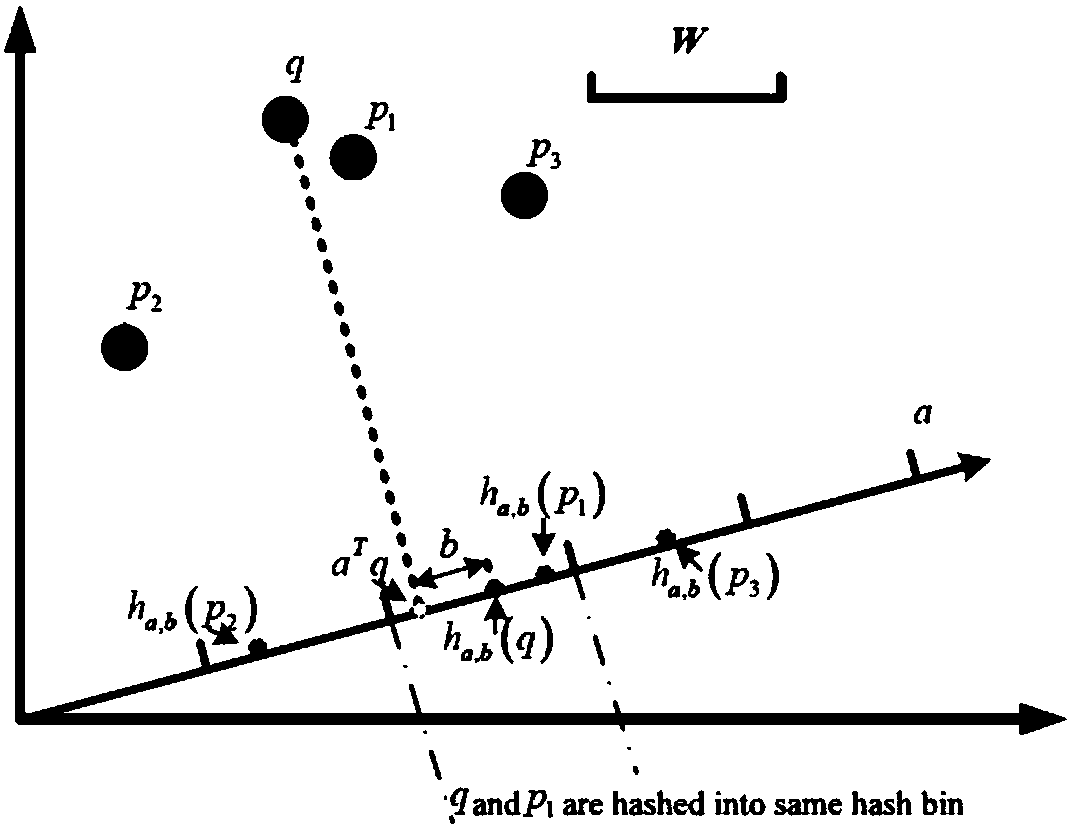
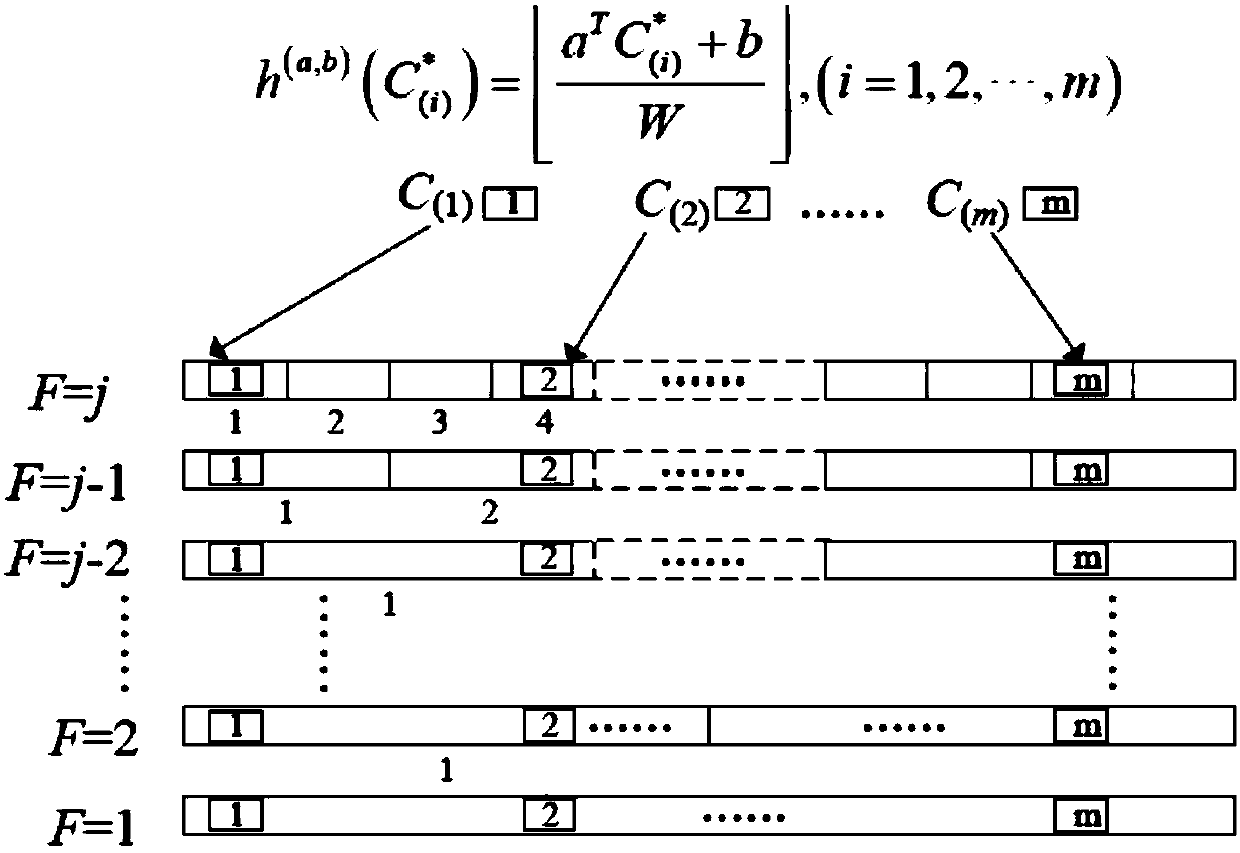
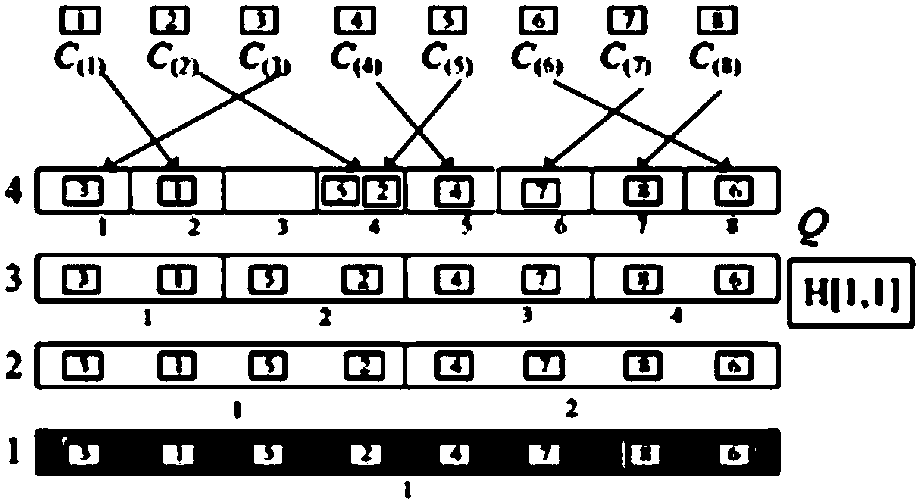
Network traffic abnormality rapid detection method based on multilayer partial sensitive hash table
A sensitive hash table and network traffic technology, applied in the field of computer technology and network, can solve the problem of high time cost of SVD, achieve the effect of reducing the overall time complexity, reducing time complexity, and realizing rapid detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] 1) Questions
[0051] Step 1: System Modeling
[0052] Assuming that the network is composed of N nodes, the present invention models the flow data into a flow matrix The rows of the traffic matrix X represent the traffic data of a single OD (source node and destination node) pair in each time slot, the columns of the traffic matrix X represent the traffic data of all OD pairs in the same time slot, and n represents the total number of time slots.
[0053] Due to the characteristics of temporal stability and spatial correlation of flow data, normal flow data will be located in a low-dimensional linear subspace to form a low-rank matrix, and abnormal flow data will be located outside this low-dimensional linear subspace to form an abnormal matrix. Therefore, the anomaly detection problem is attributed to the following constrained optimization problem:
[0054]
[0055] where S is the anomalous matrix, L is the low-rank approximation of the matrix X-S, k is the trun...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com