Certification pattern determination method and payment method using same
A payment method and pattern technology, applied in the payment system, payment system structure, user identity/authority verification, etc., can solve security weaknesses, interception and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
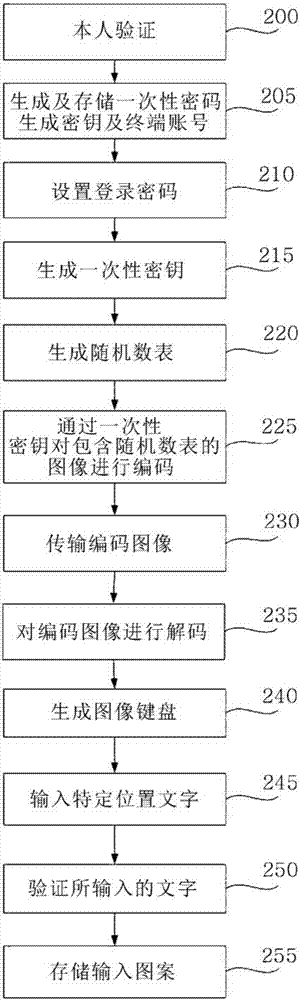
[0020] Hereinafter, preferred embodiments of the present invention will be described with reference to the drawings. In the following description, the order of description of the flow charts should be construed as non-limiting, except for the case where a preceding step should be a theoretically preceding, necessarily preceding step of a subsequent step. That is, it should not be interpreted as excluding the possibility that subsequent steps are performed before preceding steps.
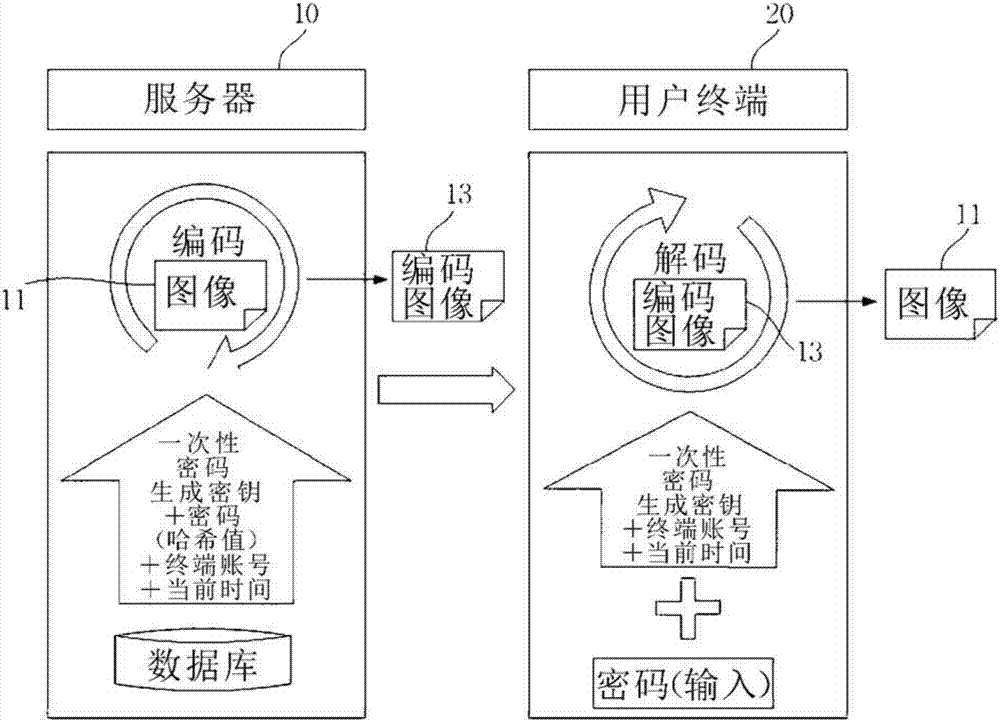
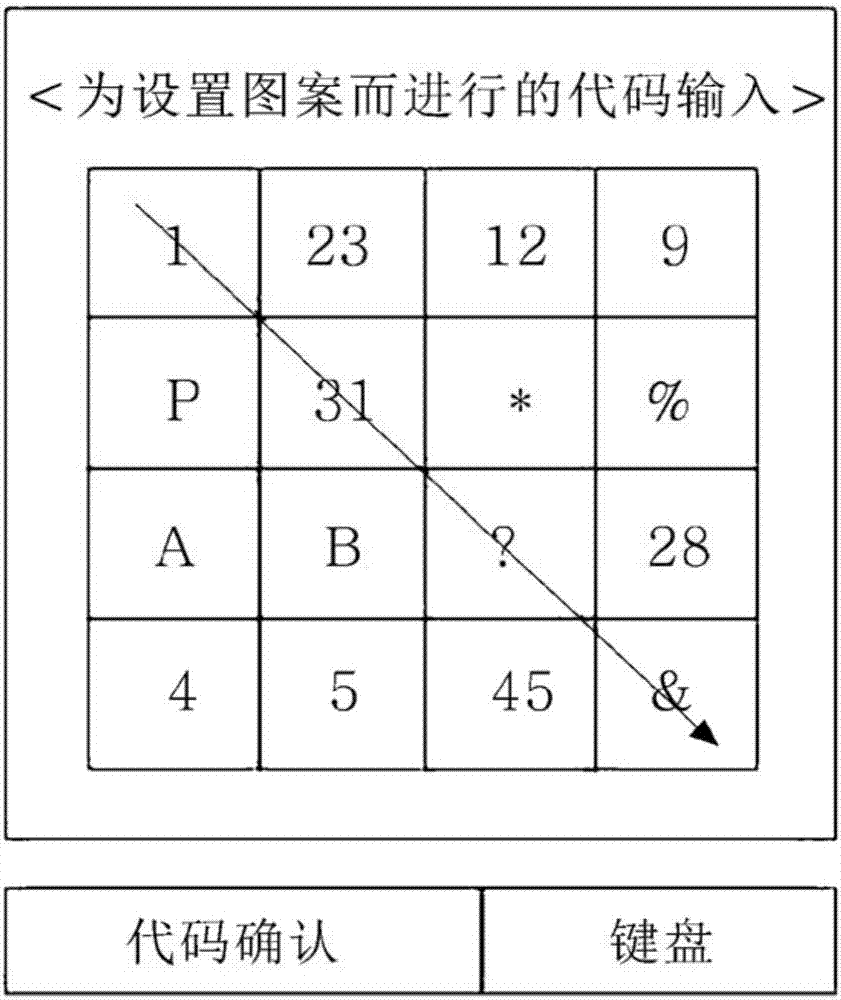
[0021] figure 1 Shown are the server 10 and the user terminal 20 and their internal operations under the environment in which the present invention is executed. figure 1 The content contained in the image 11 may vary according to the action. refer to figure 2 , the verification pattern storage method of the present invention will be described.
[0022] Before executing the present invention, the user sets the application software on the user terminal 20 that can perform the verification pattern ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com