Executable program data packet encryption/decryption method and device
A technology for executing programs and data packets, applied in the field of data security, can solve the problems that the encryption method is easy to be cracked and cannot effectively reduce the malicious cracking of application programs, so as to reduce the probability of malicious cracking, improve the difficulty of cracking, and reduce the the effect of prevention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
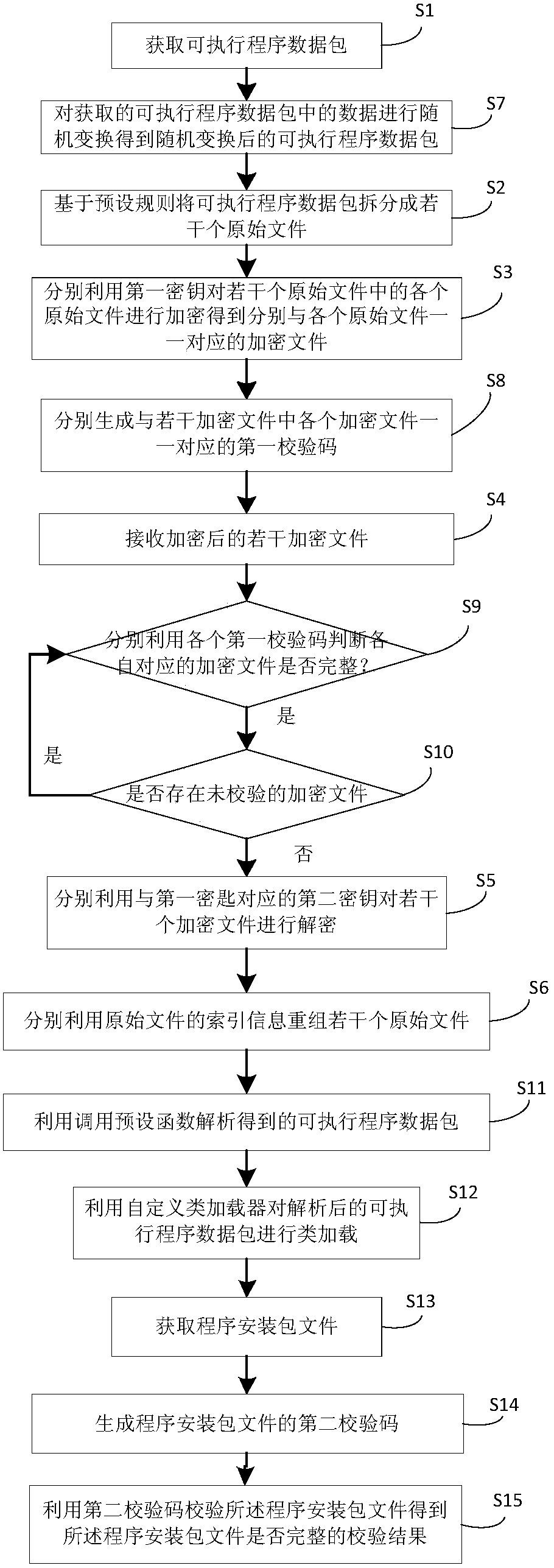
[0025] This implementation discloses an executable program data packet encryption / decryption method, such as figure 1 As shown, the method includes the following steps:
[0026] When encrypting executable program data packets:
[0027] S1. Obtain an executable program data package. In this embodiment, the executable program data package may be an executable file on the Android platform. In a specific embodiment, an encryption tool may be used to obtain the executable program data package.
[0028] S2. Splitting the executable program data package into several original files based on preset rules. In a specific embodiment, it can be preset that the executable program data package after random data transformation is divided into multiple files, for example, it can be equally divided into 8 binary files. The number of splits mentioned here is an example, and other more or Lesser quantity is workable. When splitting the executable program data package after random data change...
Embodiment 2
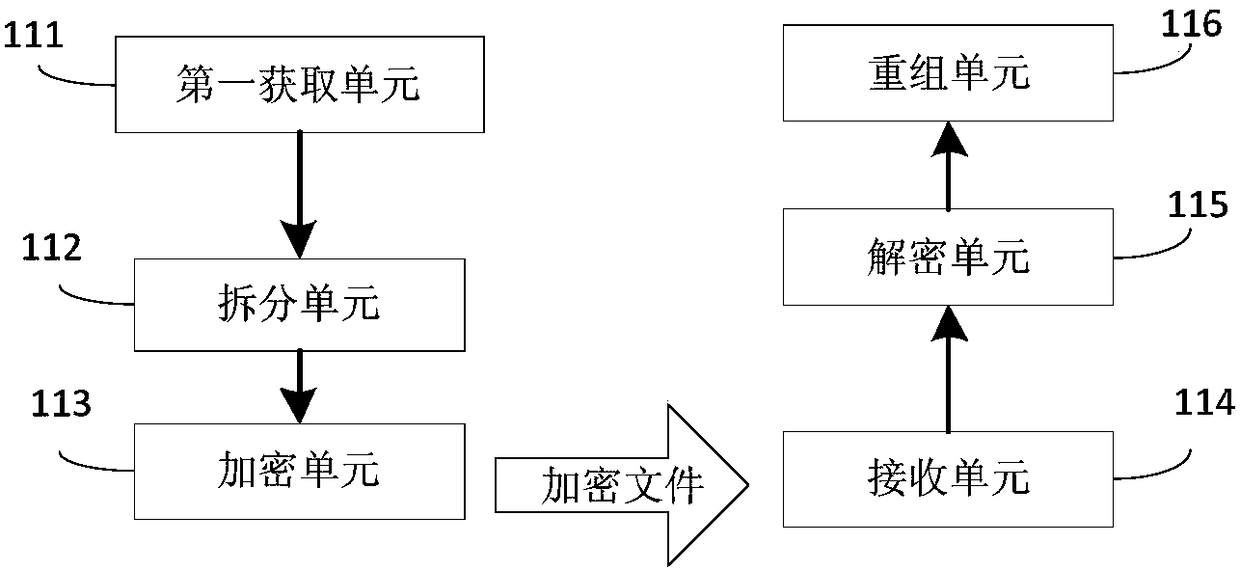
[0052] This embodiment provides an executable program data packet encryption / decryption device. Such as figure 2 As shown, the executable program data packet encryption / decryption device includes: a first acquisition unit 111, a split unit 112, an encryption unit 113, a receiving unit 114, a decryption unit 115 and a reassembly unit 116 wherein,
[0053] The first obtaining unit 111 is used to obtain the executable program data package;
[0054] A splitting unit 112, configured to split the executable program datagram into several original files based on preset rules;
[0055] An encryption unit 113, configured to encrypt each original file in the plurality of original files using the first key to obtain an encrypted file corresponding to each original file respectively;
[0056] A receiving unit 114, configured to receive encrypted encrypted files;
[0057] Decryption unit 115, configured to decrypt several encrypted files using the second key corresponding to the first k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com