A method for creating intrusion detection rules based on industrial control network variant attack
An industrial control network and intrusion detection technology, which is applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems that cannot be changed in time, unfavorable rule base establishment and upgrade, and low false alarm rate, so as to save time and energy effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
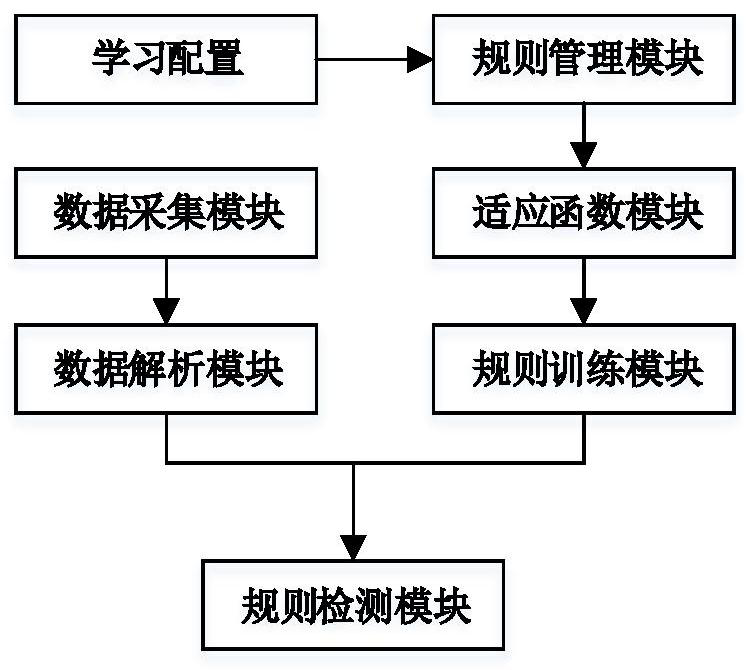
[0039] Such as figure 1 As shown, the present invention provides a method for creating an intrusion detection rule based on an industrial control network variant attack, comprising the following steps:
[0040] Data acquisition step: use WinPcap to capture network data packets from the industrial control network through the data acquisition module, and save the data packets in the cache queue respectively according to the 502 port of the ModbusTCP protocol by judging the protocol of the network data;
[0041] Data analysis step: obtain the data packet from the cache queue through the data analysis module, and analyze the data field of the application layer of the ModubsTCP protocol through the deep data packet analysis technology;
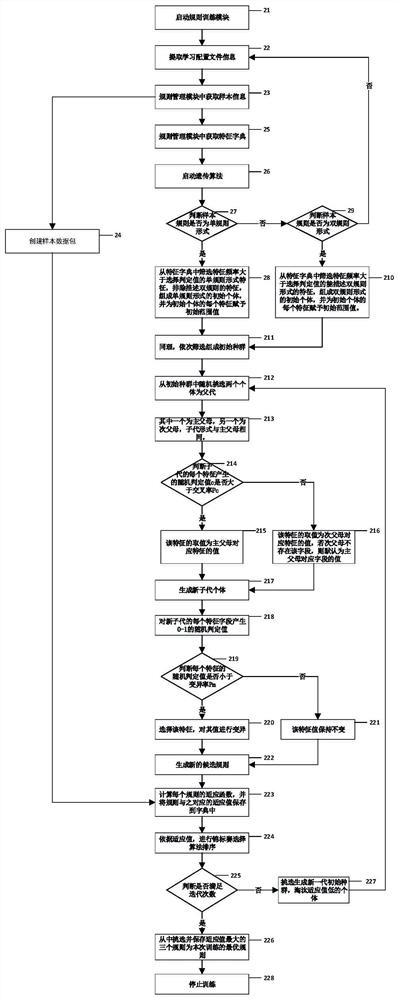
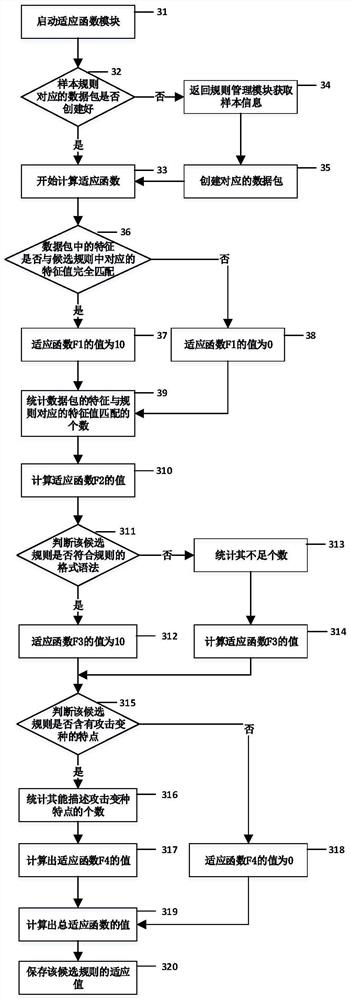
[0042] Rule training step: use the rule training module to determine whether the sample type is single ru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com