Key code programming method, server, terminal, key code programming system and storage medium
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
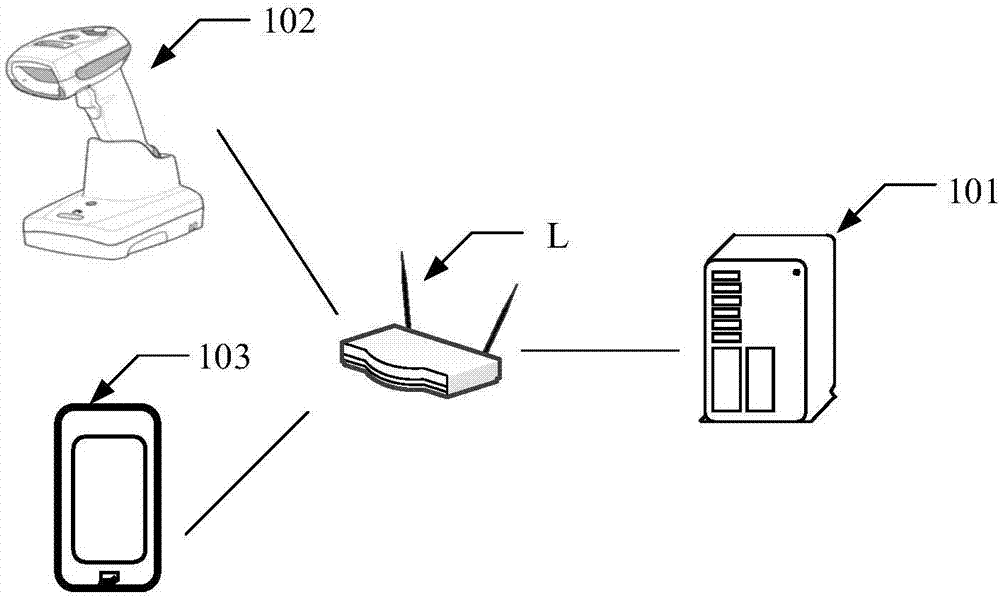
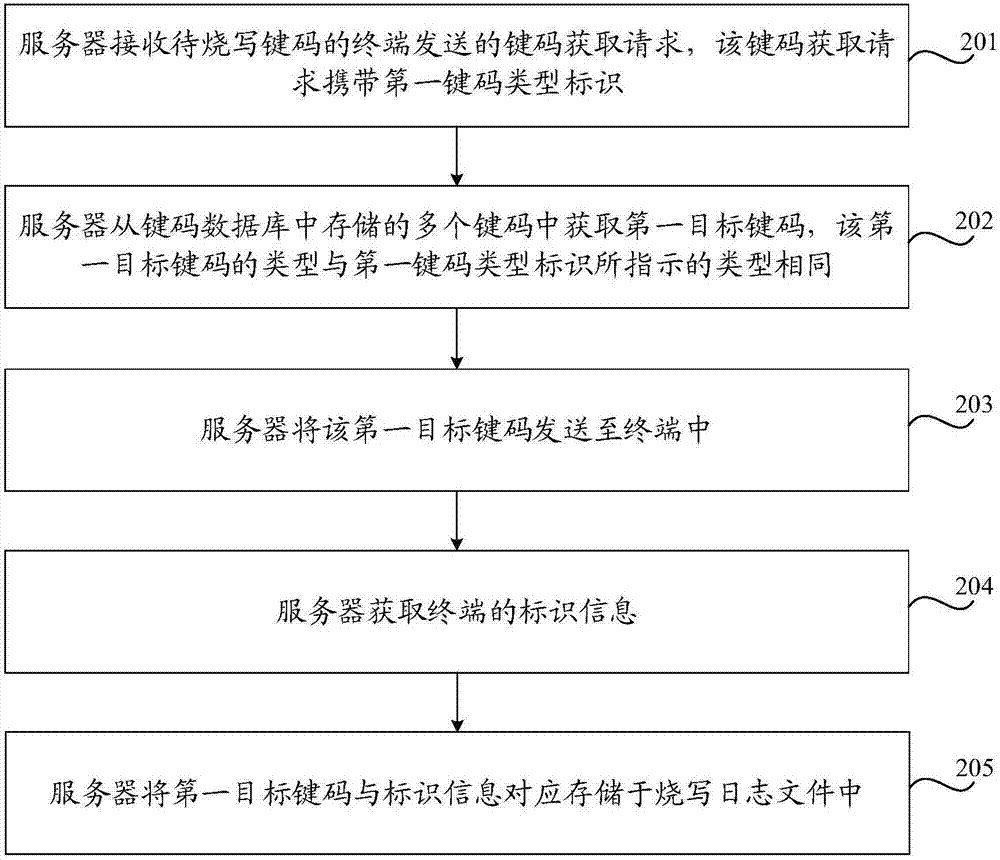
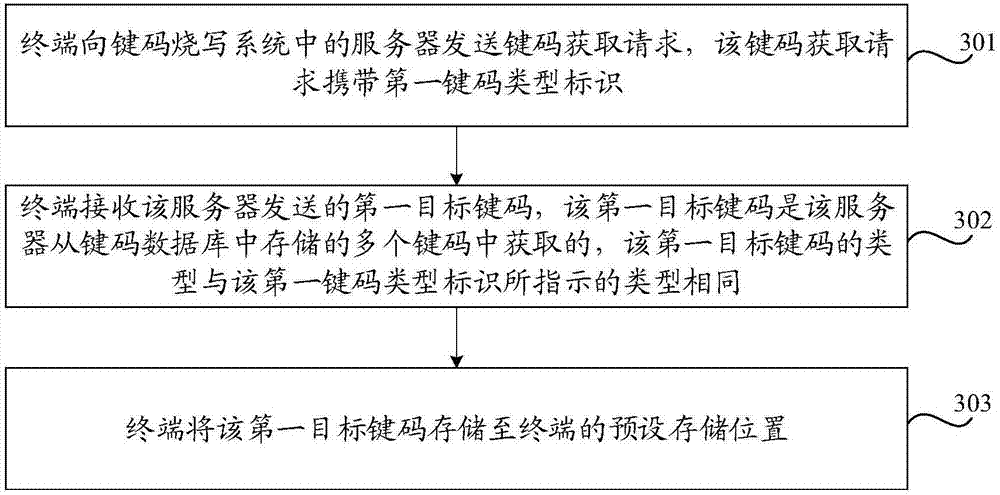
[0056]Usually, before the terminal leaves the factory, it is necessary to burn the key code for the terminal. The key code can also be called the key code, which is a kind of data used to identify the terminal or to ensure that the terminal can realize certain functions. For example, key The code can be a physical address (used to uniquely identify the terminal), or an HDCP (High-bandwidth Digital Content Protection) code to ensure that the terminal can decode high-definition video, or a code for the terminal to access certain network services. required keys, etc.
[0057] In practical applications, it is usually necessary to program multiple key codes of different types for a terminal. For example, before a certain terminal leaves the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com