Task execution method based on fingerprint, and mobile terminal
A mobile terminal and task execution technology, applied in the field of communication, can solve the problems of insufficient fingerprints and low recognition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
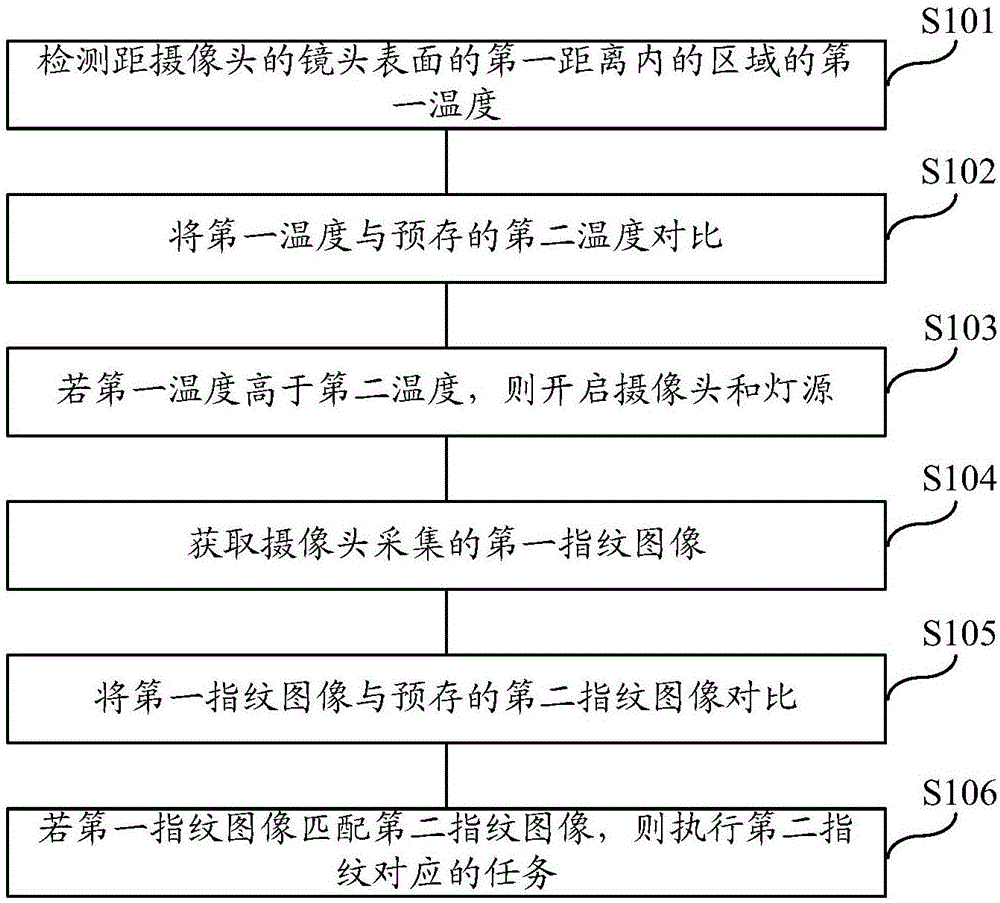
[0018] The first embodiment of the present invention discloses a fingerprint-based task execution method. This method is used for a mobile terminal with a camera and a light source. Such as figure 1 As shown, the method includes the following steps:
[0019] Step S101: Detect a first temperature of an area within a first distance from a lens surface of a camera.
[0020] Specifically, the mobile terminal may be provided with an infrared detector to detect the first temperature. The first distance can be set by the mobile terminal system or the user. The smaller the first distance is, the closer the finger of the mobile terminal user is to the lens surface of the camera if the camera and the light source are to be turned on.
[0021] Step S102: comparing the first temperature with the pre-stored second temperature.
[0022] The second temperature can be set by the mobile terminal system or the user, and is generally close to the temperature of the human body.
[0023] Ste...
no. 2 example
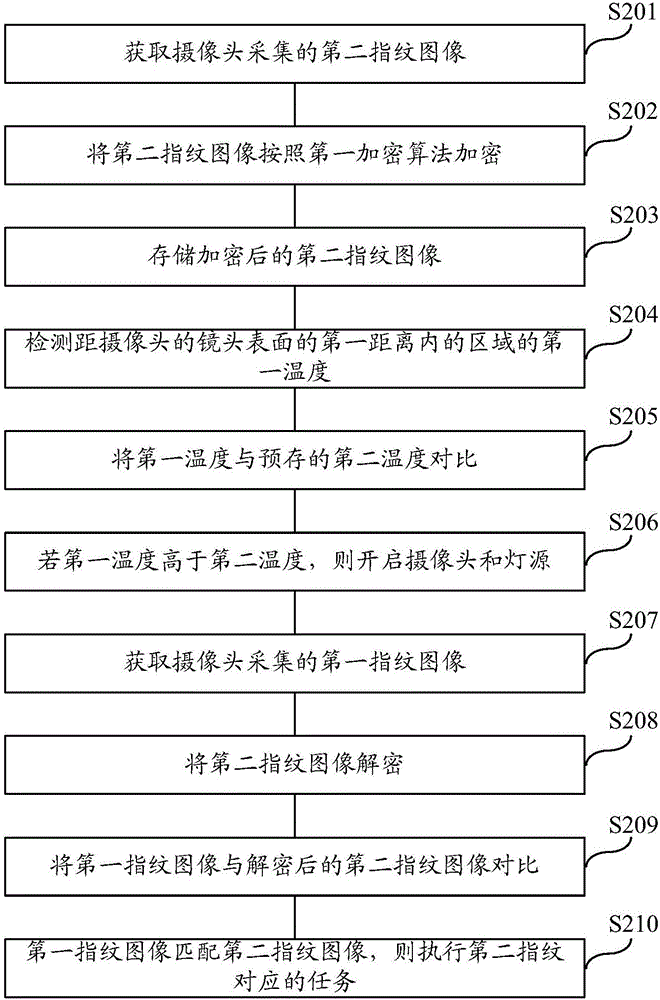
[0035] The second embodiment of the present invention discloses a fingerprint-based task execution method. This method is used for a mobile terminal with a camera and a light source. Such as figure 2 As shown, the method includes the following steps:
[0036] Step S201: Obtain a second fingerprint image collected by a camera.
[0037] Generally speaking, the camera can collect multiple second fingerprint images, and use the multiple second fingerprint images as comparison images for comparison of fingerprints, so that the second fingerprint images can contain more comprehensive fingerprint information.
[0038] Step S202: Encrypt the second fingerprint image according to the first encryption algorithm.
[0039] Through this step, the second fingerprint image can be encrypted to improve the security of the second fingerprint image and prevent the second fingerprint image from being stolen by others.
[0040] Step S203: storing the encrypted second fingerprint image.
[00...
no. 3 example
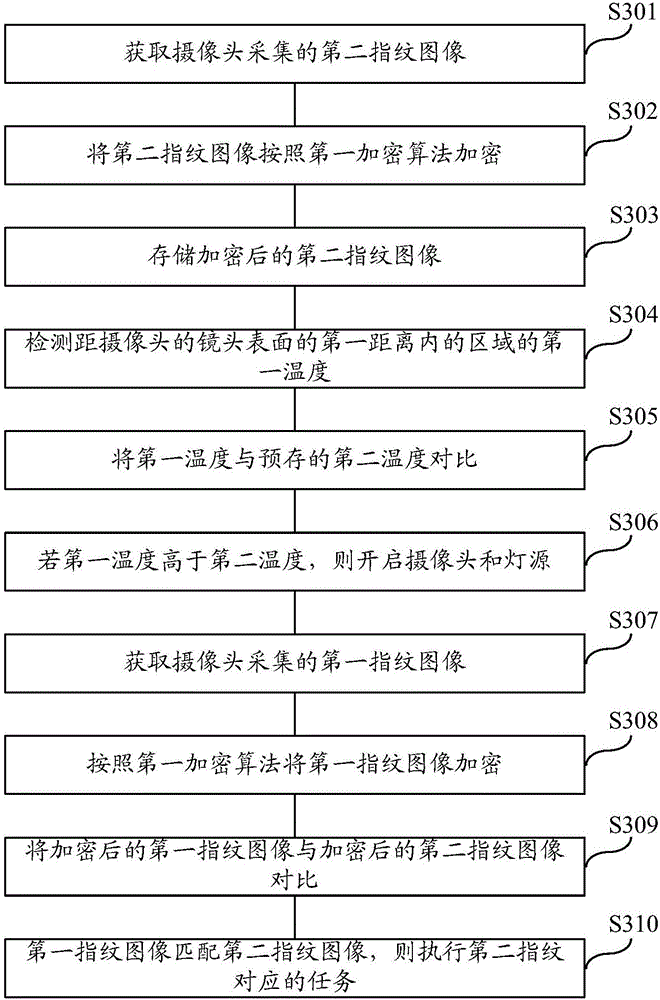
[0058] The third embodiment of the present invention discloses a fingerprint-based task execution method. This method is used for a mobile terminal with a camera and a light source. Such as image 3 As shown, the method includes the following steps:
[0059] Step S301: Obtain a second fingerprint image collected by a camera.
[0060] Generally speaking, the camera can collect multiple second fingerprint images, and use the multiple second fingerprint images as comparison images for comparison of fingerprints, so that the second fingerprint images can contain more comprehensive fingerprints.
[0061] Step S302: Encrypt the second fingerprint image according to the first encryption algorithm.
[0062] Through this step, the second fingerprint image can be encrypted to improve the security of the second fingerprint image and prevent the second fingerprint image from being stolen by others.
[0063] Step S303: storing the encrypted second fingerprint image.
[0064] The encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com