Safety verification method, platform, device and system
A security verification and platform technology, applied in the field of security verification methods and systems, can solve the problems of biometric information being stolen or forged and difficult to detect, hidden dangers, and high hardware requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
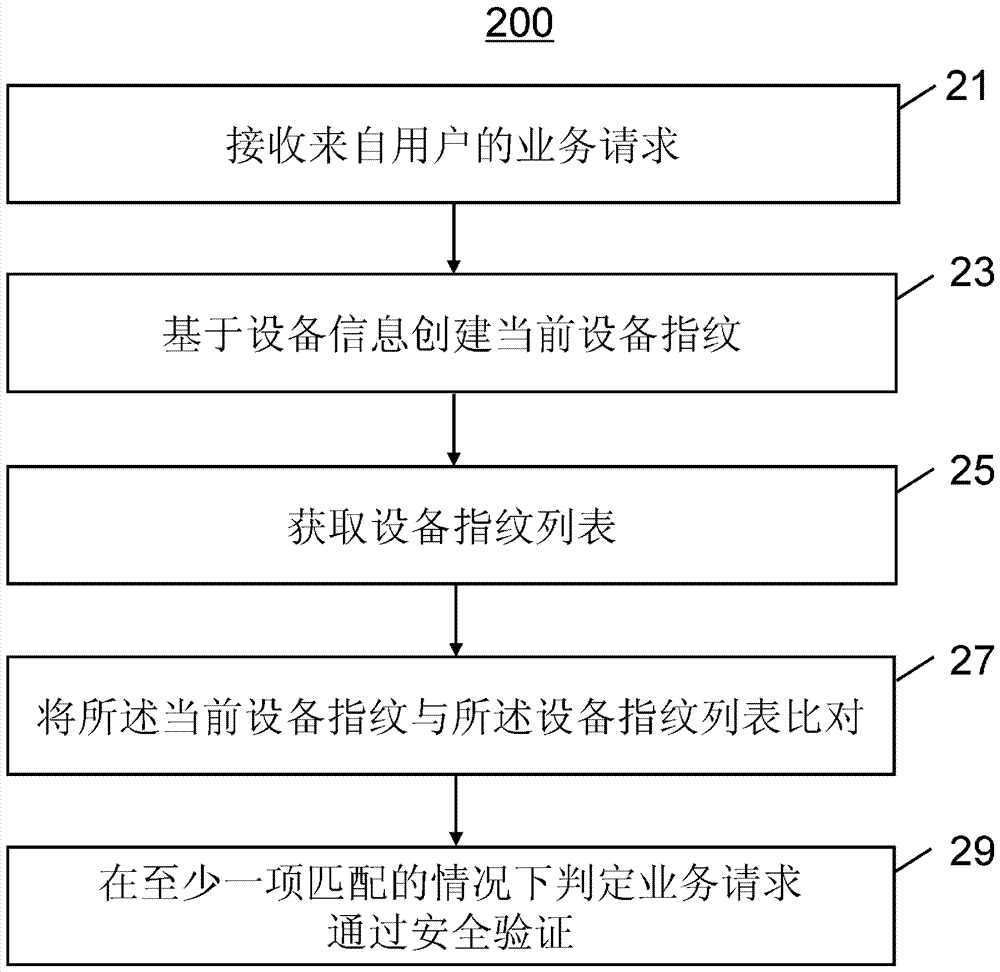
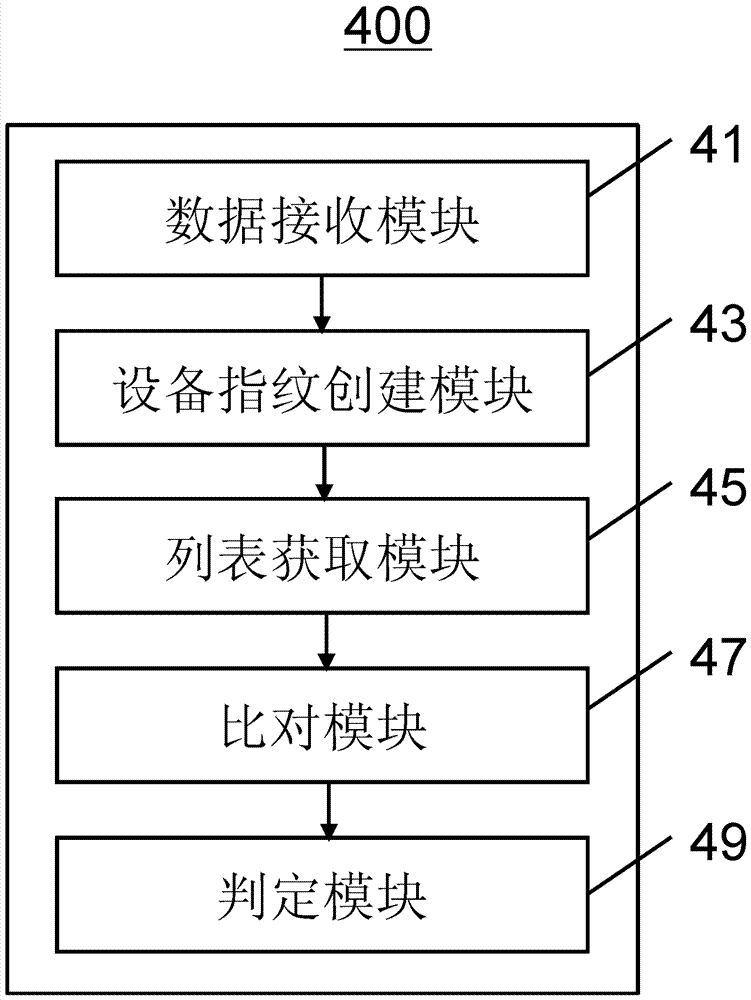
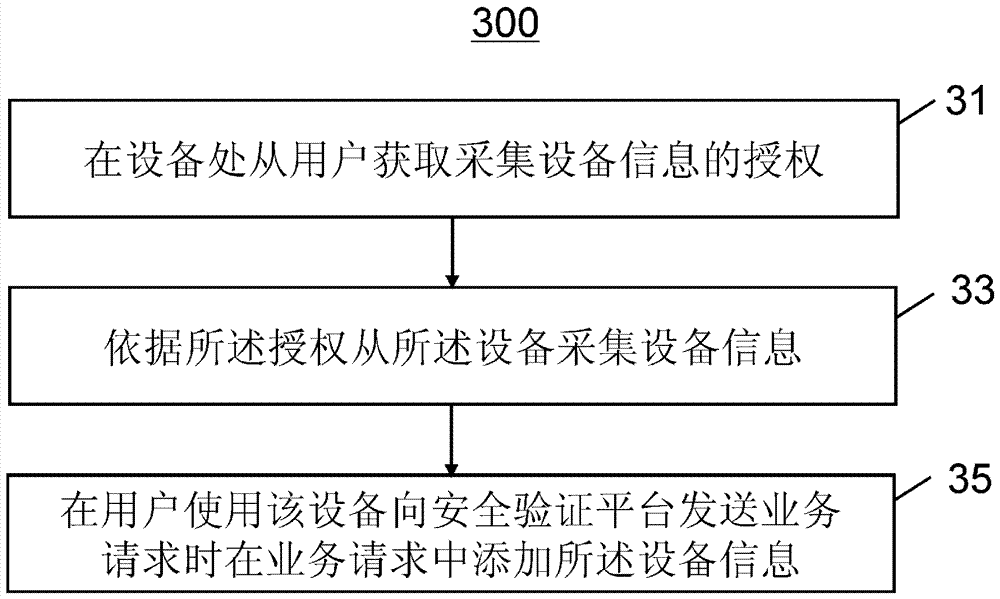
[0032] Illustrative examples of the invention will now be described with reference to the drawings, wherein like reference numerals refer to like elements. Each example described below helps those skilled in the art to thoroughly understand the present invention, and each example is intended to be an illustration rather than a limitation. The diagrams of the components, components, modules, devices and equipment bodies in the figure only schematically indicate the existence of these components, components, modules, devices and equipment bodies, and also indicate the relative relationship between them, but are not intended to limit their specific Shape; the relationship of each step in the flow chart is not limited to the order given, and can be adjusted according to actual applications without departing from the scope of protection of the present application.
[0033] figure 1 is a schematic block diagram of a security verification system according to an example of the presen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com