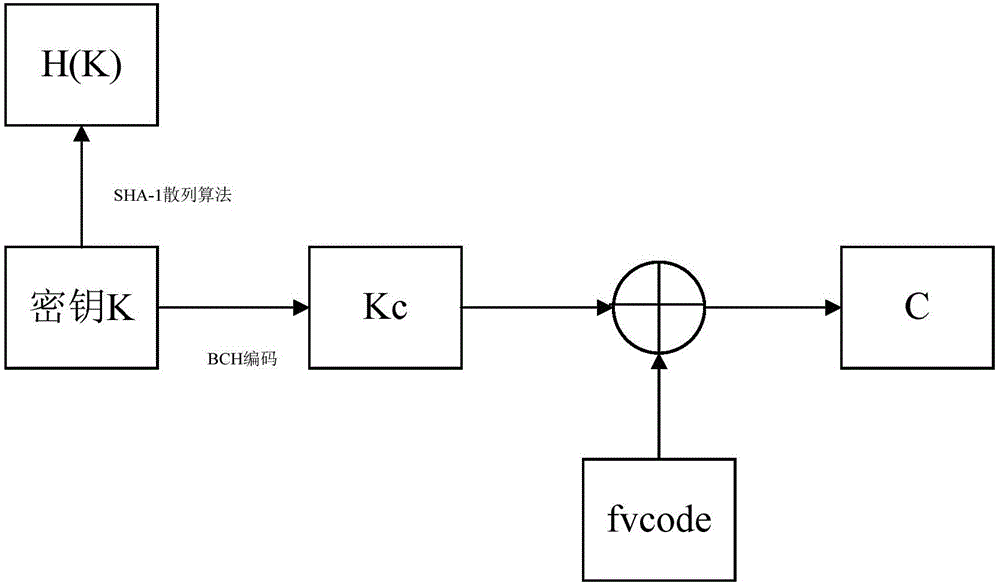
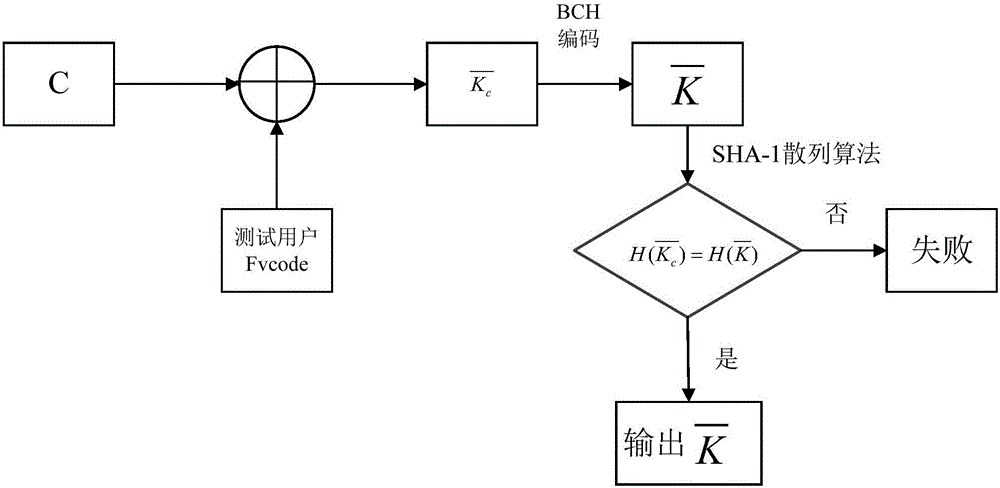
Finger vein encryption method
A technology of finger veins and encryption methods, which is applied in the field of pattern recognition, can solve problems such as performance evaluation of biometric encryption systems, and achieve good classification effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
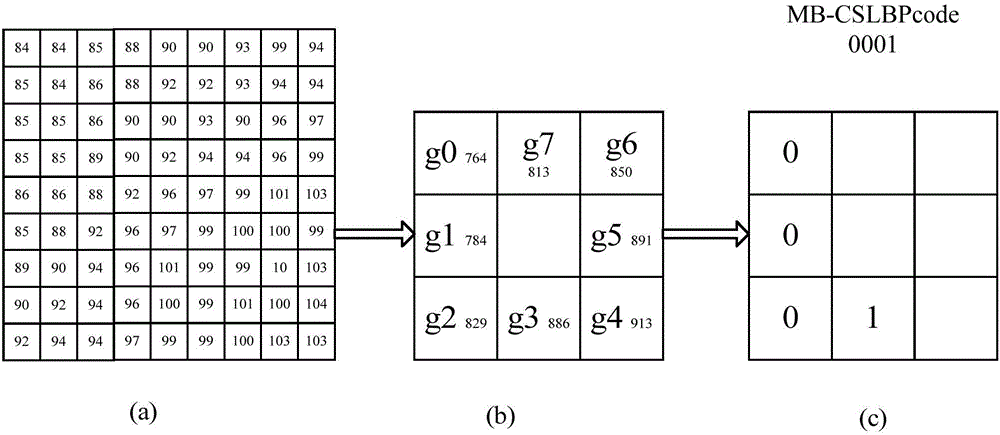
[0022] 1. Multi-scale block central symmetric local binary mode (MB-CSLBP) encodes the image
[0023]
[0024]
[0025]
[0026] Wherein, L represents the side length of the square area of the pixel block. g k Represents the gray value of a single pixel, B is the sum of the pixel gray values of the i-th square area, and the encoding obtained by replacing the gray average value of the pixel gray value of the square area with the sum is the same. s(x) is a binarization function, T is a threshold value, and x represents the difference between the sum of pixel gray values of two selected square areas.
[0027] figure 1 The encoding process of MB-CSLBP operator is given.
[0028] figure 1 In this method, the sum of the gray value of a square area with a side length of 3 is regarded as the gray value of a pixel, and compared with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com