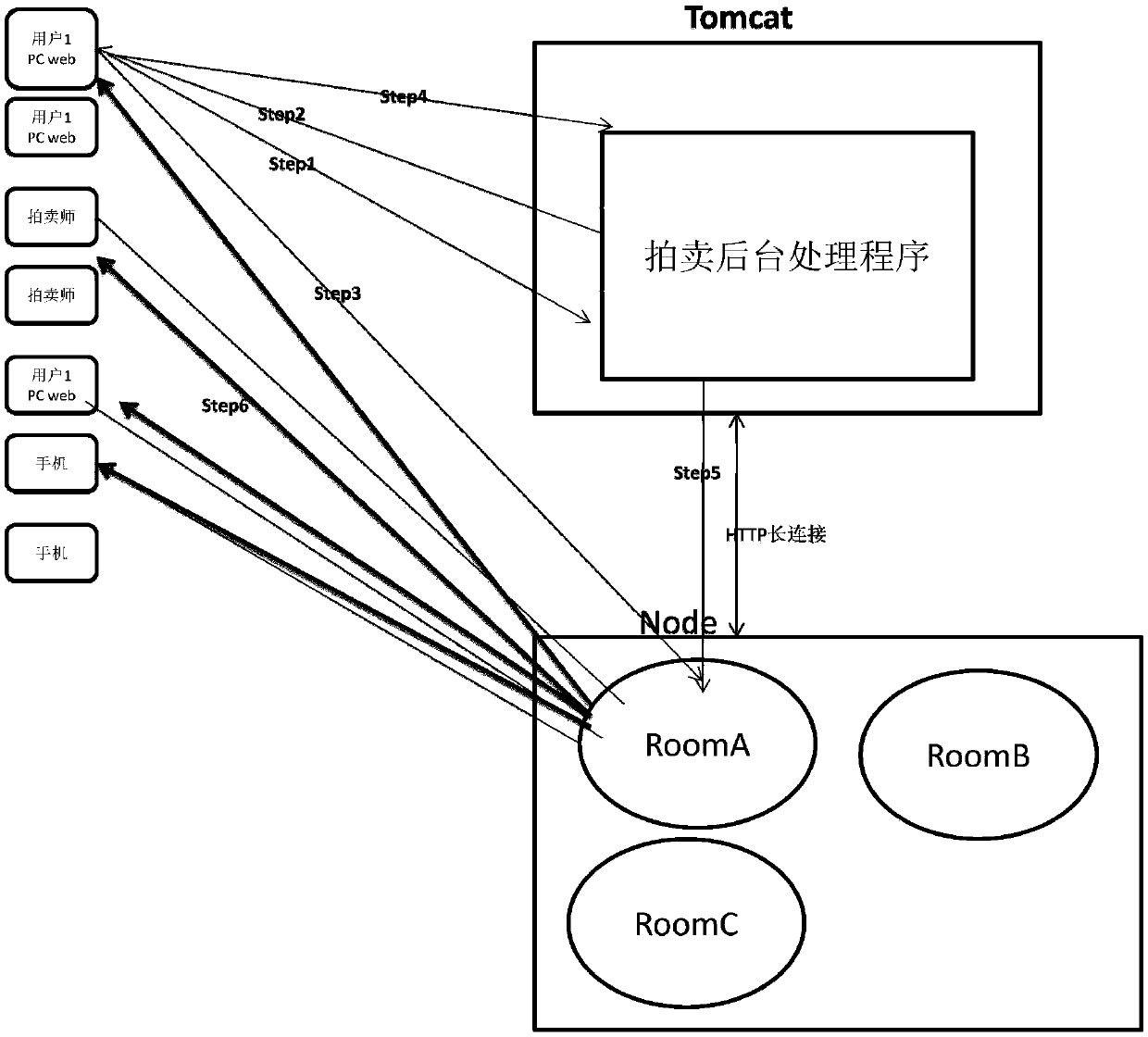
The invention relates to an intelligent auction method for a click auction website. The method comprises a login step and an auction step. In the login step, firstly, the method determines whether a user is a registered user; secondly, a user name and a password are entered, a request including target_id is initiated, and whether the user is registered is judged, a Token code is returned and the method enters a third step if the user is registered, or an error message is returned if the user is not registered; and thirdly, the Token code is used to connect with a Node, a long connection is set up, and according to the target_id in the request, the user joins a corresponding room where a target that bidders / auctioneers intend to bid for / auction is. In the click auction website, each target is corresponding to a room, bidders and auctioneers participating in the auction of the target all join the room; the room in the Node is like a chat room, messages of operations of the bidders and auctioneers are all broadcasted in real time in the room, and the messages are not broadcasted to other irrelevant users.
Owner:山东佳联电子商务有限公司
Anti-cracking method and system for software
ActiveCN106096336BPrevent malicious crackingKey distribution for secure communicationUser identity/authority verificationPlaintextTerminal equipment
The invention discloses a software anti-crack method and system. The method comprises the steps that terminal equipment acquires an application private key from an application management server when the terminal equipment needs to install a main application file of an application, and if acquiring fails, installation is stopped; when the terminal equipment receives a function execution command to the application for the first time, the terminal equipment applies to the application management server for the application function load authorization, after the authorization is acquired, a class SEC file of the application is loaded, the SEC file is encrypted by means of the application private key, the acquired encrypted file F[SEC] is saved, and the application private key and a plaintext of the SEC file are deleted; when the terminal equipment receives the function execution command to the application not for the first time, the terminal equipment applies to the application management server for a decryption key corresponding to the application private key, the applied decryption key is utilized for decrypting the encrypted file F[SEC], the plaintext of the SEC file is acquired and loaded, and after loading is finished, the decryption key and the plaintext of the SEC file are deleted. By means of the software anti-crack method and system, the software can be effectively prevented from being cracked maliciously.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
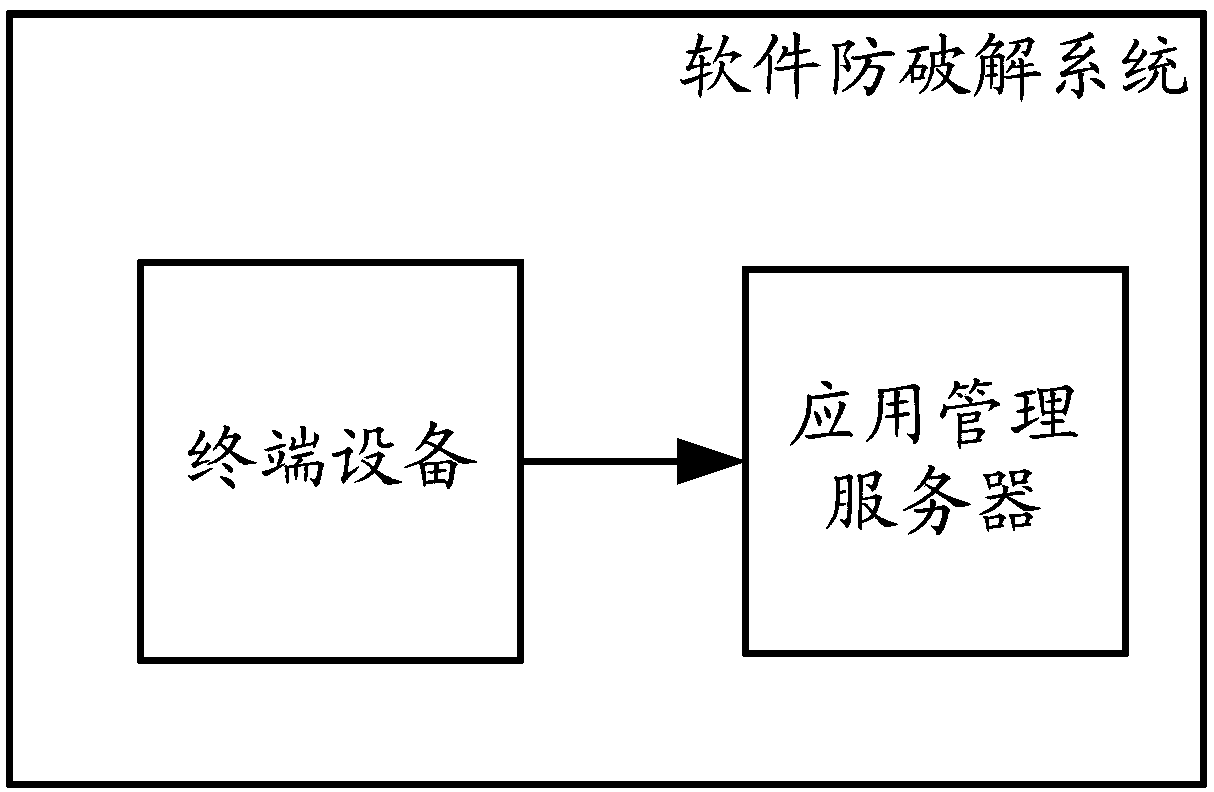
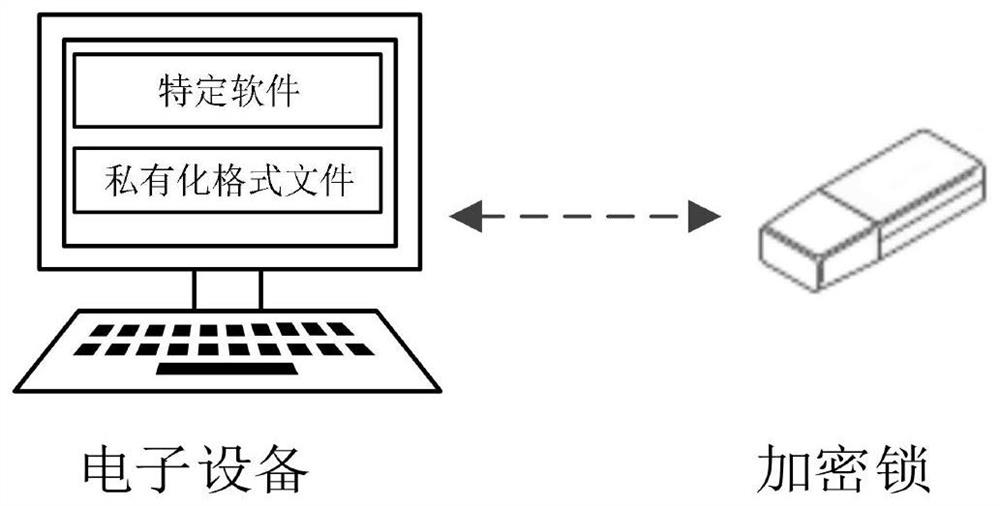
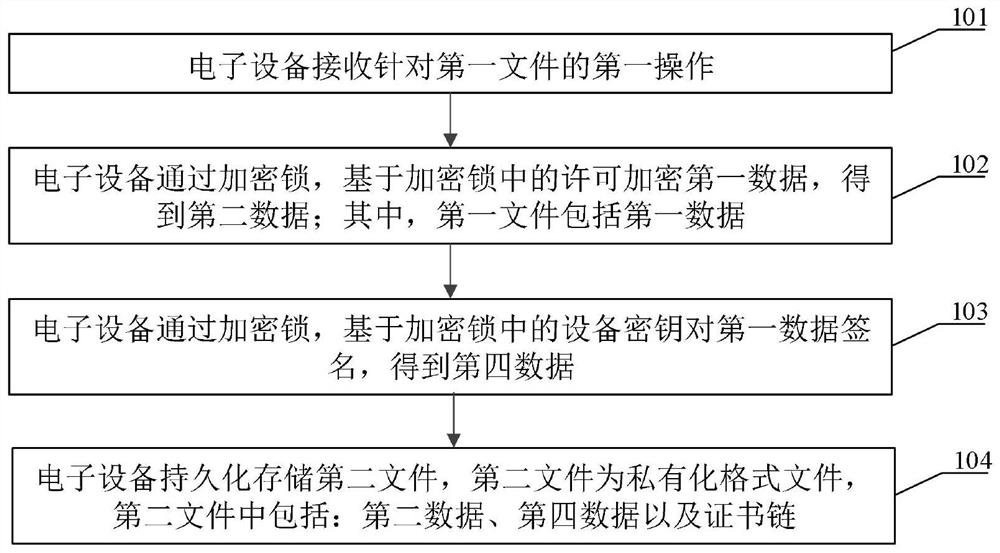
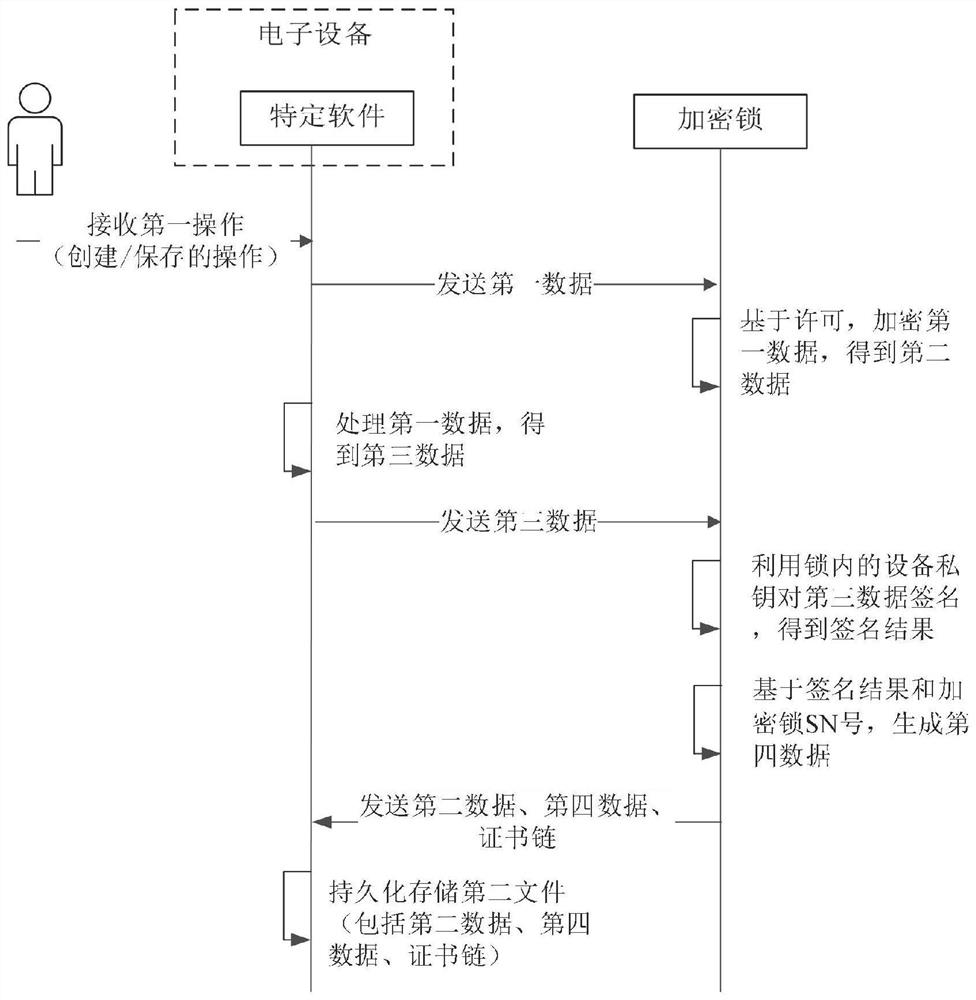
Private format file processing method, electronic equipment and medium
PendingCN114329564APrevent illegal modificationEasy to trace the editing historyDigital data protectionEngineeringTerm memory
The invention discloses a method and equipment for processing a file in a privatized format. The method is applied to the electronic equipment and comprises the steps that a first operation for a first file is received, the first file is a privatized format file and located in a memory of the electronic equipment, and the first operation is used for instructing specific software to store the first file; encrypting the first data through the encryption lock to obtain second data, the first file including the first data; signing the first data based on an equipment private key in the encryption lock to obtain fourth data; wherein the device private key corresponds to a developer of the specific software associated with the privatized format file; and persistently storing a second file comprising the second data, the fourth data and the certificate chain. By adopting the implementation mode, the user can open, edit and store the file in the privatized format only under the condition that the user can legally use the specific software and hold the specific encryption lock capable of decrypting the file in the privatized format, so that the content of the file can be prevented from being maliciously acquired.
Owner:上海纬百科技有限公司
Executable program data packet encryption/decryption method and device
ActiveCN106055936BGuaranteed confidentialityPrevent malicious crackingDigital data protectionProgram/content distribution protectionMultiple encryptionNetwork packet
The invention provides a method and device for encryption / decryption of an executable program data package. The method comprises the steps that the executable program data package is acquired; based on preset rules, the executable program data package is divided into multiple original documents; a first secret key is used to encrypt the multiple original documents respectively, so that encryption documents which have one-to-one correspondence relations with each original document respectively can be obtained; the multiple encrypted encryption documents are received; a second secret key corresponding to the first secret key is used to decrypt the multiple encryption documents respectively, so that the multiple original documents which have the one-to-one correspondence relations with the encryption documents can be obtained; and index information of the original documents are used respectively to reform the multiple original documents, so that the executable program data package can be obtained. The method and the device provided by the invention have the advantages that vicious decryption of the executable program data package caused by theft of a single secret key in the executable program data package can be prevented; a probability of the vicious decryption of an application program can be reduced; and data safety of the application program can be enhanced.
Owner:SHENZHEN UNIV
Connection method and system for wireless fidelity network
ActiveCN105072615BImprove securityImprove experienceConnection managementTransmissionNetwork connectionEngineering
The present invention relates to a wireless fidelity network connection method and system, the method comprising: a wireless fidelity hotspot receives a wireless fidelity network connection request from a mobile terminal, and obtains a key and identity information sent by the mobile terminal; The Wi-Fi hotspot judges whether the identity information matches the pre-stored identity information, and judges whether the key matches the preset key; if the identity information matches the pre-stored identity information, and the key matches the pre-stored Assuming that the keys match, the Wi-Fi hotspot establishes a Wi-Fi network connection with the mobile terminal. The present invention greatly improves the security of Wi-Fi network connection through the double verification mechanism of identity information and key, can effectively prevent Wi-Fi hotspots from being maliciously cracked, avoid user data traffic from being maliciously used, and further improve user experience .
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com