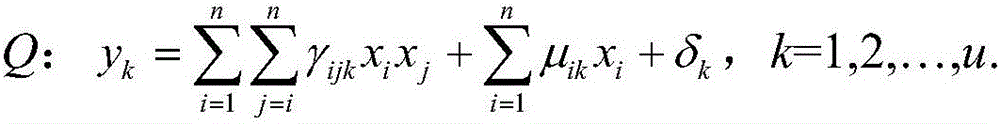Proxy re-signature method based on IP signature
A re-signature and manager technology, applied in key distribution, can solve the problem of poor anti-quantum attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The comparison table of the meanings of variables and operation symbols in the specific embodiment.
[0068]
[0069] In this embodiment, based on the proxy re-signature method of IP signature, Alice is selected as the trustee, that is, the original signer; Bob is the delegator, that is, the owner of the converted signature. Specific steps are as follows:
[0070] Step 1: Generate system parameters.
[0071] The system administrator chooses order 2 p The finite field K of , p is a positive integer selected by the system administrator. The system administrator chooses three positive integers n, u and q;
[0072] The system administrator chooses a collision-resistant hash function H(x):{0,1} in cryptography * →{0,1} q ;
[0073] The system administrator chooses a system Q of quadratic polynomial equations Q with n variables, which is of the form:
[0074]
[0075] The system administrator publishes the system-generated parameters (n, u, q, K, Q, H(x)).
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com