A Maintenance Method of Distributed Dynamic Layer 2 Forwarding Table
A forwarding table and distributed technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as low utilization of external memory space, low read and write speed, and limited BRAM resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
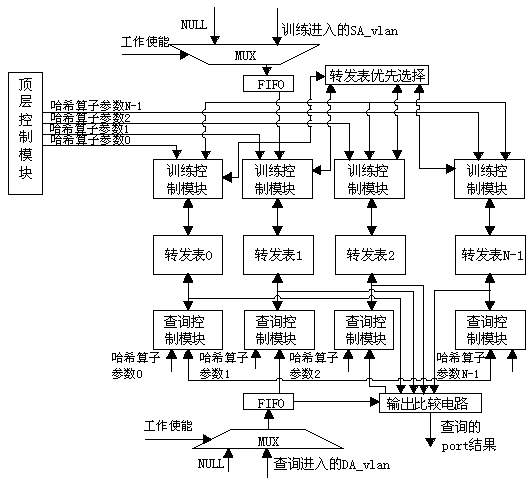
[0070] combined with figure 1 Shown, a kind of maintenance method of distributed dynamic two-layer forwarding table, comprises the training of forwarding table, the query of forwarding table and the aging of forwarding table, the training of described forwarding table comprises steps:
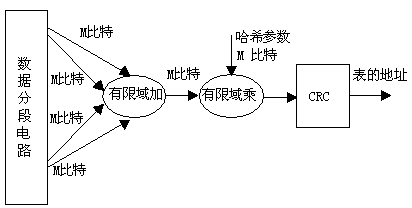
[0071] S1) When the FPGA is powered on and started, N mutually different true random numbers R are externally input, expressed as GF(R) in the finite field, and stored in the register of the top-level control module, and the register is connected to the hash calculation module Input port, said N is the number of forwarding tables in the FPGA internal BRAM, and the entries of said forwarding tables include:
[0072] MAC: stored source address SA;
[0073] vlan: the vlan ID associated with the MAC;
[0074] port: the port number associated with the MAC;
[0075] vld: the effective flag of the entry, "1" means valid, "0" means invalid;
[0076] age: counting item, used to record the aging coun...
Embodiment 2
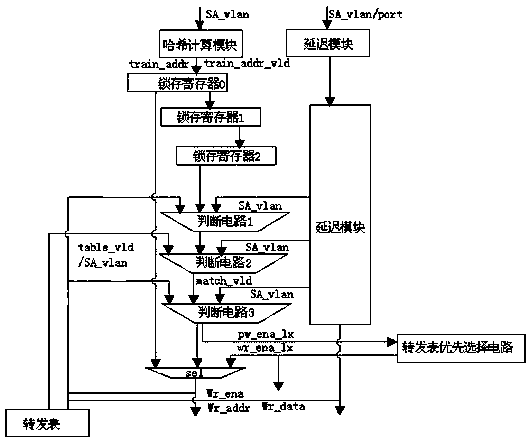
[0084] On the basis of Example 1, in conjunction with the attached figure 1 and image 3 As shown, the specific steps of S4) are: every other clock cycle, the hash calculation module will output a training address train_addr and a valid training address train_adr_vld, if train_adr_vld=0, do not take any action, when train_adr_vld=1, SA_vlan The port number and port will be passed in the pipeline read-write circuit, and the entry is read through the training address train_addr, and the SA_vlan corresponding to this address is compared with the entry:
[0085] A) The read table entry is not occupied, that is, the vld of the table entry=0, then the training address train_addr and the effective training address train_adr_vld are passed down as they are;
[0086] B) The table entry read has been occupied, but the content of the table entry MAC does not match the SA_vlan that needs to be trained, then the training address is valid train_adr_vld=0, and no action is taken;
[0087] ...
Embodiment 3
[0097] On the basis of Example 1, in conjunction with the attached figure 1 and Figure 4 As shown, an aging control circuit is also included, the aging control circuit is provided with an age address age_addr and an aging cycle age_period, and the working process of the aging control circuit includes:
[0098] M1): Initialize age address age_addr=0;
[0099] M2): Determine whether the age address age_addr is greater than the depth table_deep of the forwarding table, if greater, end the aging process; otherwise enter the next step;
[0100] M3): Read the age address age_addr, obtain the age count in the entry, and subtract "1" from it. If age≤1, set the effective flag vld of the entry to "0", that is, the entry in the current forwarding table The status is writable;
[0101] M4): Write the age after subtracting "1" into the age address age_addr;
[0102] M5): add 1 to the age address: age_addr=age_addr+1, return to step M2).
[0103] After the entries in the forwarding ta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com