Password management method, system and intelligent terminal
A password management and intelligent terminal technology, applied in the field of data security, can solve the problems of password leakage, poor confidentiality, poor convenience, etc., and achieve the effect of correcting the mapping relationship and improving the password management method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
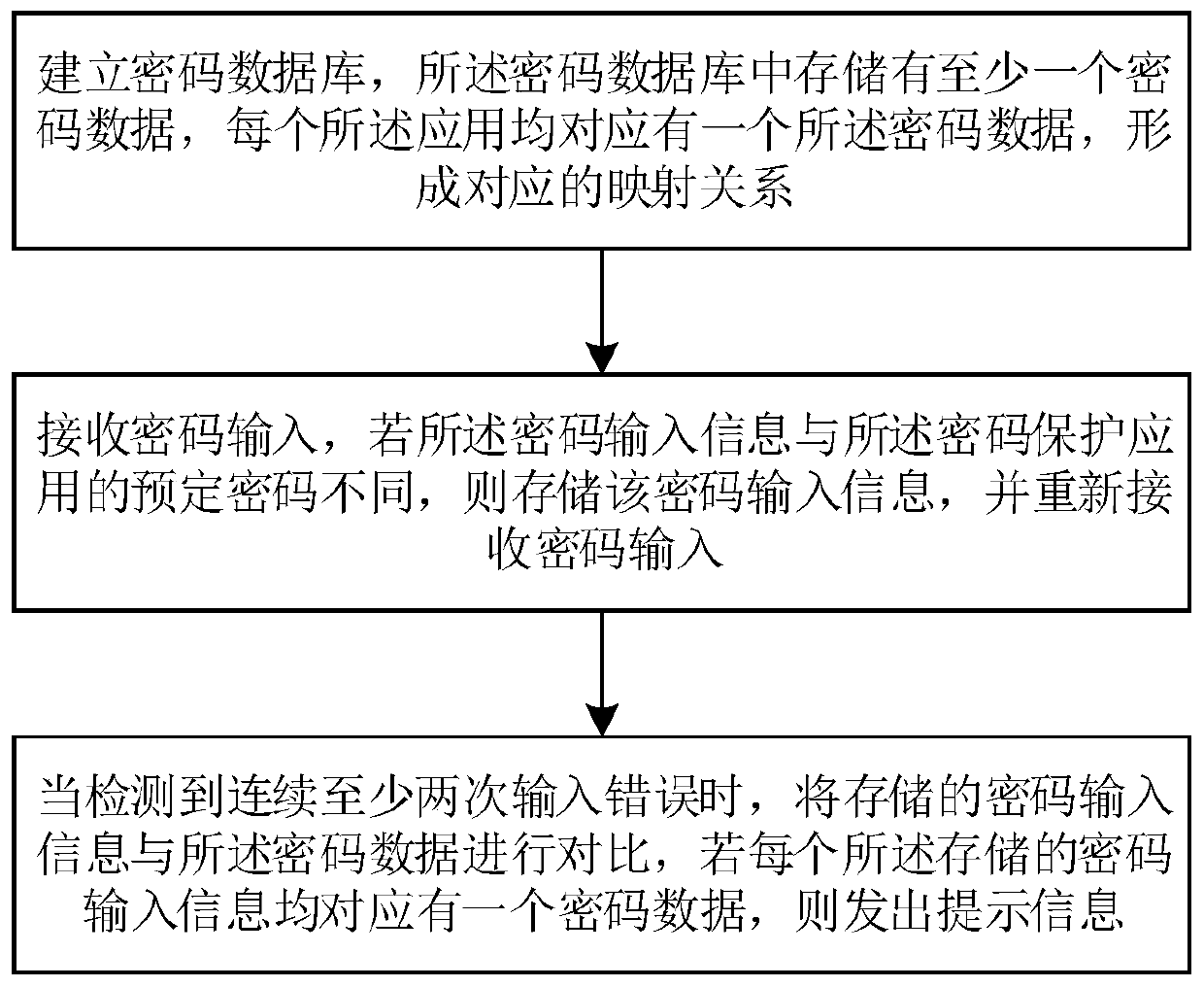
[0031] figure 1 Shown is the flow chart of the password management method of the present invention, which is applied to a smart terminal, and the smart terminal has a password-protected application, and the application has a predetermined password, which is characterized in that it includes the following steps:
[0032] Establishing a password database, at least one password data is stored in the password database, each of the applications corresponds to one password data, forming a corresponding mapping relationship;
[0033] Receiving a password input, if the password input information is different from the predetermined password of the password protection application, storing the password input information, and receiving the password input again;
[0034] When at least two consecutive input errors are detected, the stored password input information is compared with the password data, and if each of the stored password input information corresponds to a password data, a prom...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com