Communication with permanent security from short-term secure encrypted quantum communication
A short-term security and quantum technology, applied in the field of quantum cryptography, can solve the problems that permanent security cannot be established, and achieve the effects of large encoder and receiver noise, high channel bit error rate, and large channel loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
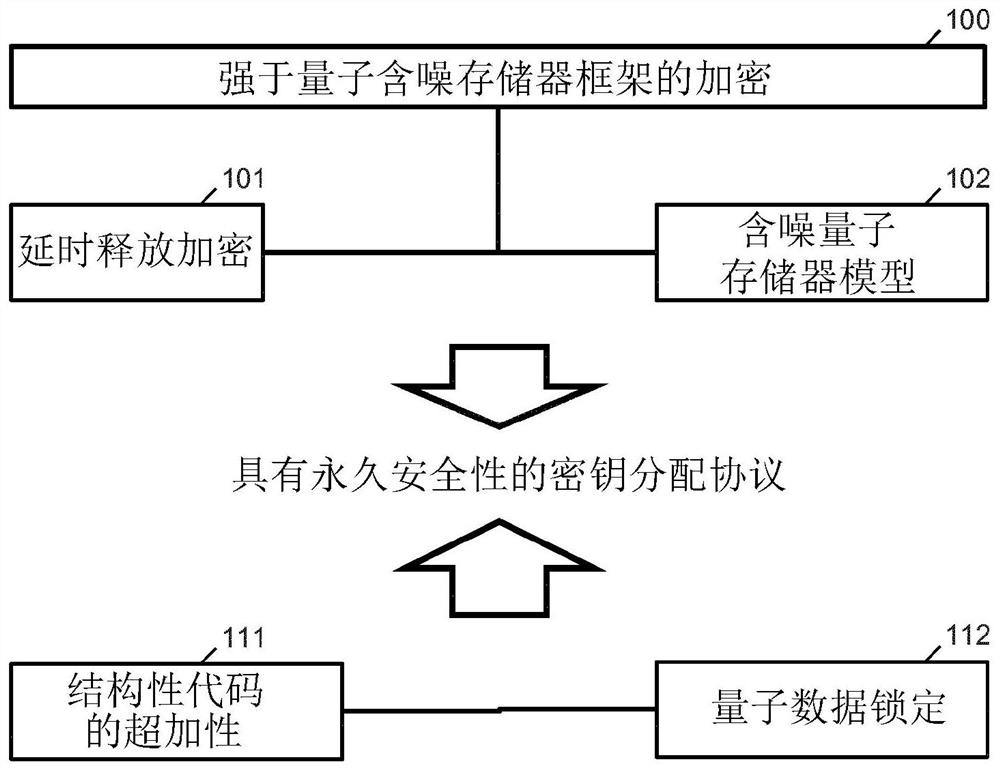
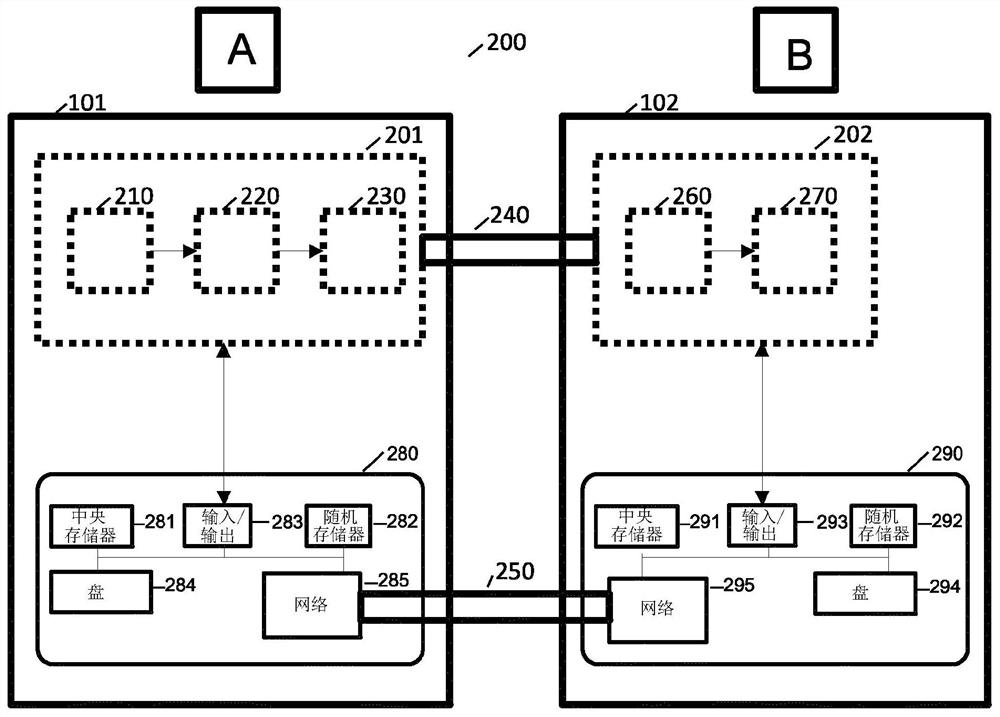
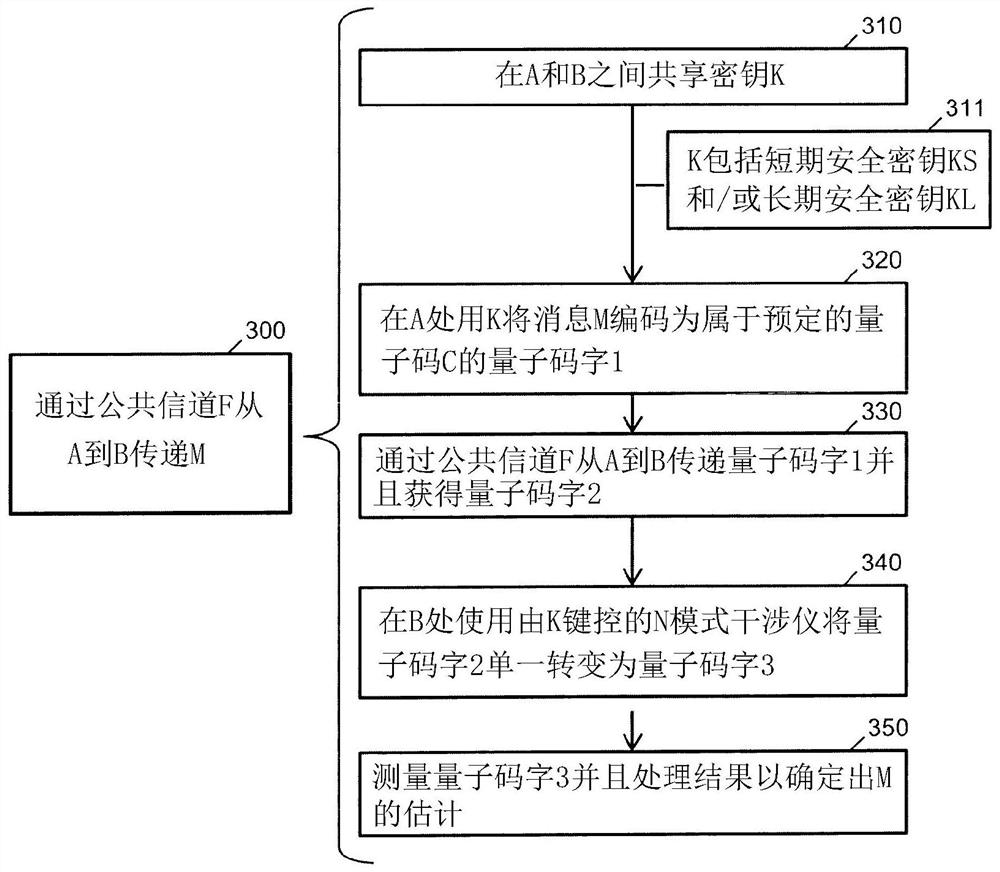
[0065] According to an aspect of the invention, a "hybrid" security model (ie combining classical and quantum cryptography in a specific manner) is disclosed. Embodiments of the disclosed invention, for example, enable the establishment of secure two-party cryptographic primitives. Such progressions include, for example, bit commitments, coin tosses, or XOR calculations. Relatedly, such two-party cryptographic protocols can be used to establish any secure multi-party protocol.
[0066] Further, a classical message is long-term secure if the information accessible to any eavesdropper E about the message can be capped at an arbitrarily chosen amount close to zero, and if said bound always remains in effect.
[0067] Further, if the accessible information about any eavesdropper E of a message can be bounded by an arbitrarily chosen amount close to 0, and if this bound is valid during an interval of at least tau duration, then a classical message is at least tau The period is sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com