Python code obfuscation method based on control flow and appearance obfuscation
A code obfuscation and control flow technology, applied in the field of Python code obfuscation, can solve the problems of core code theft or tampering, it is difficult to protect the intellectual property rights of the code, etc., to achieve complex logical structure, increase the difficulty of reading and understanding, and protect software copyright. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
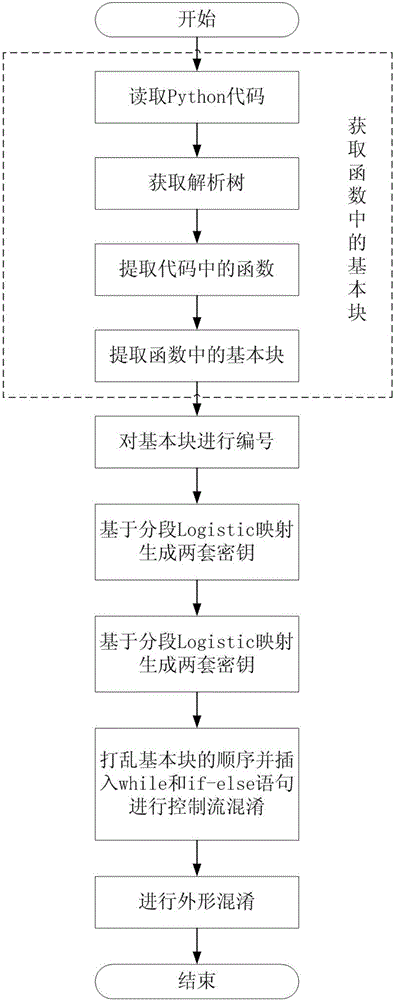
[0033] In this embodiment, a kind of Python code obfuscation method based on control flow and appearance confusion, according to figure 1 Follow the steps shown:
[0034] Step 1. First, read the Python code that needs to be confused; second, use the built-in functions in the Python language to obtain the parse tree of the code; then, divide all the functions in the Python code with the start and end of a function as the unit, Get several individual functions;
[0035] Step 2. For any single function fun, such as figure 2 As shown in the figure, several consecutively executed codes in the function body are divided, and several basic blocks are obtained and numbered sequentially, recorded as B={b 1 ,b 2 ,...,b i ,...,b n}; figure 2 The number of basic blocks in n=4, so get B={b 1 ,b 2 ,b 3 ,b 4}; b i Indicates the i-th basic block; the i-th basic block b i The code in has only one entry and one exit; 1≤i≤n; to extract the basic blocks in the function;
[0036] Ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com