Weak password detection method, apparatus and system
A detection method and detection device technology, applied in the field of security detection, can solve the problems of low identification efficiency of weak passwords, achieve the effect of improving the collision hit rate and identification efficiency, and solving the low identification efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
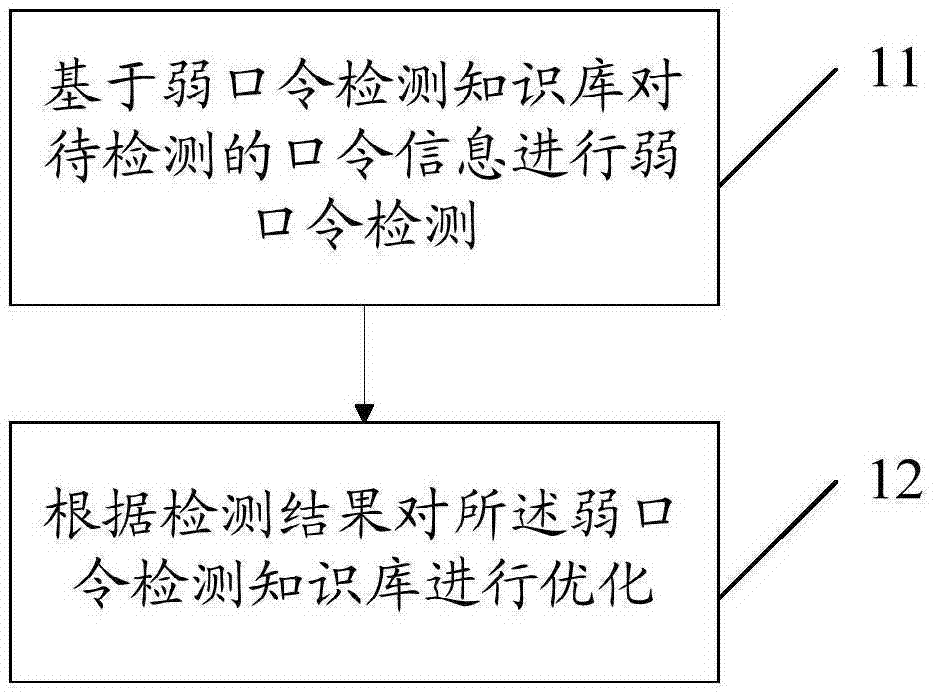
[0057] Such as figure 1 As shown, the weak password detection method provided by Embodiment 1 of the present invention includes:
[0058] Step 11: Perform weak password detection based on the weak password detection knowledge base for the password information to be detected;
[0059] Step 12: Optimizing the weak password detection knowledge base according to the detection results.
[0060] The weak password detection method provided in Embodiment 1 of the present invention performs weak password detection on the password information to be detected based on the weak password detection knowledge base, and then optimizes the weak password detection knowledge base according to the detection results for subsequent weak password identification , improve the collision hit rate and recognition efficiency of subsequent weak password detection, and solve the problem of low efficiency of weak password recognition in the prior art.
[0061] Embodiment 1 of the present invention provides...
Embodiment 2
[0119] Such as Figure 5 As shown, the weak password detection device provided by Embodiment 2 of the present invention includes:
[0120] A detection module 51, configured to detect weak passwords based on the weak password detection knowledge base for the password information to be detected;
[0121] An optimization module 52, configured to optimize the weak password detection knowledge base according to the detection result.
[0122] The weak password detection device provided in Embodiment 2 of the present invention performs weak password detection on the password information to be detected based on the weak password detection knowledge base, and then optimizes the weak password detection knowledge base according to the detection results for subsequent weak password identification. , improve the collision hit rate and recognition efficiency of subsequent weak password detection, and solve the problem of low efficiency of weak password recognition in the prior art.
Embodiment approach
[0123] Embodiment 2 of the present invention provides two specific implementation modes for the function of the optimization module 52, as follows:
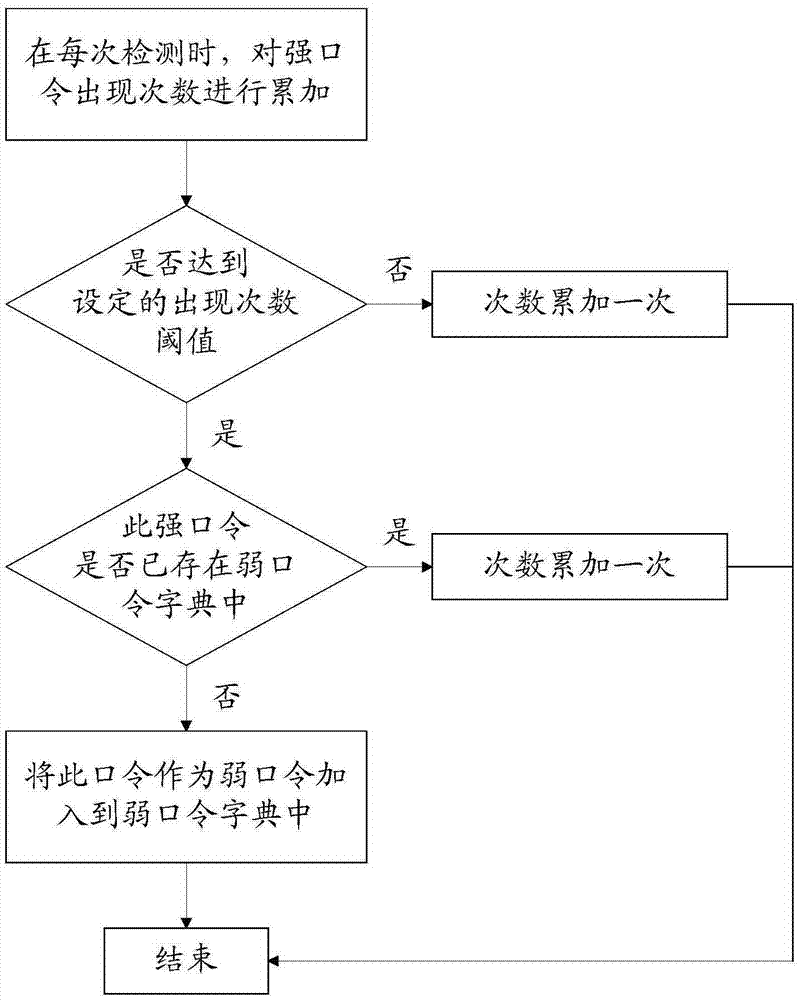
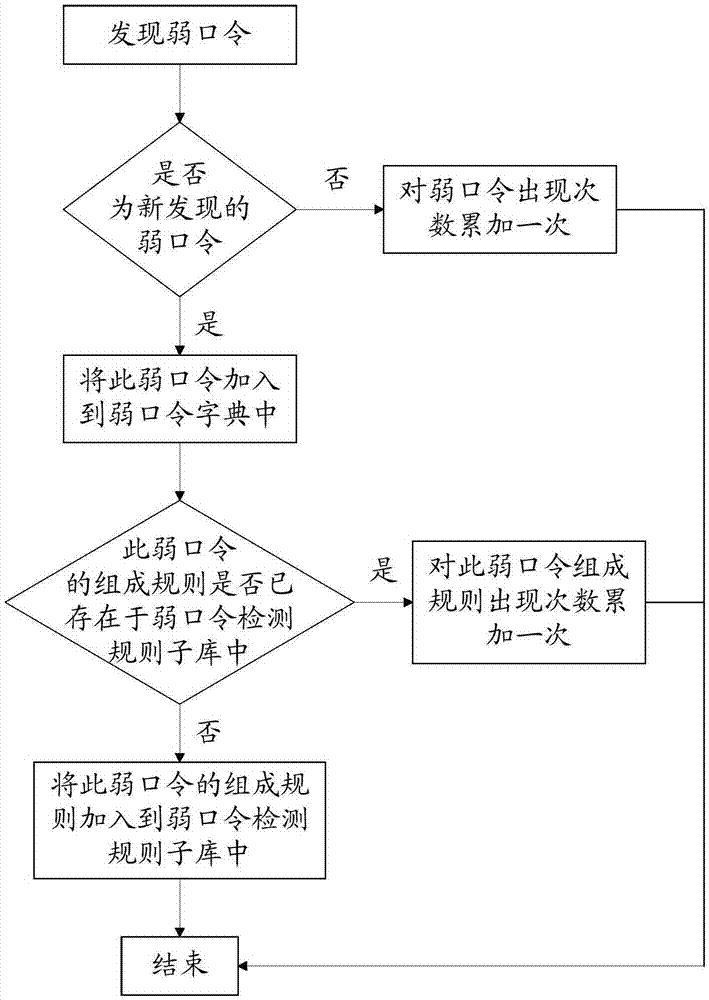
[0124] In the first type, the optimization module includes: a counting submodule, configured to count the weak passwords and corresponding weak password composition rules when the detection result indicates that a weak password is detected; a sorting submodule is configured to count the weak passwords according to The counting result sorts the calling priority of the weak passwords and corresponding weak password composition rules.
[0125] In the second type, the optimization module includes: an extension submodule, configured to expand the weak password dictionary of the weak password detection knowledge base according to the detection result.
[0126] It should be noted that the first and second manners may coexist or exist independently, which is not limited here.
[0127] Specifically, Embodiment 2 of the present invention ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com