Security encryption method and system
A technology of secure encryption and encryption algorithm, which is applied in the field of secure encryption methods and systems, and can solve problems such as leakage of user passwords, risks of encryption methods, and low encryption security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
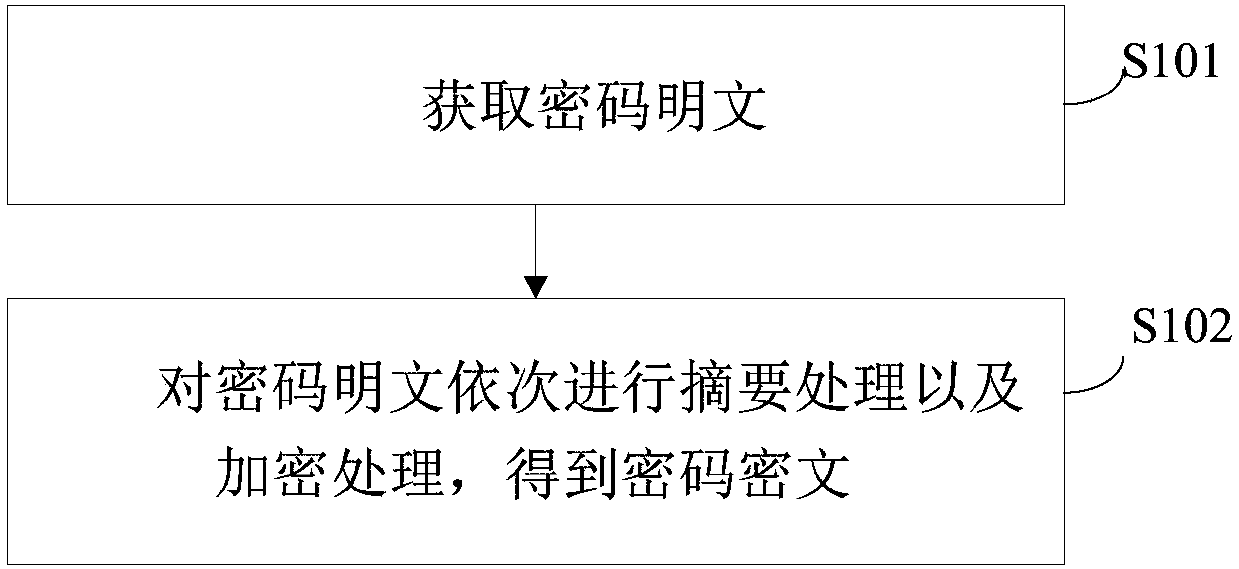
[0043] figure 1 It is a flow chart of the secure encryption method provided by Embodiment 1 of the present invention.
[0044] refer to figure 1 , secure encryption methods, including:
[0045] Step S101, obtaining password plaintext;
[0046] Step S102, perform digest processing and encryption processing on the password plaintext according to preset rules to obtain the password ciphertext.
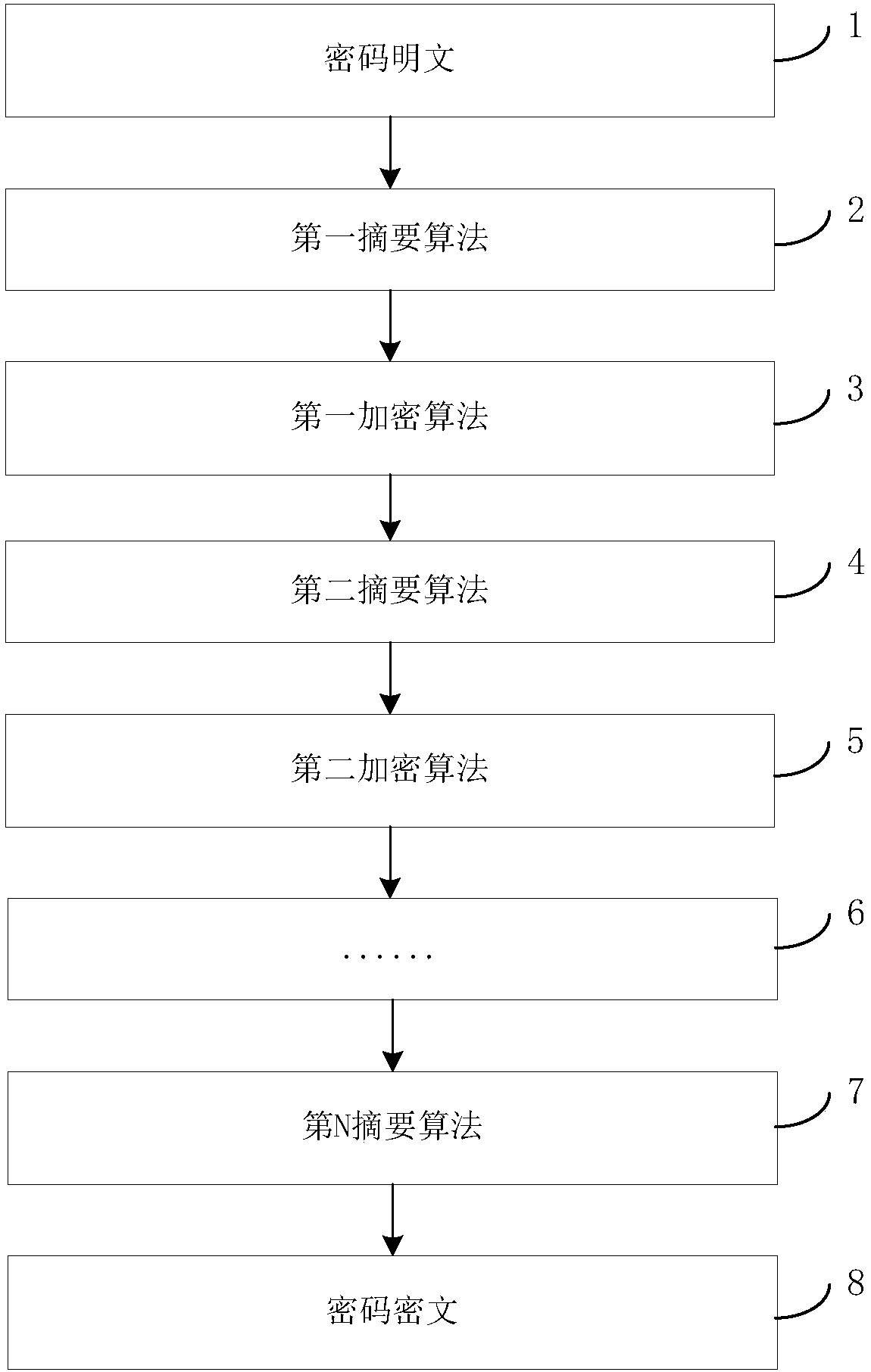
[0047] The preset rule is a pre-customized encryption process. Generally, when the background encrypts the password, the digest algorithm is directly encrypted. The hacker can still try to restore the ciphertext by pre-establishing the corresponding table of all passwords and their digests; the risk of this encryption method is still bigger. The embodiment of the present invention executes multiple digest processing and multiple encryption processing according to preset rules, which can resist the attack by pre-generating the corresponding table. Attack, the attack cost is very high....
Embodiment 2
[0072] Figure 4 It is a schematic diagram of the security encryption system provided by Embodiment 2 of the present invention.
[0073] refer to Figure 4 , a secure encryption system, including:
[0074] Obtaining module 10, for obtaining password plaintext;
[0075] The digest encryption module 20 is configured to perform digest processing and encryption processing on the password plaintext according to preset rules to obtain password ciphertext.
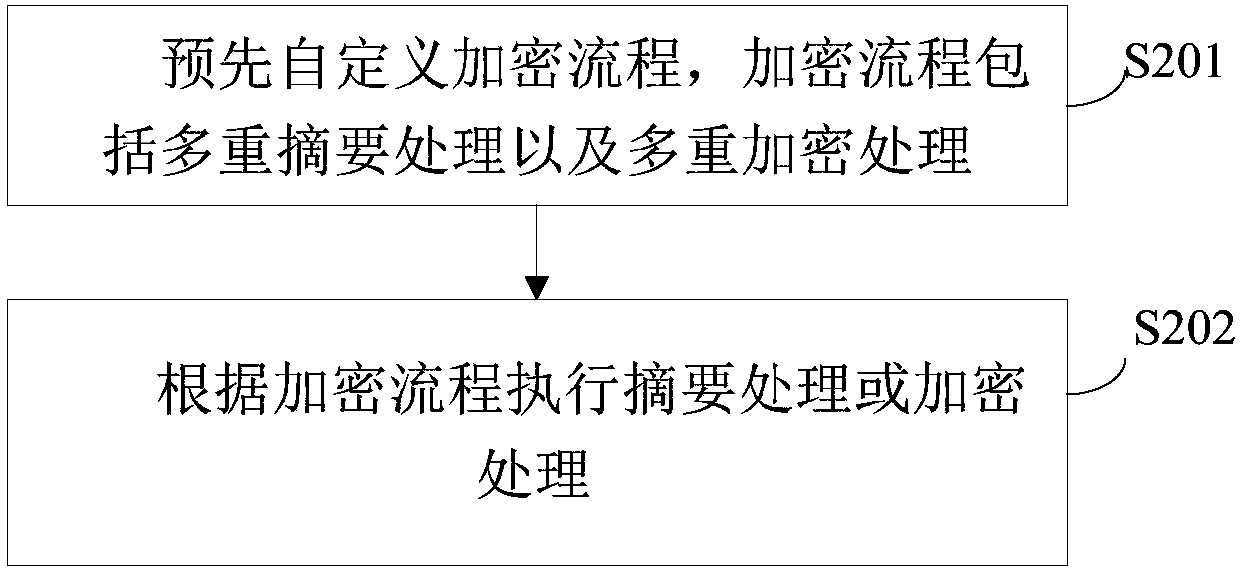
[0076] Further, as Figure 5 As shown, the digest encryption module 20 includes:
[0077] The custom unit 21 is used to pre-customize the encryption process, and the encryption process includes multiple digest processing and multiple encryption processing;
[0078] The digest encryption unit 22 is configured to perform digest processing or encryption processing according to the encryption process.
[0079] Further, the digest encryption unit 22 includes:
[0080] The first digest encryption unit (not shown) executes the fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com