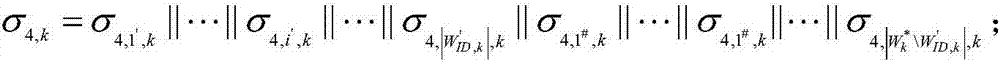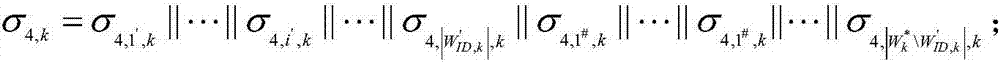Attribute-based network ring signing method for distributed authorization
A distributed, ring signature technology, applied in user identity/authority verification and key distribution, can solve problems such as increasing the communication cost between the attribute authority AA and the user, attribute key escrow, and anonymity degradation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0072] A specific embodiment of the present invention is a distributed authorization attribute-based network ring signature method, the steps of which are:
[0073] A. Parameter generation
[0074] A1. Establishment of attribute set
[0075] The system establishes attribute collection space W, W={W 1 ,...,W k ,...,W K},in is the kth attribute subset of the attribute set space W, and K is the total number of attribute subsets in the attribute set space W; w i,k is the kth attribute subset W k The i-th attribute in |W k | is the kth attribute subset W k The total number of attributes in;
[0076] A2. Generation of system public key and private key
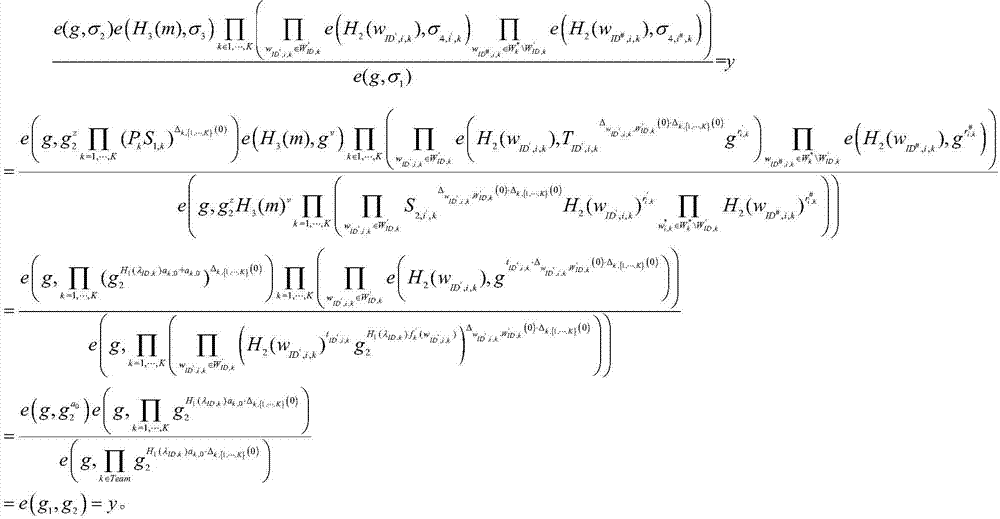
[0077] System setting P≥K distributed attribute authority AA p , where p is the attribute authority AA p serial number, p={1,2,...,P}; construct q factorial method cyclic group G and q factorial method cyclic group Y, q is greater than 2 512 and there is a bilinear mapping relationship y=e(g a , g b ); among them, e(g ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com