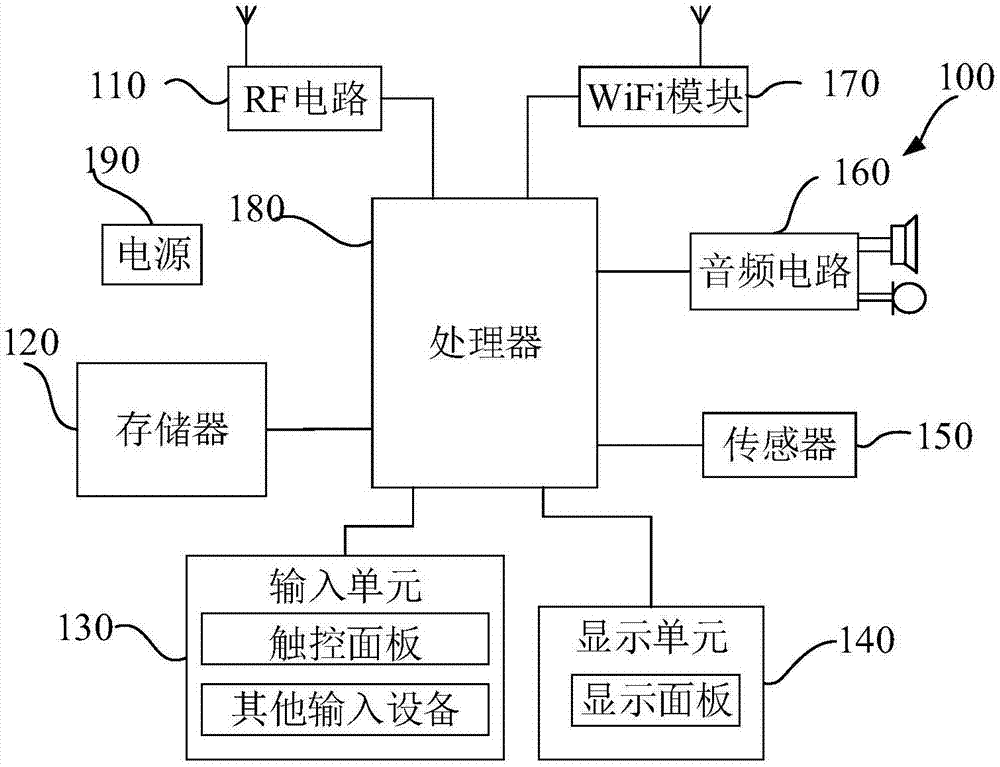
Alarm method, alarm device, mobile terminal, and computer readable storage medium
A mobile terminal and computer program technology, applied in the fields of computer-readable storage media, alarm methods, and alarm devices, can solve problems such as help calls, rescue obstacles, communication difficulties with the outside world, loss of life, and property, and achieve rapid alarm effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
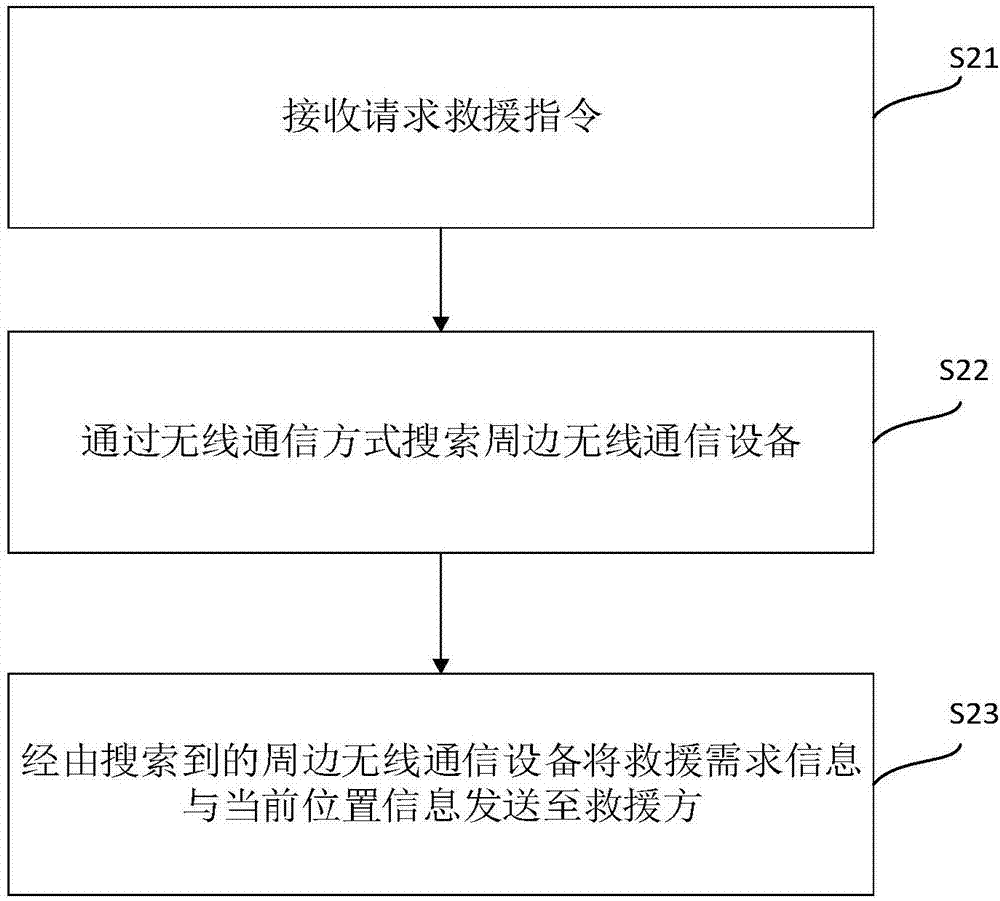
[0049] figure 2 It is a flow chart of embodiment 1 for alarming under weak signal or no signal situation. This embodiment gives the situation that the user is in a remote area and the signal of the user's mobile terminal is weak or has no signal. At this time, even if the user is not injured, the user cannot directly contact the outside world through the mobile terminal. The method comprises the steps of:
[0050] In step S21, a rescue request instruction is received.
[0051] Rescue instructions input by the user by inputting specific characters or combinations of characters, pressing physical keys, and inputting special audio by voice can be received. That is, the rescue request instruction may be a voice instruction, a character instruction and / or a physical key instruction, and the like.
[0052] For example, the instruction to request rescue may be a specific character or a combination of characters. In order to avoid misoperation, a combination of characters is preferr...
Embodiment 2
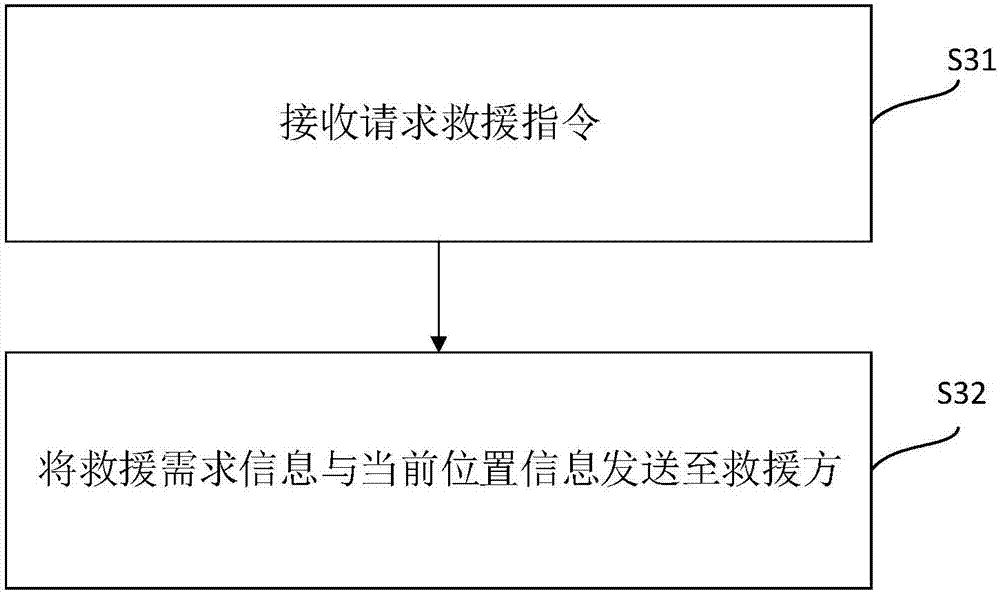
[0070] image 3 It is a flow chart of embodiment 2 in which an alarm is issued in a signal state. The alarm method of this embodiment is applicable to the situation where the mobile terminal is in a signal state and the user in an emergency state cannot communicate by language. The method comprises the steps of:
[0071] In step S31, a rescue request instruction is received.
[0072] After receiving the rescue request instruction, in step S32, the rescue request information and the current location information are sent to the rescue party.
[0073] Embodiment 2 differs from Embodiment 1 in that: the rescue demand information and current location information are directly sent to the rescuer according to the rescue request instruction, without going through surrounding wireless communication devices. The current location information may include not only the GPS location information of the mobile terminal, but also the location information of the base station where the mobile ...
Embodiment 3
[0079] Figure 4 It is a flow chart of embodiment 3 for alarming when there is a signal. For example, when a car breaks down halfway and emergency rescue is needed, people may know their approximate location, but because there are no prominent landmarks, it is impossible to clearly describe the specific location. Moreover, in some unfamiliar environments, even the approximate location may not be provided. , which brings difficulty to the positioning of rescuers. This embodiment is applicable to the above-mentioned scenarios. The method comprises the steps of:
[0080] In step S41, receiving a current location sending instruction in a talking state.
[0081] In the case of a mobile terminal with a signal, the user can call for rescue, but during the communication process, the description of the current location may not be cleared. Therefore, the user can send the current location while in the call state. The current location sending instruction input by the user by inputti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com