Method for constructing safety domain model of flexible power distribution network
A technology of distribution network and security domain, applied in the direction of electrical components, circuit devices, AC network circuits, etc., can solve the problems of randomness, intermittency, and volatility of renewable energy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
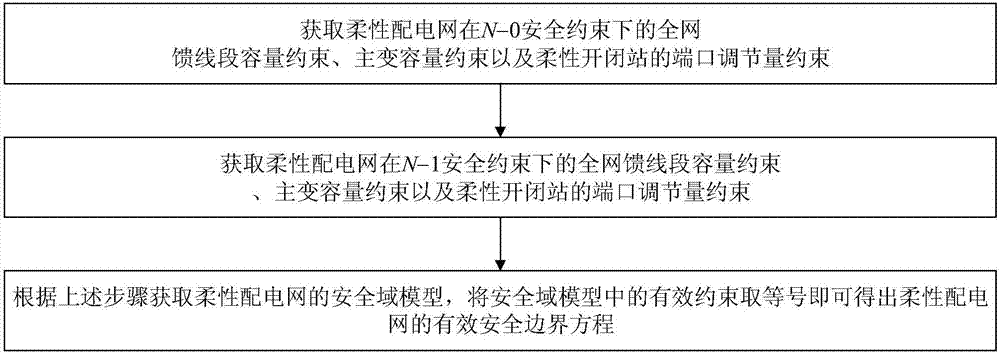
[0045] An embodiment of the present invention provides a method for constructing a security domain model of a flexible distribution network, see figure 1 , the method includes the following steps:
[0046] 101: Obtain the capacity constraints of the feeder section of the flexible distribution network under the N-0 security constraint, the capacity constraints of the main transformer, and the port regulation constraints of the flexible switching station;
[0047] 102: Obtain the capacity constraints of the feeder section of the flexible distribution network under the N-1 security constraint, the capacity constraints of the main transformer, and the port regulation constraints of the flexible switching station;
[0048] 103: Obtain the security domain model according to step 101 and step 102, and obtain the effective security boundary equation of the FDN security domain by equalizing the effective constraints in the security domain model.
[0049] To sum up, the embodiment of t...
Embodiment 2
[0051] The scheme in embodiment 1 is further introduced below in conjunction with specific calculation formulas and examples, see the following description for details:
[0052] 201: preparatory work;
[0053] In FDN, this method selects the node load in the feeder as the state variable instead of the feeder outlet load selected by TDN. The reasons are as follows: TDN closed-loop design is open-loop operation, and the power supply for a single load comes from only one power source. The power at the outlet of the feeder is equal to the load plus the network loss, which is approximately equal to the load. In order to be consistent with the actual situation of distribution network data collection and the habits of dispatchers, when studying TSC, distribution system security region (DSSR) and N-1 security, the feeder outlet (multi-connection part) is generally selected. is the power of the feeder section) as the state variable. In FDN flexible closed-loop operation, the load of ...
Embodiment 3
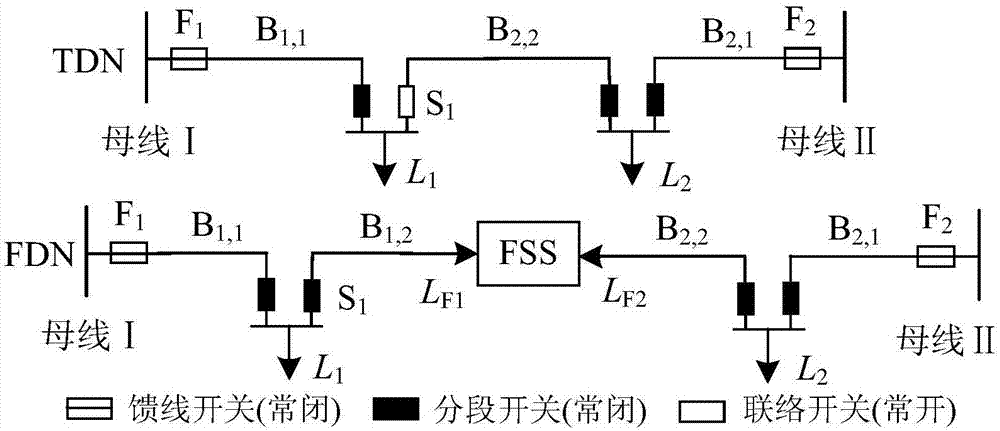
[0114] The following combined with specific examples, Figure 2-Figure 8 The scheme in embodiment 1 and 2 is carried out feasibility verification, see the following description for details:
[0115] 1. Basic situation of the example
[0116] figure 2 , 5 Middle: L i Indicates the equivalent load; L Fi is the power injected into FSS, L Fi is positive to indicate power from F i The side flows into the FSS, and vice versa. figure 2 , 5 The basic parameters of the calculation example are shown in Table 1.
[0117] Table 1 Basic parameters of single / multi-connection case
[0118]
[0119] Two, the implementation steps of the present invention
[0120] (1) Single contact calculation example
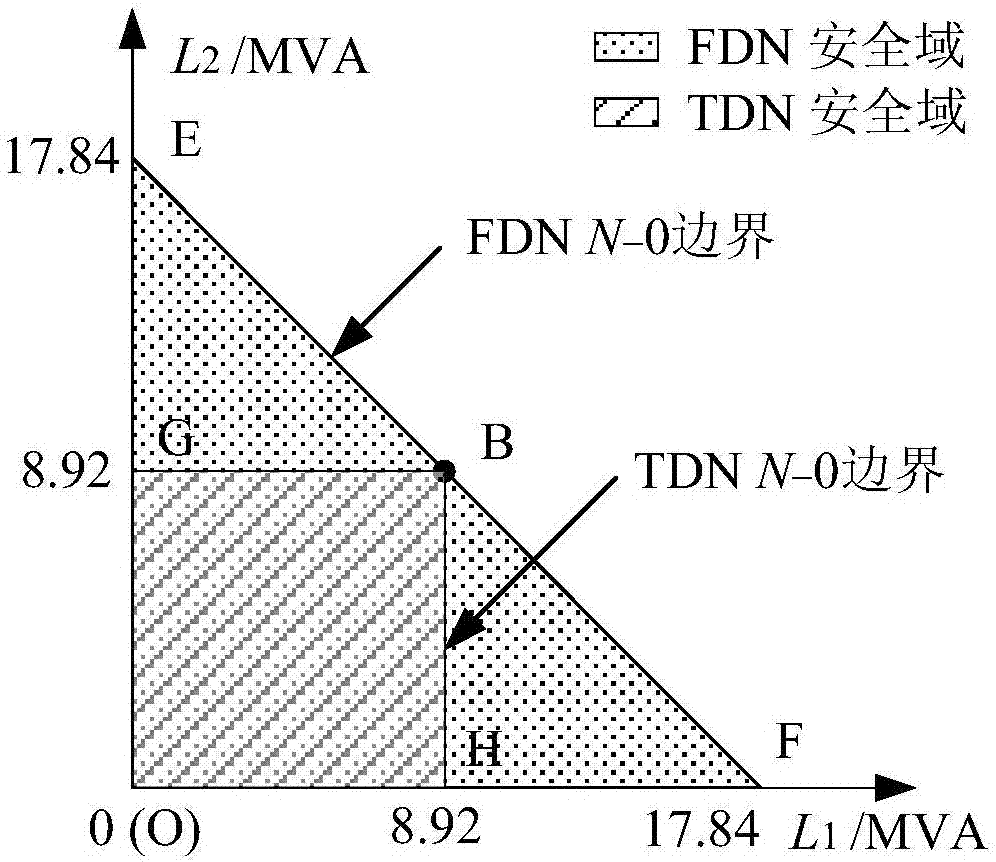
[0121] 1) Effective security constraints
[0122] The effective security constraints are obtained after removing invalid constraints from the security constraints of the single-connection case N-0 and N-1, as shown in Table 2.
[0123] Table 2 Effective security constraints of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com