Method and system for realizing password retrieval based on multiple safety verification ways
A password recovery and security verification technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., to achieve the effects of protecting security, ensuring security, and preventing malicious cracking of passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
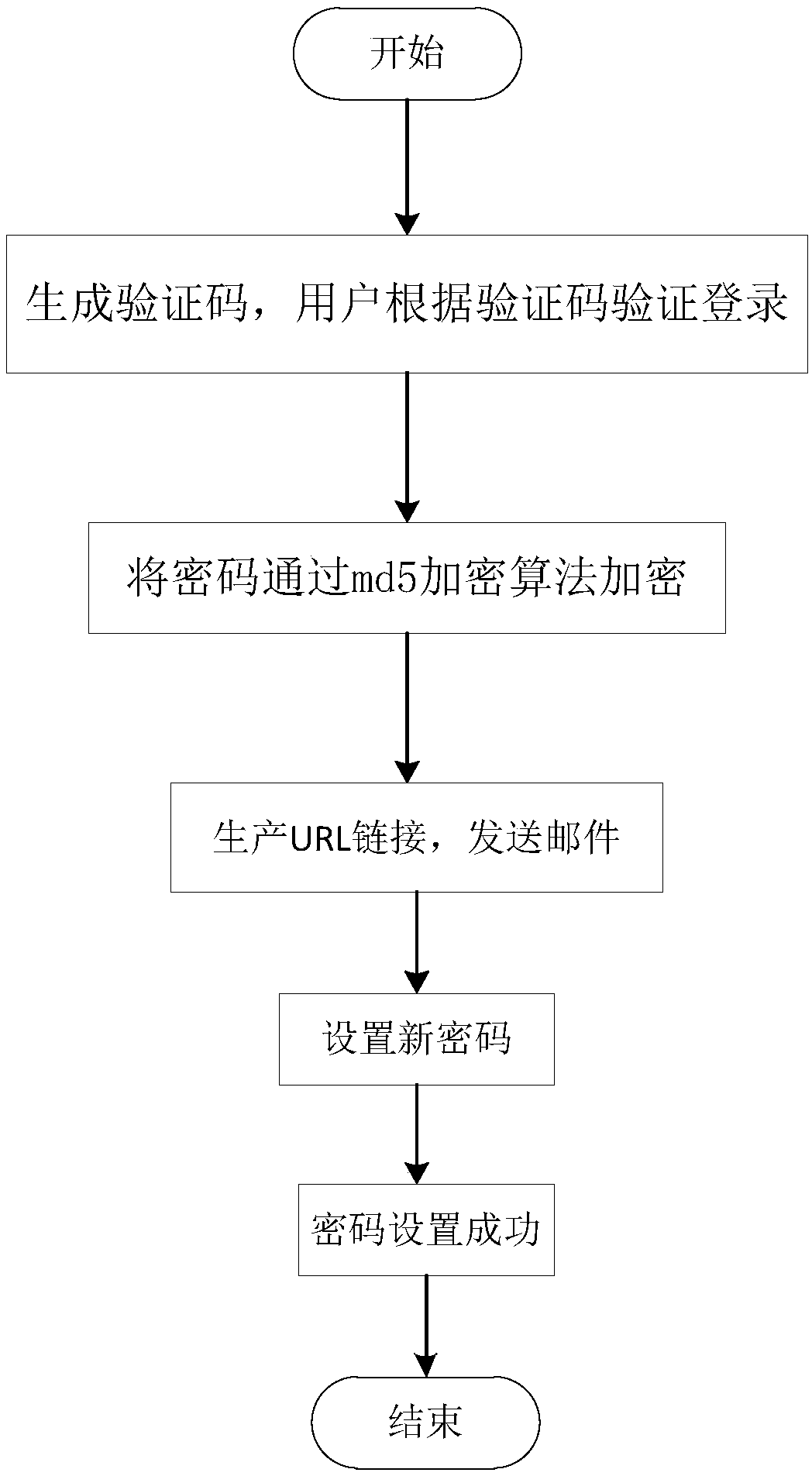
[0078] as attached figure 1 As shown, the present invention realizes the method for retrieving passwords based on multiple security verification methods, and the method mainly includes the following steps:
[0079] S1. Generate a verification code, and the user verifies and logs in according to the verification code;
[0080] Among them, the specific steps to generate the verification code are as follows:
[0081] S101. Set the font of the production verification code through the getFont() method;
[0082] S102. Obtain the random color of the generated font through the getRandColor(int fc, int bc) method;
[0083] S103, drawing a randomly generated character string through drowString(Graphics g, String randomString, int i);
[0084] S104, draw the interference line by the drowLine(Graphics g) method;
[0085] S105, obtain random characters by getRandomString (int num) method;
[0086] S106. The getRandcode() method generates a random image with fixed sizes, different line...
Embodiment 2
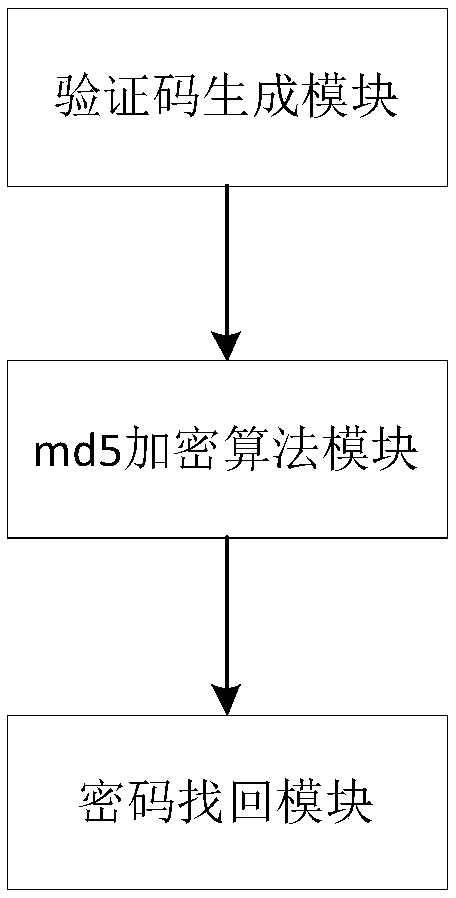
[0114] as attached figure 2 As shown, the password recovery system based on multiple security verification methods of the present invention includes a verification code generation module, an md5 encryption algorithm module, and a password retrieval module; wherein, the verification code production module is used to produce verification codes, and the user The verification code verification login md5 encryption algorithm module is used to encrypt the password through the md5 encryption algorithm, then add the verification code to the back, and then encrypt it with the md5 encryption algorithm, and transmit it to the background database in the form of cipher text during network transmission; The return module is used to generate URL links and send emails to user mailboxes. Users set new passwords. If the passwords are set successfully, the password can be retrieved according to the mailboxes.
[0115] Among them, the specific steps to generate the verification code are as follo...
Embodiment 3
[0137] Specific steps are as follows:
[0138] (1) Implementation of md5 encryption algorithm, the main code is as follows:
[0139]
[0140]
[0141] (2), the verification code generation algorithm, the code is as follows:
[0142]
[0143]
[0144]
[0145]
[0146] (3) Send an email to the specified email address, verify whether the email address exists, and generate an email link address if it exists. The main code is as follows:
[0147]
[0148]
[0149]
[0150] (4) After the email is sent successfully, enter the mailbox, enter the password modification request through the link, and enter the password modification page after the link verification is passed, which is used to process the password modification request linked from the mailbox. The main code is as follows:
[0151]
[0152]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com