Method and device for monitoring operating system behaviors
An operating system and behavior technology, applied in the computer field, can solve the problem that third-party security software cannot monitor the operating system, and achieve the effect of defending against malicious program attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
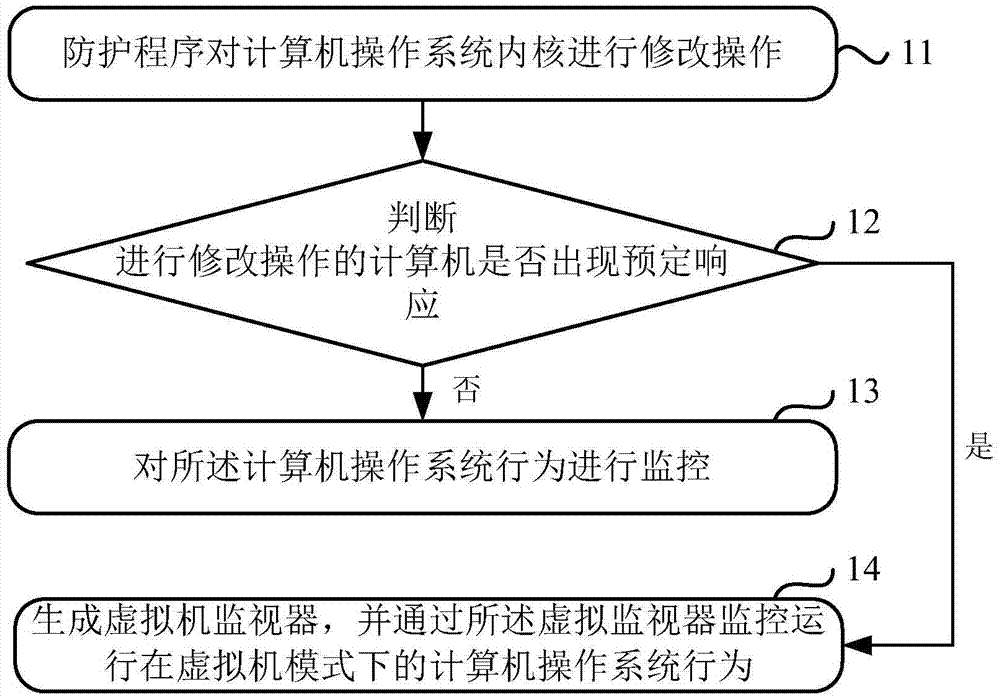
[0025] Embodiment 1 of the present application provides a method for monitoring the behavior of the operating system to solve the problem that third-party security software cannot monitor the behavior of the operating system because the computer operating system prohibits third-party software from modifying the operating system kernel. question.
[0026] The execution subject of the method for intercepting a system call provided in the embodiment of the present application may be, but not limited to, at least one of terminal devices such as a tablet computer and a personal computer (Personal Computer, PC). In addition, the subject of execution of the method may also be an application program installed on the terminal device.
[0027] For the convenience of description, the implementation of the method will be introduced below by taking the execution subject of the method as the protection program as an example. It can be understood that the fact that the execution subject of ...
Embodiment 2
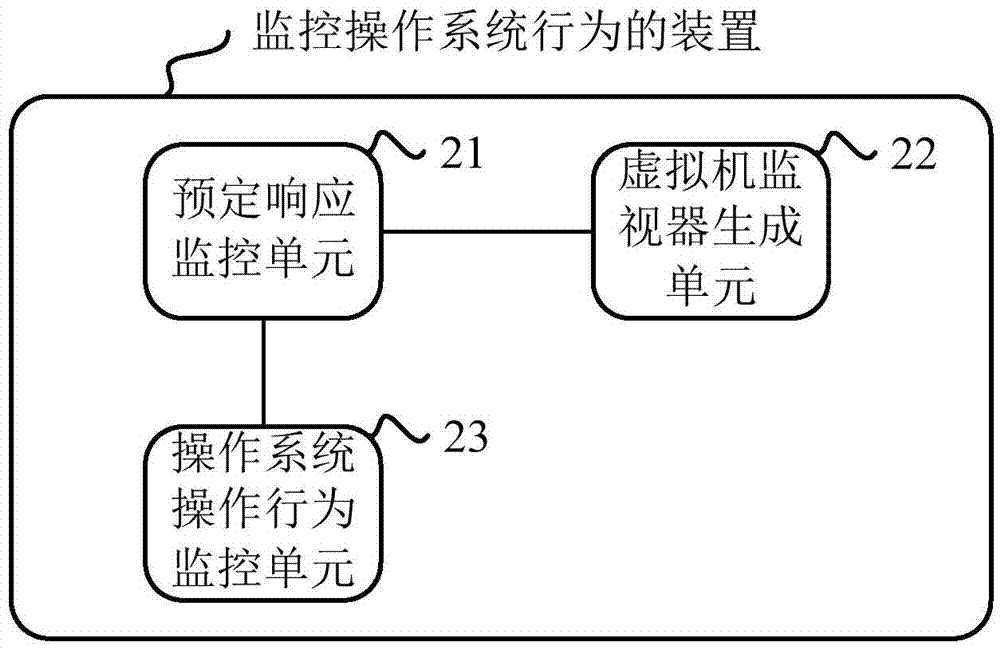
[0053] Embodiment 2 of the present application provides a device for monitoring the behavior of the operating system, which is used to solve the problem that the third-party security software cannot monitor the behavior of the operating system because the computer operating system prohibits third-party software from modifying the operating system kernel. question. The specific structural diagram of the device is shown in figure 2 As shown, it includes: a predetermined response monitoring unit 21 , a virtual machine monitor generating unit 22 and an operating system operation behavior monitoring unit 23 .
[0054] Wherein, the predetermined response monitoring unit 21 is used to modify the operating system kernel of the computer, and determine whether the computer performing the modification operation has a predetermined response;
[0055] The virtual machine monitor generation unit 22 is configured to generate a virtual machine monitor by performing a hardware virtualization...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com