Relation-based access control method
An access control and relationship technology, applied in the field of network information security, can solve problems such as hidden security risks, poor scalability, and difficulty in applying distributed systems, and achieve the effect of improving the degree of automation and ensuring information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The above-mentioned features and advantages of the present invention can be better understood after reading the detailed description of the embodiments of the present disclosure in conjunction with the following drawings. In the drawings, components are not necessarily drawn to scale, and components with similar related properties or characteristics may have the same or similar reference numerals.
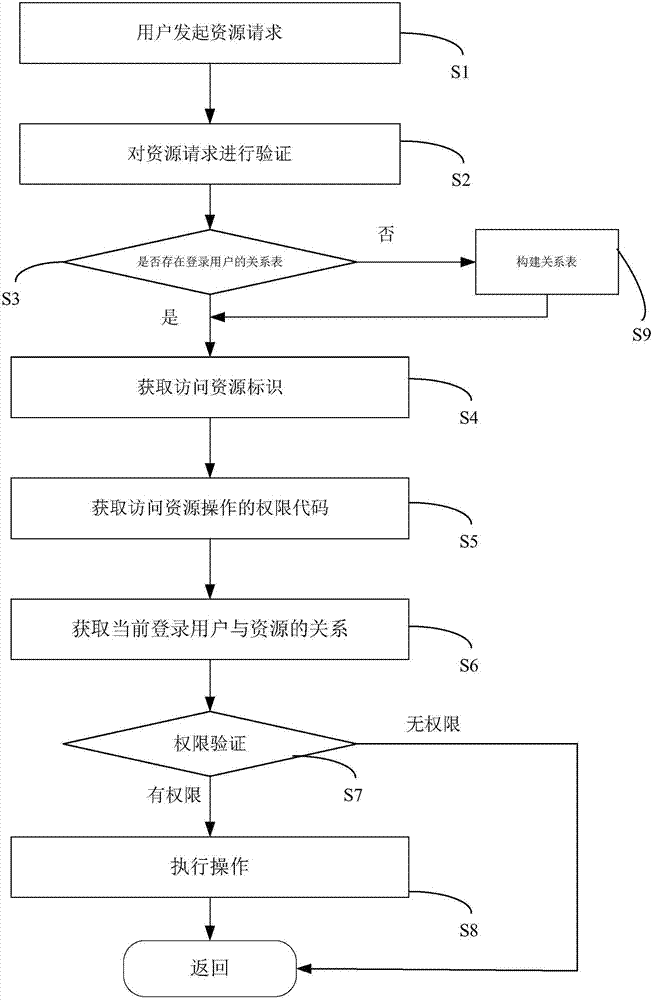
[0054] figure 1It shows the flow of a preferred embodiment of the relation-based access control method of the present invention. See figure 1 , the following is a detailed description of each step of the method of this embodiment.
[0055] Step S1: The user initiates a resource request.
[0056] Step S2: Verify the resource request, and enter the next step after the verification is passed.
[0057] That is, user U accesses resource R to verify whether user U is a legal user of the system.
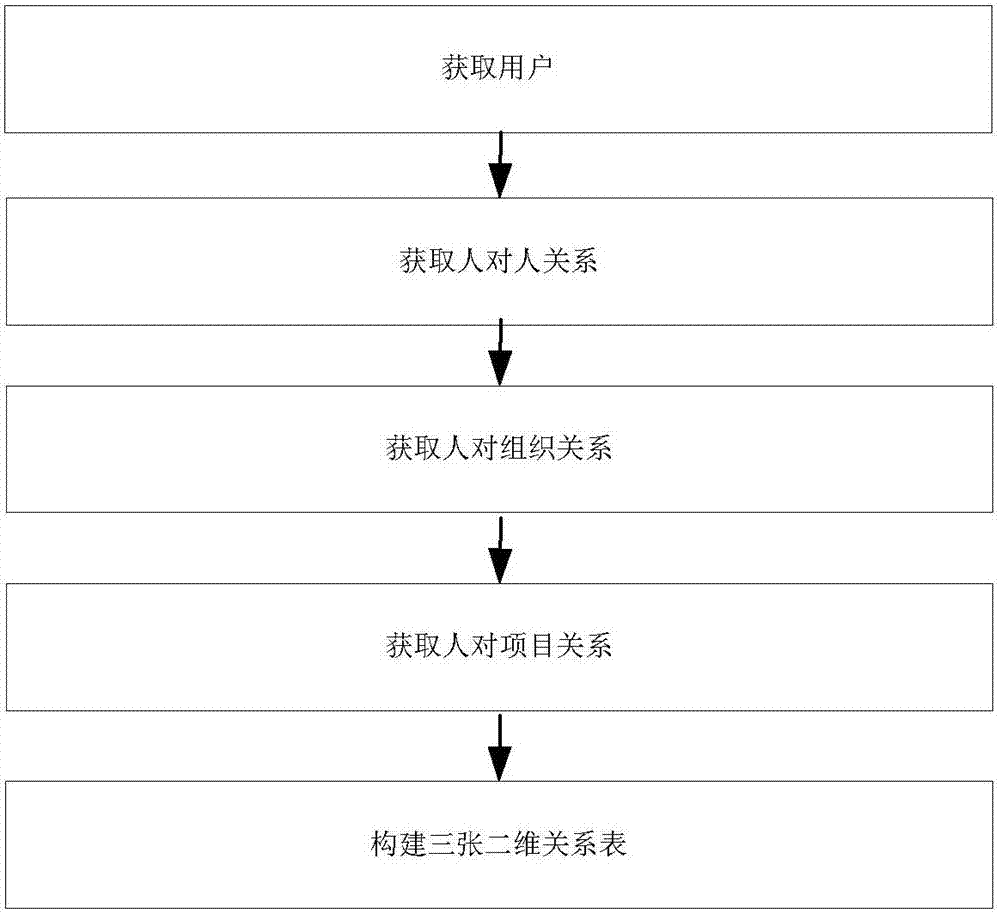
[0058] Step S3: Verify whether there is a relational table of the user in the ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com