Implementation method and system of openstack token access protection mechanism
A technology of protection mechanism and implementation method, applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as data leakage and lack of security mechanisms in Memcache, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
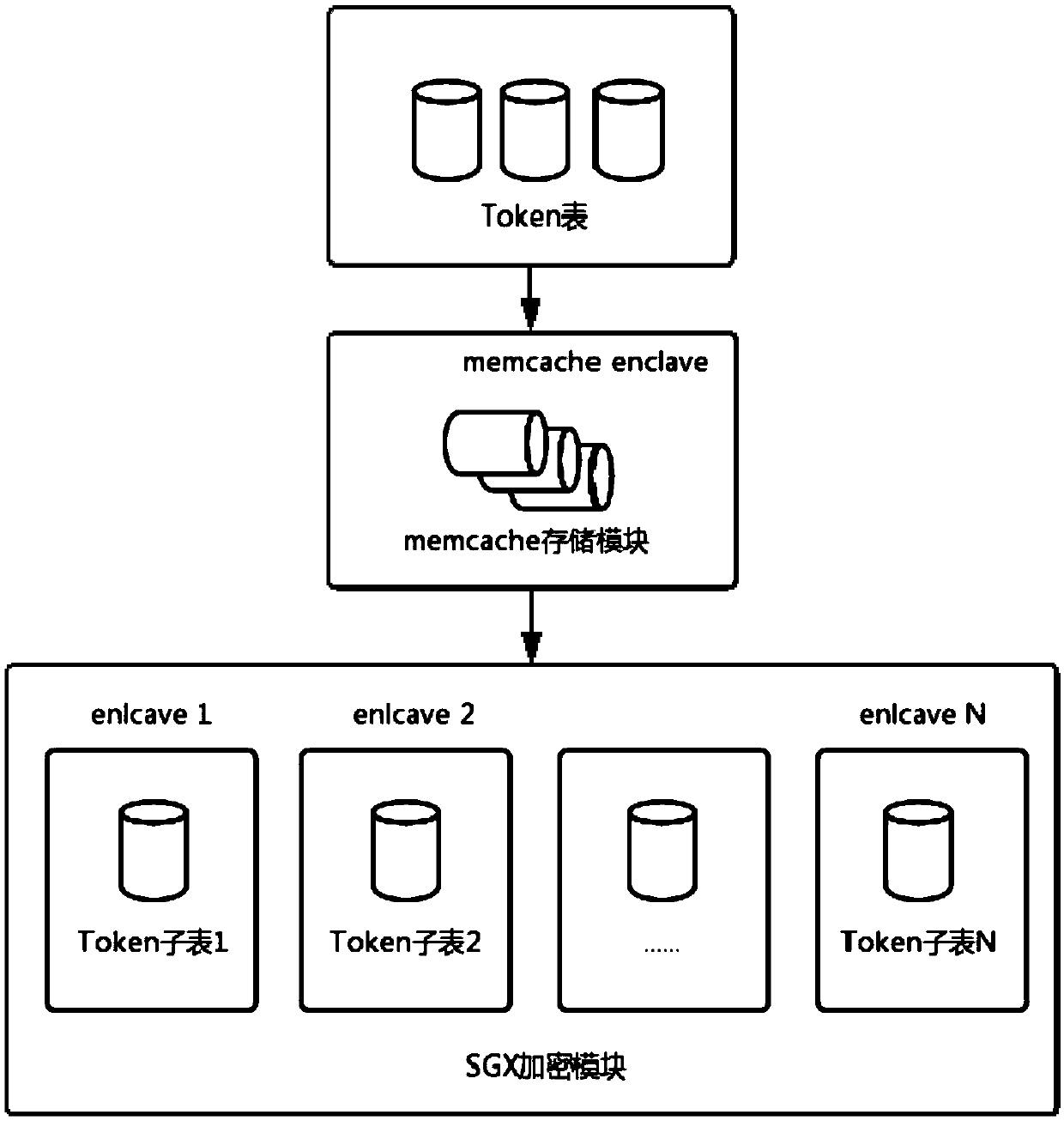
[0043] The present invention is realized by 2 software modules: memcache storage module and SGX encryption module, its flow control is as follows figure 1 shown.
[0044] The role of the memcache storage module is to distribute the token table stored in the openstack storage mode, and use memcache as the driver. Specific steps are as follows:
[0045] (1) Edit the Token field of / etc / keystone / keystone.conf:
[0046] driver=keystone.token.backends.memcache.Token, change its driver to memecache;
[0047] (2) Restart keystone, and start memcache, and manage the distributed storage token table through memcache.
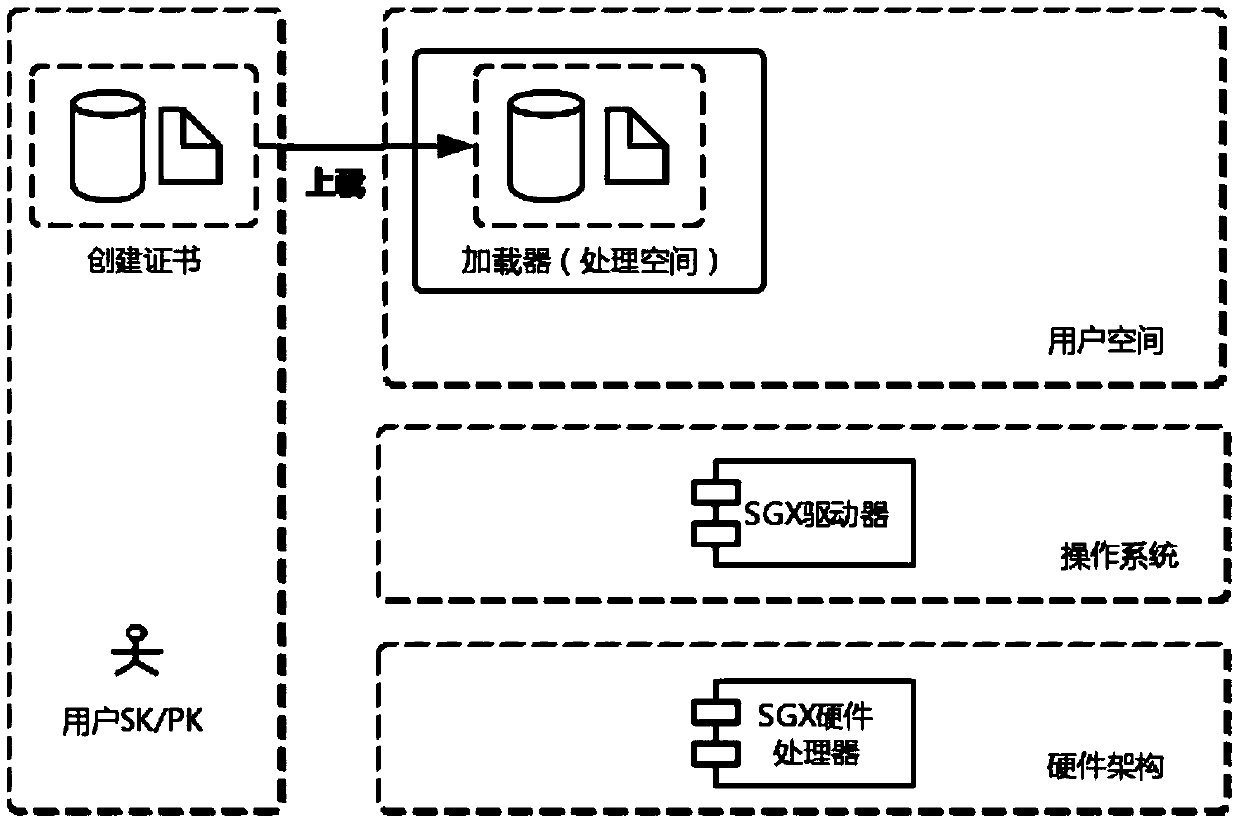
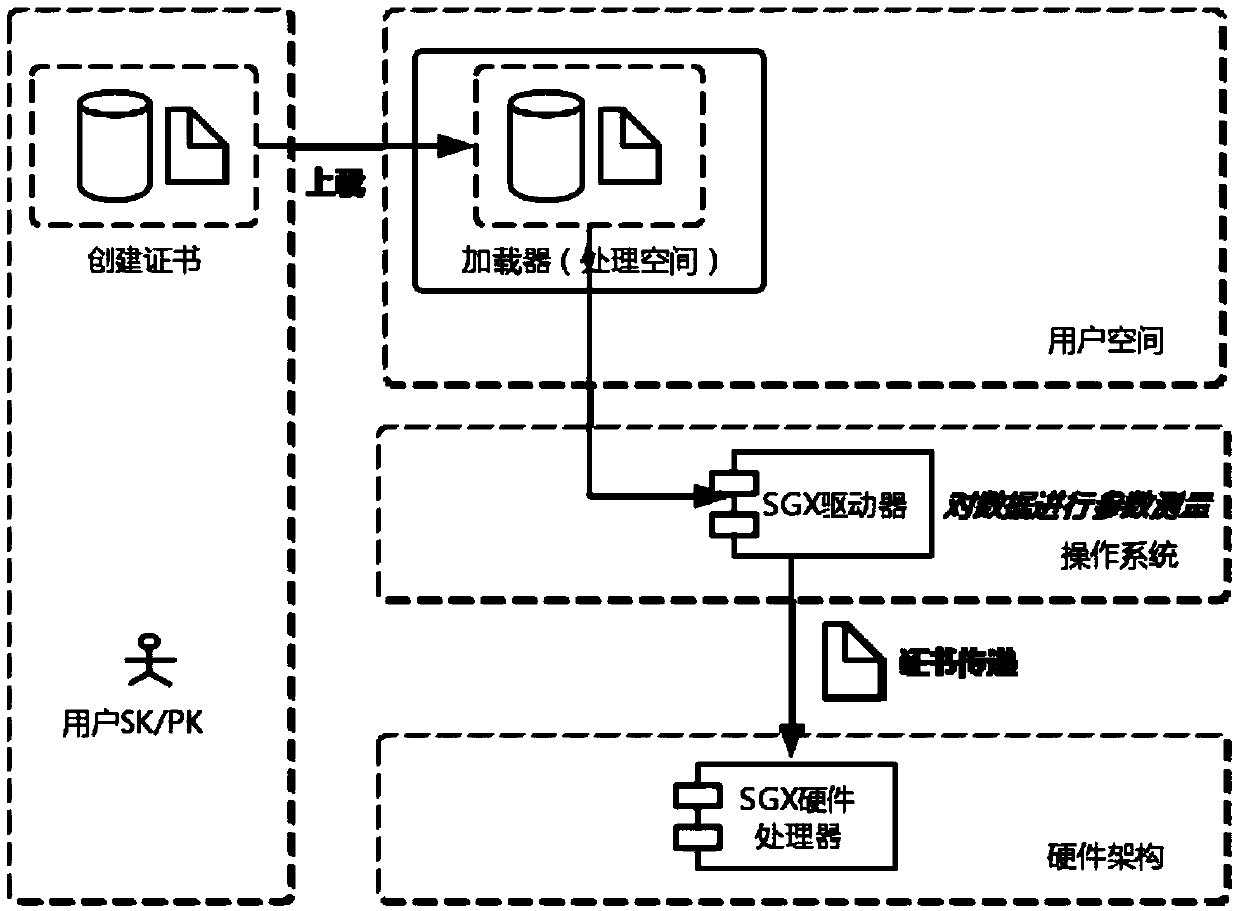
[0048] The role of the SGX encryption module is to generate a trusted space to store and operate corresponding data, and to generate keys for verifying access rights. Its working principle is as follows:
[0049] (1) Data upload stage...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com