Network information auditing method and system based on ciphertext retrieval
A network information and ciphertext technology, applied in the field of information security, can solve problems such as attacks, inefficient communication, and user data leakage, and achieve the effects of avoiding inefficiency, convenient review, and strong security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The features of various aspects of the present invention will be described in detail below without limiting the scope of the present invention in any way.
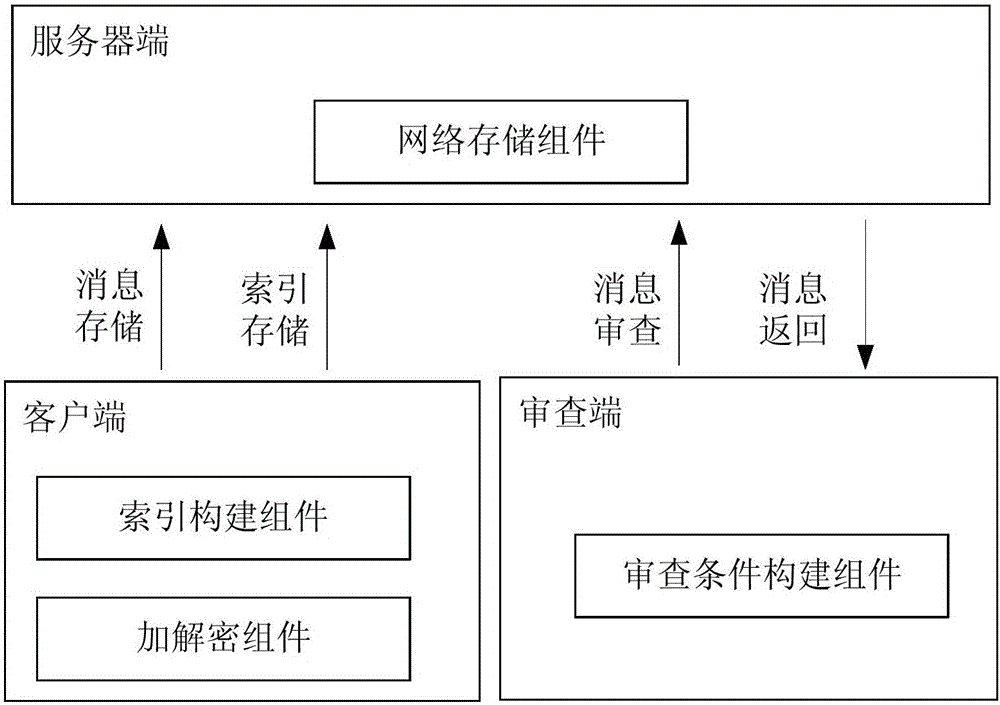
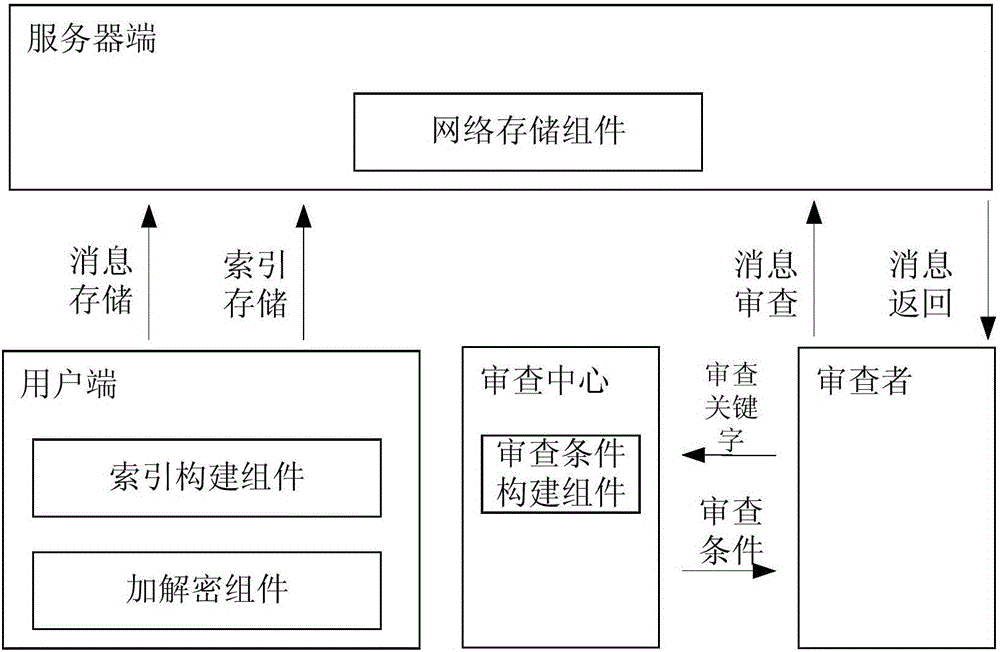
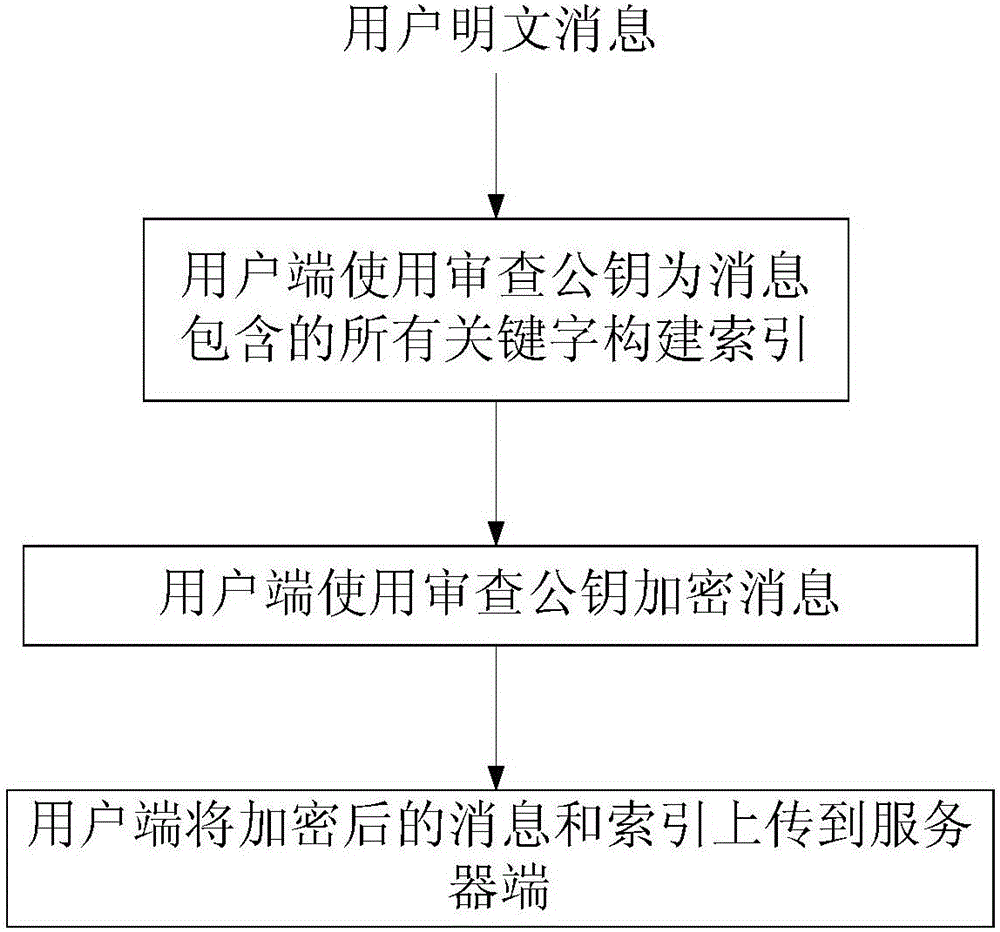
[0037] An information review method based on ciphertext retrieval in this embodiment is implemented through the client, the review terminal and the server, including user information storage processes (such as image 3 ), and the review process (such as Figure 4 shown), specifically include the following steps:
[0038] A. The examiner registers a pair of public and private keys PK and SK: {PK, SK}=KEYGEN(), publicly releases the public key PK, and keeps the private key SK by itself;
[0039] B. Suppose the message body that the user needs to save is M, and the user builds an index I for all keywords contained in M M ;
[0040] C. The user uses PK to encrypt M to obtain ciphertext C M =PENC(M,PK);
[0041] D. The user will C M and I M upload to the server;
[0042] E. Set the keyword to be reviewed as W, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com