A Source IP Protection Method Based on Scanning Probe Behavior
A technology for scanning probes and behaviors, applied in the field of communications, to solve problems such as the inability to record the source IP address in time and the inability of network administrators to detect it all the time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] It should be noted that, in the case of no conflict, the embodiments of the present invention and the features in the embodiments can be combined with each other.
[0032] The present invention will be described in detail below with reference to the accompanying drawings and examples.
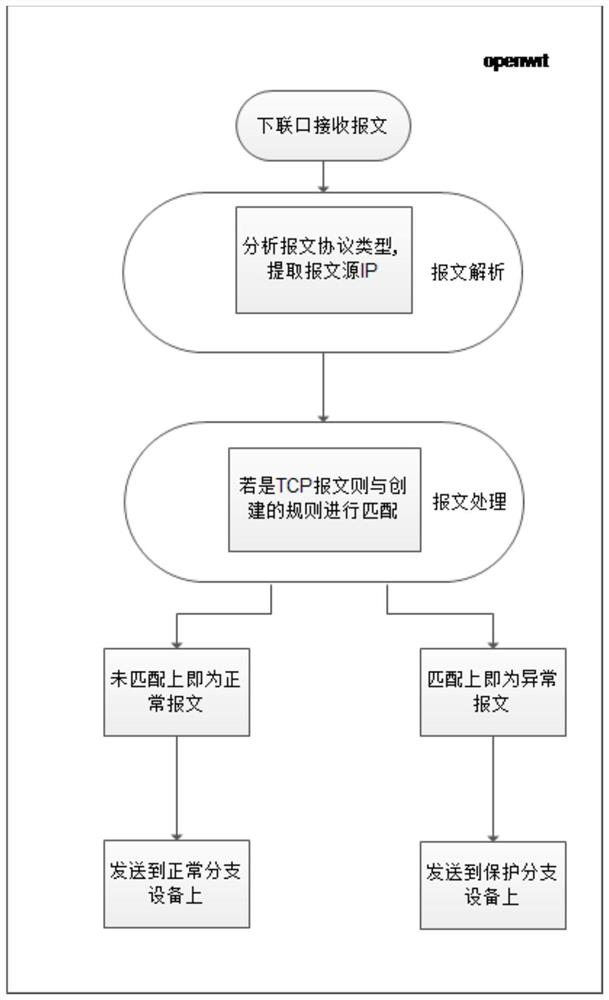
[0033] A source IP protection method based on scanning probe behavior, comprising the following content:
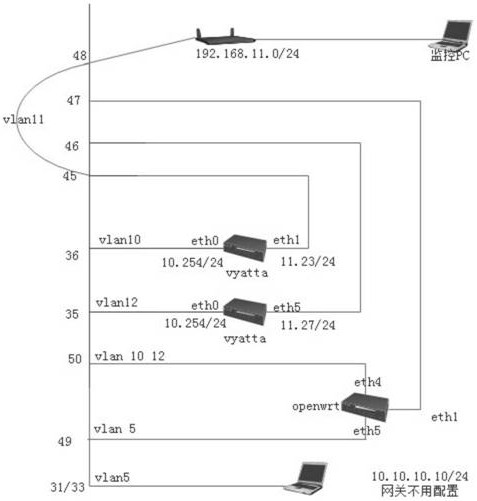
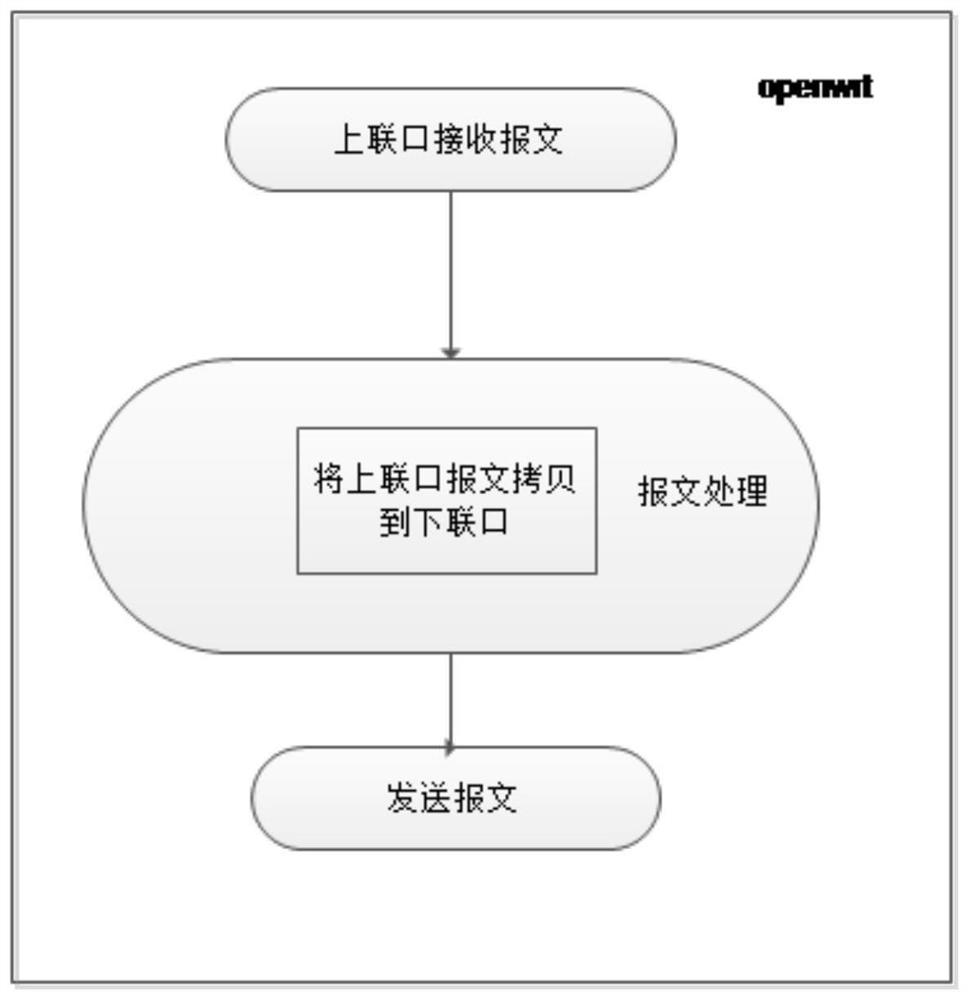
[0034] After the uplink port receives the message, it does not need to be modified, and the message is copied to the downlink port intact. The processing flow of the uplink port receiving the message is as follows: figure 1 shown;
[0035] Because the uplink port does not need IP protection to receive packets. The so-called IP protection protects the online behavior of intranet users. Therefore, the task of the uplink port is to copy the message to the downlink port intact and send it to the intranet user, which is equivalent to sending the message to the peer end in bridge mode, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com