Method and system for preventing PowerShell malicious code execution
A malicious code and operation execution technology, applied in the field of information security, to prevent APT attacks and ransomware intrusion, and prevent the execution of malicious code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
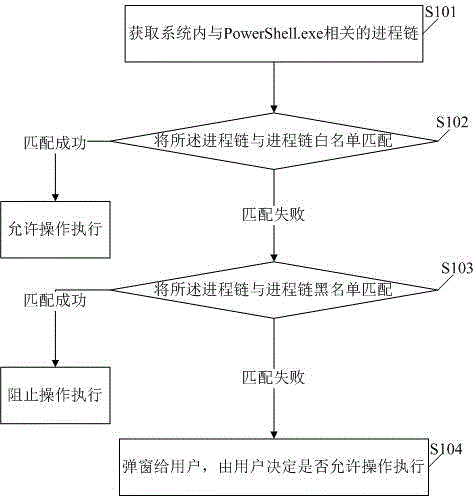
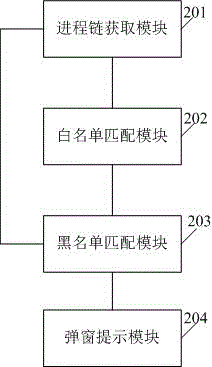
[0054] The present invention provides a method and a system embodiment for defending against PowerShell malicious code execution, in order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the present invention It can be more obvious and understandable, and the technical solution in the present invention will be described in further detail below in conjunction with the accompanying drawings:
[0055]At present, PowerShell malicious code is used by various malicious programs to spread and execute programs with actual malicious functions. It mainly includes APT and ransomware, for example: PowerShell code embedded in office macro code, PowerShell code embedded in installation package program, PowerShell code embedded in database file, etc. Because the method of embedding script code into other programs has strong anti-killing ability and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com