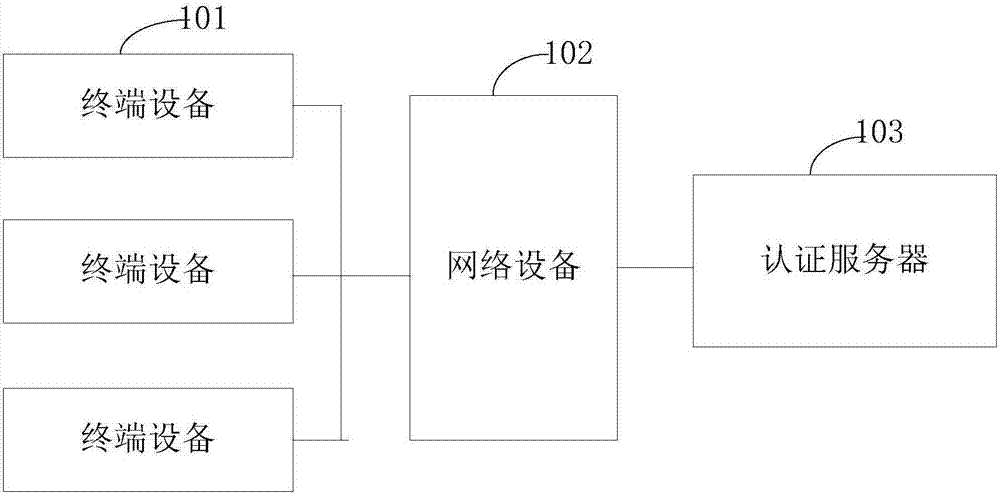
Network access authentication method and device
A network access and authentication method technology, applied in the field of network access authentication methods and devices, can solve problems such as affecting the online efficiency of terminal equipment and consuming a lot of human resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
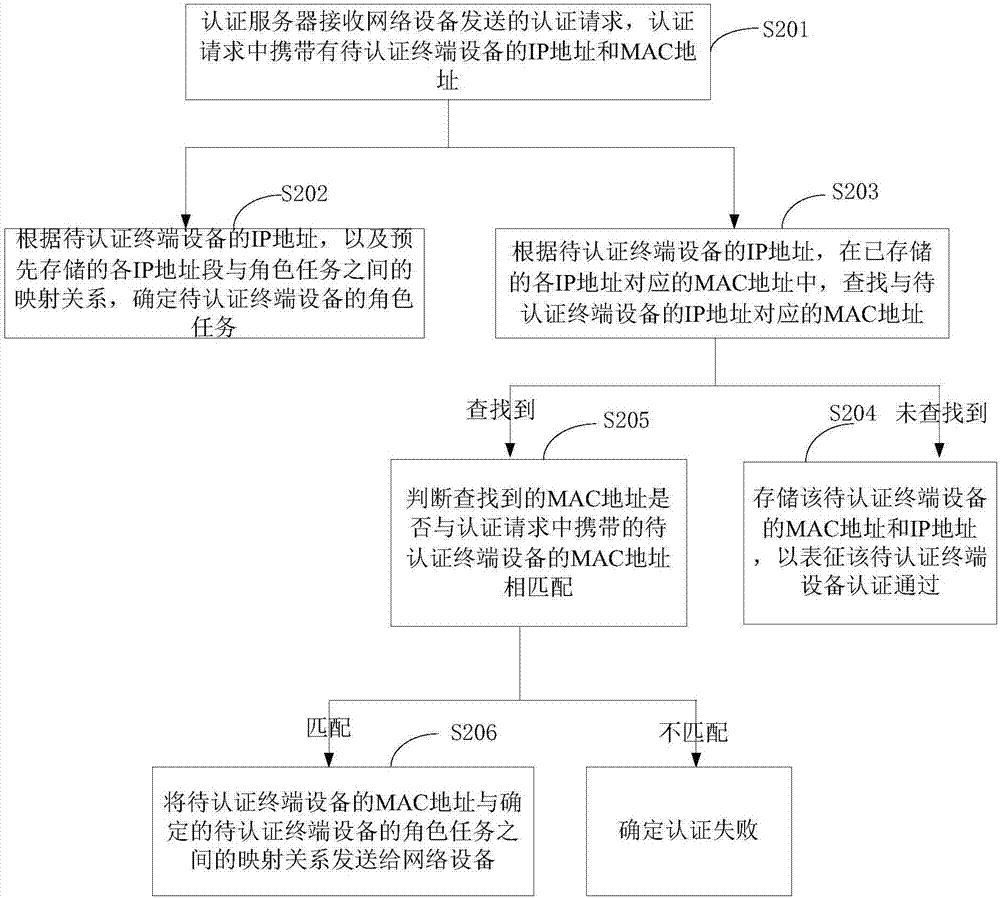
[0030] see figure 2 As shown, the network access authentication method provided by Embodiment 1 of the present application includes the following steps S201-S203:
[0031] S201: The authentication server receives an authentication request sent by a network device, and the authentication request carries an IP address and a MAC address of a terminal device to be authenticated.
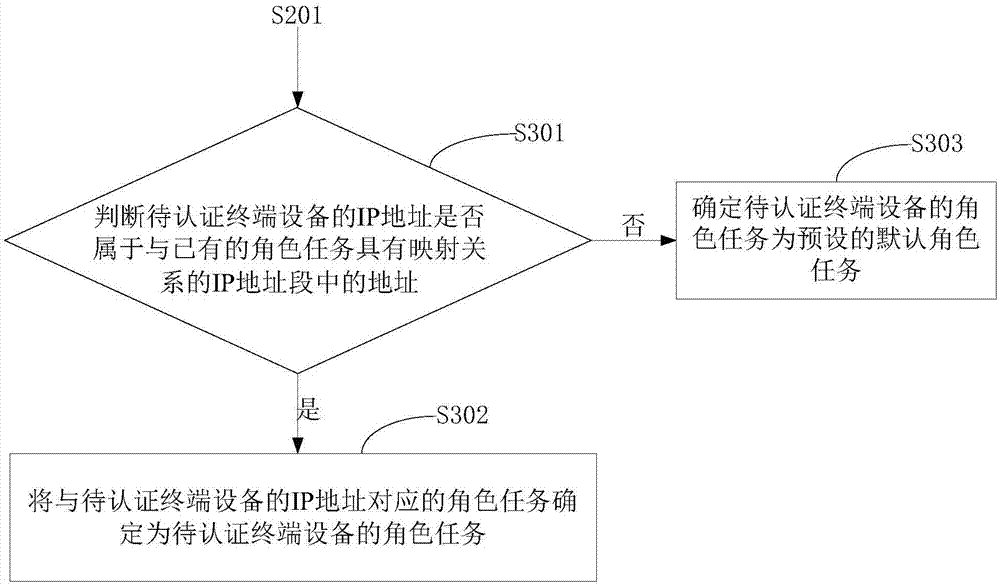
[0032] S202: Determine the role task of the terminal device to be authenticated according to the IP address of the terminal device to be authenticated and the pre-stored mapping relationship between each IP address segment and the role task.
[0033] Wherein, the IP address of the terminal device to be authenticated is configured according to the pre-stored mapping relationship between each IP address segment and the role task, and the role task to be performed by the terminal device to be authenticated.
[0034] The embodiment of the present application is mainly applied to a scenario where an IP addres...
Embodiment 2
[0065] see Figure 4 As shown, the network access authentication device provided in Embodiment 2 of the present application includes:
[0066] The receiving module 401 is configured to receive an authentication request sent by a network device, and the authentication request carries an Internet protocol IP address and a media access control MAC address of the terminal device to be authenticated.
[0067] Executing module 402, configured to determine the role task of the terminal device to be authenticated according to the IP address of the terminal device to be authenticated and the pre-stored mapping relationship between each IP address segment and role task; For the IP address of the device, search for the MAC address corresponding to the IP address of the terminal device to be authenticated in the stored MAC addresses corresponding to each IP address; if not found, store the MAC address and IP address of the terminal device to be authenticated , to indicate that the termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com