Privacy character information encryption inquiry method and system
A character information, encrypted query technology, applied in the field of private character information encrypted query methods and systems, can solve the problems of reducing the flexibility and security of the method, and achieve the effects of coordinating security and efficiency and improving data query efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
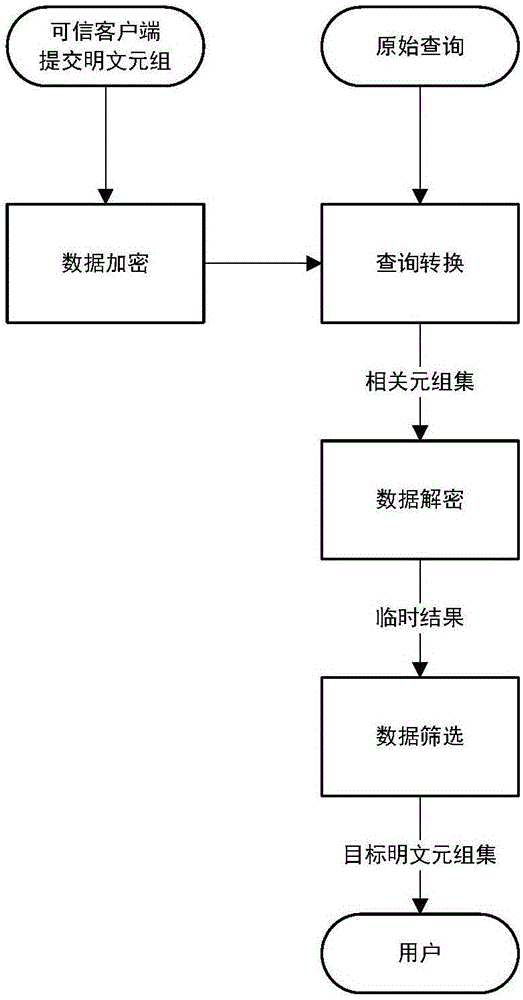
[0117] A private character information encryption query method, comprising the following steps:
[0118] (1) Data encryption: the plaintext tuple submitted by the trusted client is converted into a ciphertext tuple; the plaintext tuple contains a privacy field, and its value is preferably a character string; the ciphertext tuple includes ciphertext data and index data;
[0119] The conversion of the private character string in clear text form submitted by the trusted client into cipher text data is specifically:
[0120] For contact information in plain text R(A 1 ,A 2 ,...,A r ,…), where A r It is a mobile phone number in plain text, a string type, consisting of 11 characters, of which the first 2 characters can only be 13, 15, 17 or 18, and the remaining 9 characters can be any value from characters 0 to 9. The encrypted ciphertext tuple is where R E The new ciphertext field in Its type is preferably binary, used to store the ciphertext data encrypted by the entire...
Embodiment 2
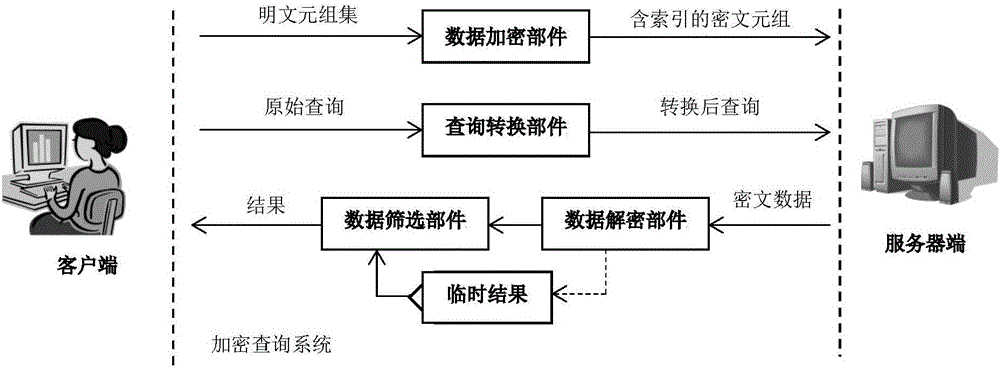
[0166] An encrypted query of private character information, including a data encryption component, a query conversion component, a data decryption component, and a data screening component;
[0167] The data encryption component is used to convert the plaintext tuple submitted by the trusted client into a ciphertext tuple; the plaintext tuple contains a privacy field, and its value is preferably a character string; the ciphertext tuple includes a ciphertext data and index data;
[0168] The query conversion component is used to convert the original query condition into the index query condition, and use the tuple set composed of the ciphertext tuple whose index data satisfies the index query condition as the related ciphertext tuple set, so that the related ciphertext tuple set The text tuple set is a superset of the ciphertext tuple set converted from the original query result;
[0169] The query conversion component includes a precise query subcomponent, a fuzzy query subco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com