Method for IMSI privacy protection of mobile communication system
A technology of mobile communication system and privacy protection, which is applied in the field of privacy protection of mobile communication system IMSI, which can solve problems such as the difficulty of adding real identities, and achieve the effect of meeting the national military-civilian integration strategy and having a wide range of applications
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
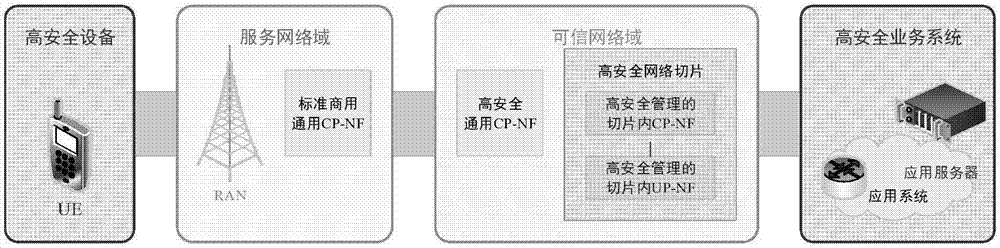
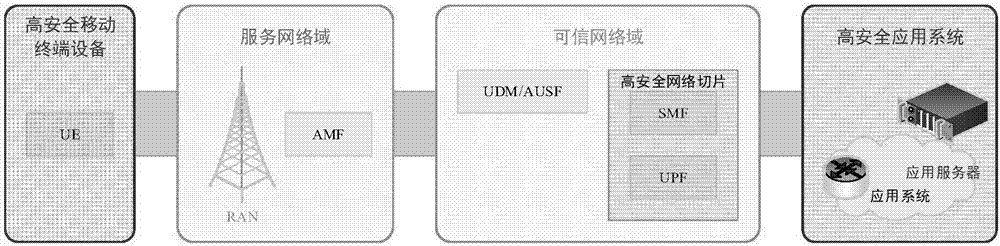
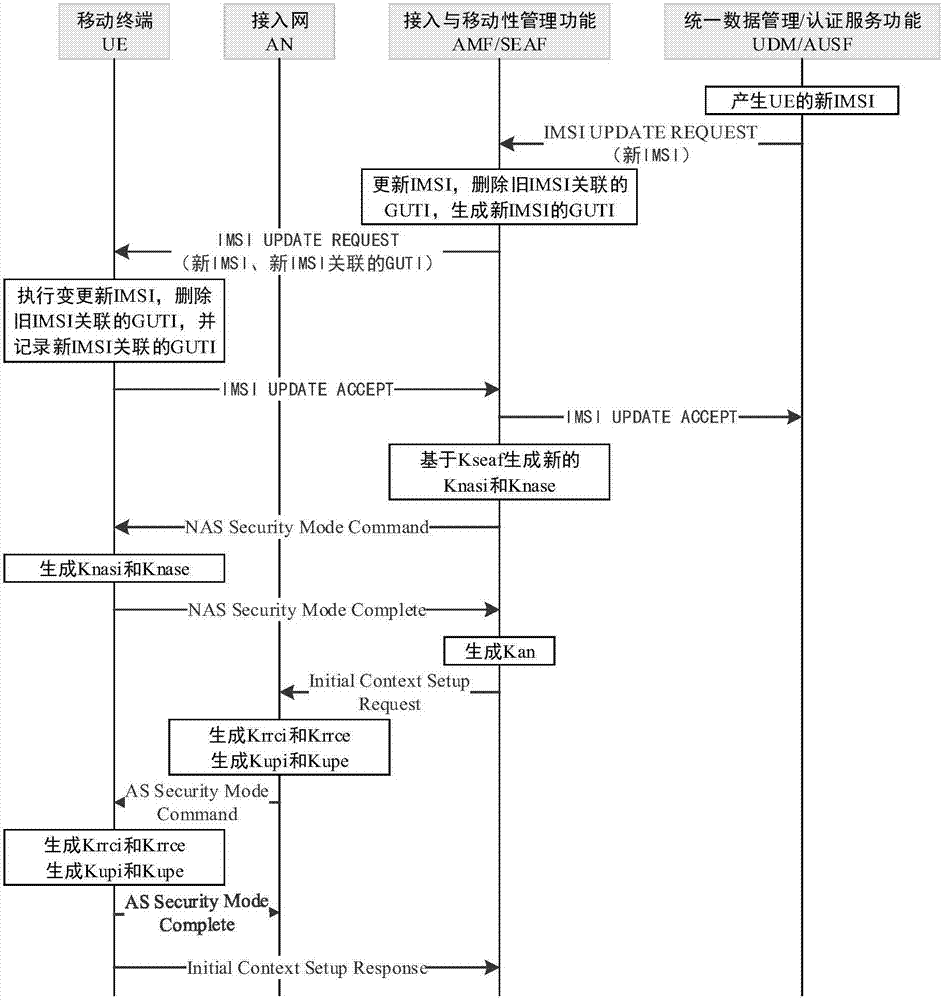
[0021] The method of the present invention follows the standard framework of international standards, and the functional entities include mobile terminal UE, radio access network RAN, access and mobility management function AMF, trusted unified data management / authentication service function UDM / AUSF, trusted network slice ( Trusted Session Management Function SMF, Trusted User Plane Function UPF) and application systems, such as figure 2 Shown:
[0022] The mobile terminal UE is used to perform an IMSI change behavior and initiate a network attachment request, and at the same time complete new security context negotiation based on the new IMSI.
[0023] The serving AMF / MME is used to actively (CP mode) or passively (UP mode) replace the IMSI information and its related GUTI information, and complete the security context negotiation based on the new IMSI.
[0024] The trusted UDM / AUSF / HSS is used to generate new IMSI information for the UE according to a certain strategy.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com