Distributed identity authentication method and system
An identity authentication and distributed technology, applied in the field of big data security, to achieve the effect of reliable authentication, high authentication efficiency, and reliable identity authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
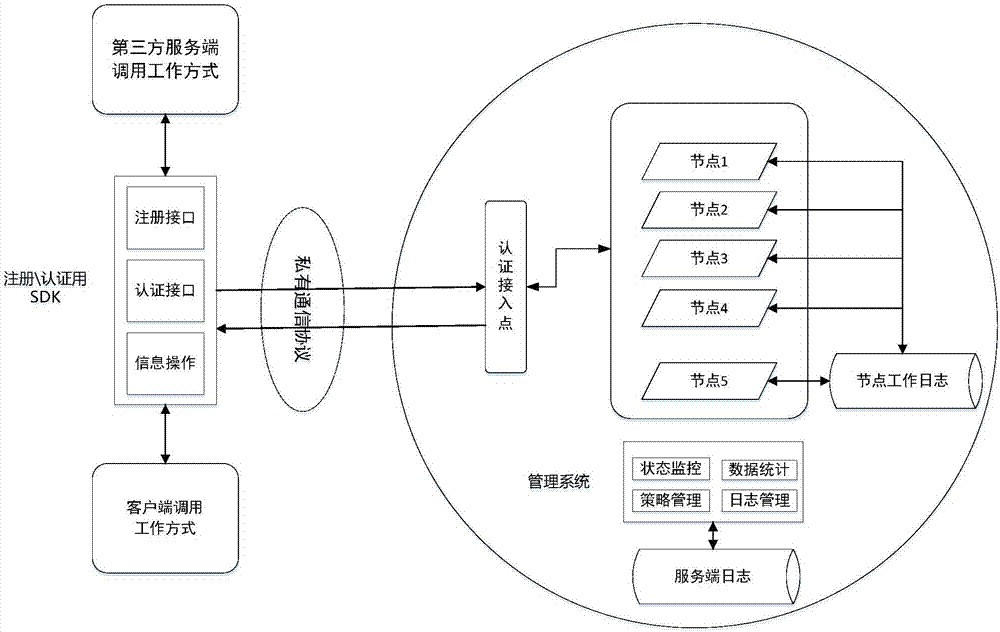
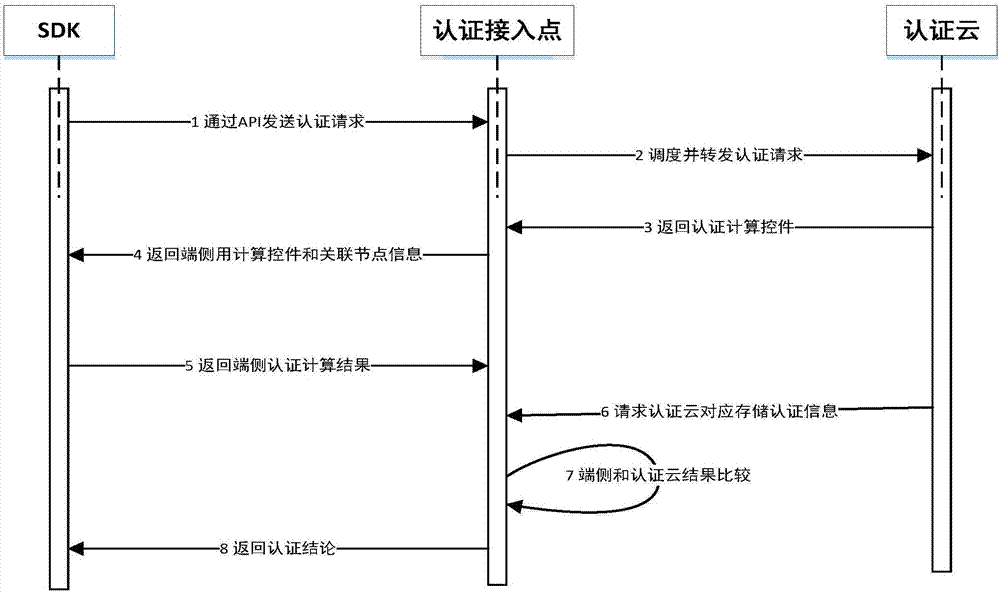
[0051] A distributed identity authentication demonstration system implemented by a bank based on the technical solution of the present invention. By combining the customer's existing physical and virtual environments, a set of identity authentication systems for mobile terminals (android), PC terminals (windows) and business systems (Linux) is built. The authentication cloud distributed unit consists of 10 servers with different configurations Composition, distributed units can be added at any time. The number of access users is about 5000, and the performance of this set of demonstration system has reached that the identity authentication function is still running normally when 50% of the distributed units exit; when the number of concurrent users reaches 2000, the identity authentication of various terminal devices is less than 1s.
[0052] Through client products combined with server-side integration support, on the one hand, it can be used in the new business system to sup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com