Method for Windows system login by smart card and private credential providing device
A smart card, a proprietary technology, applied in the field of information security, can solve problems such as the user interface is not friendly enough, the login interface is not friendly enough, and the user cannot be prompted
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
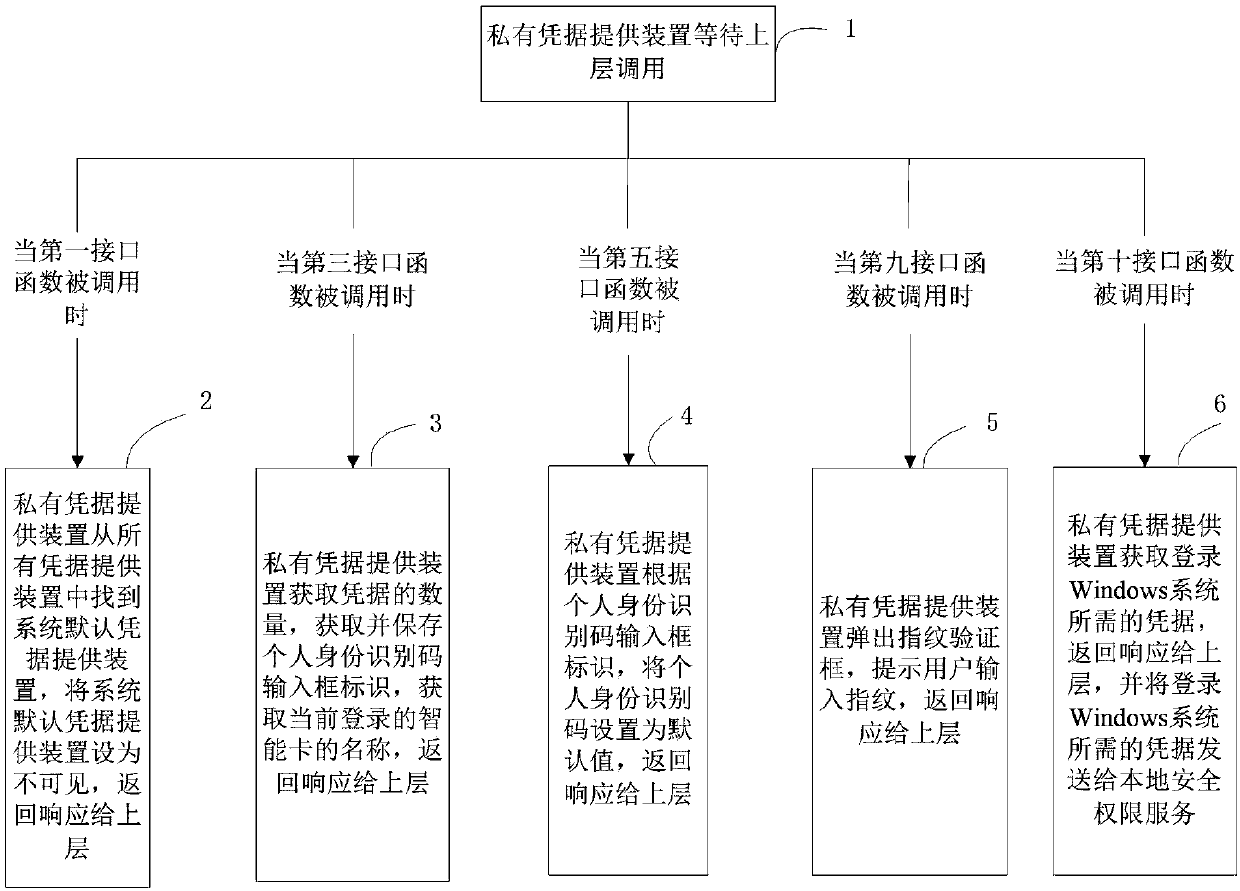
[0106] Example 1 of the present invention provides a method for logging into a Windows system with a smart card. Such as figure 1 As shown, the specific process is as follows:
[0107] Step 1, the private credential providing device waits for the upper layer to call,
[0108] When the first interface function of the private credential providing device is called, step 2 is performed;
[0109] When the third interface function of the private credential providing device is called, perform step 3;
[0110] When the fifth interface function of the private credential providing device is called, perform step 4;
[0111] When the ninth interface function of the private credential providing device is called, perform step 5;
[0112] When the tenth interface function of the private credential providing device is called, step 6 is performed.
[0113] Specifically, the upper layer may be a program implementing a login function, such as LoginUI.exe or Mstsc.exe.
[0114] Step 2, the ...
Embodiment 2
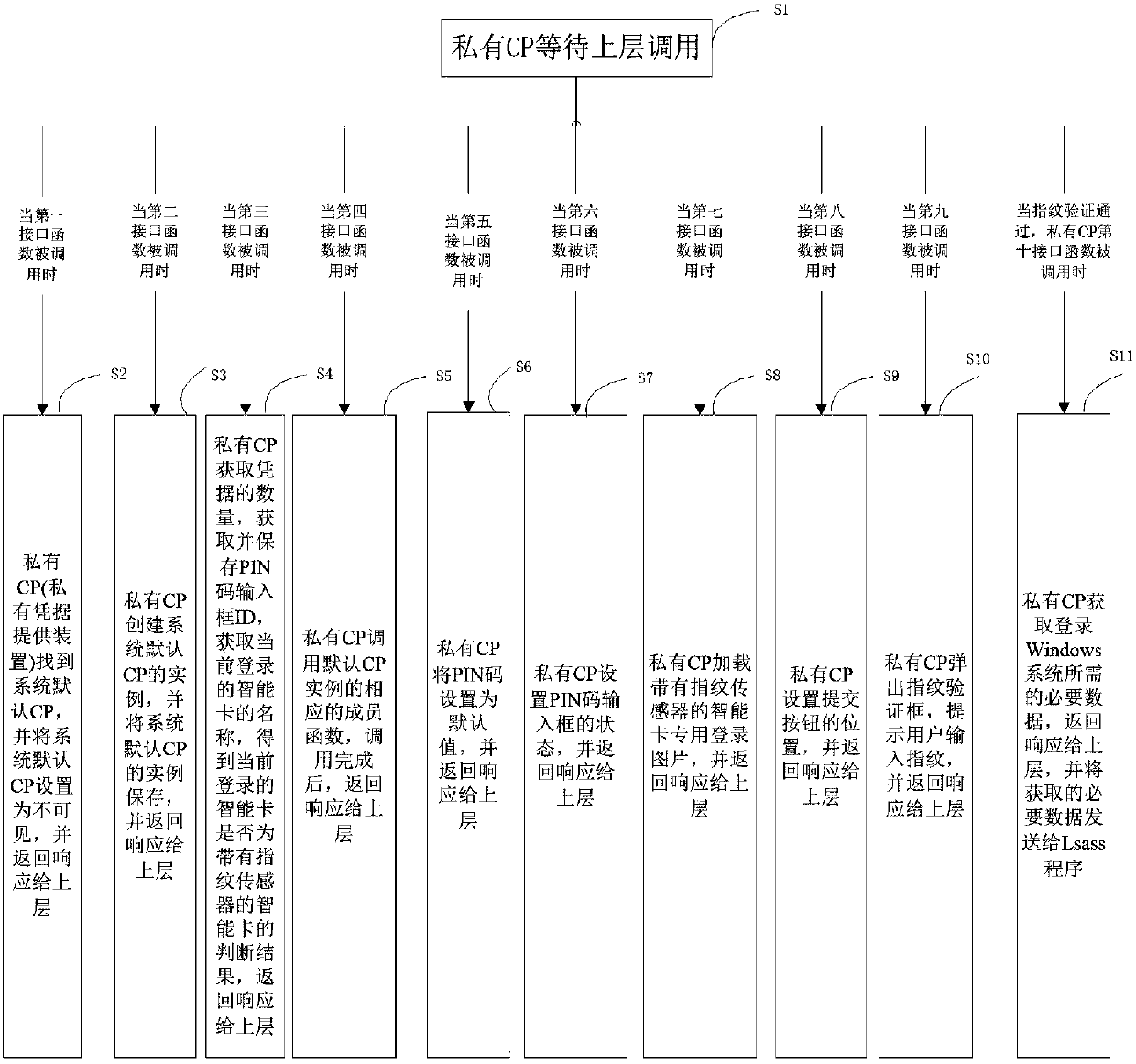
[0123] Example 2 of the present invention provides a method for logging into a Windows system with a smart card. Such as figure 2 As shown, the specific process is as follows:
[0124] Step S1, the private credential providing device (private CP for short) waits for the upper layer to call;
[0125] When the first interface function of the private CP is called, execute step S2; when the second interface function of the private CP is called, execute step S3; when the third interface function of the private CP is called, execute step S4; When the fourth interface function of the CP is called, execute step S5; when the fifth interface function of the private CP is called, execute step S6; when the sixth interface function of the private CP is called, execute step S7; When the seventh interface function is called, execute step S8; when the eighth interface function of the private CP is called, execute step S9; when the ninth interface function of the private CP is called, execu...
Embodiment 3
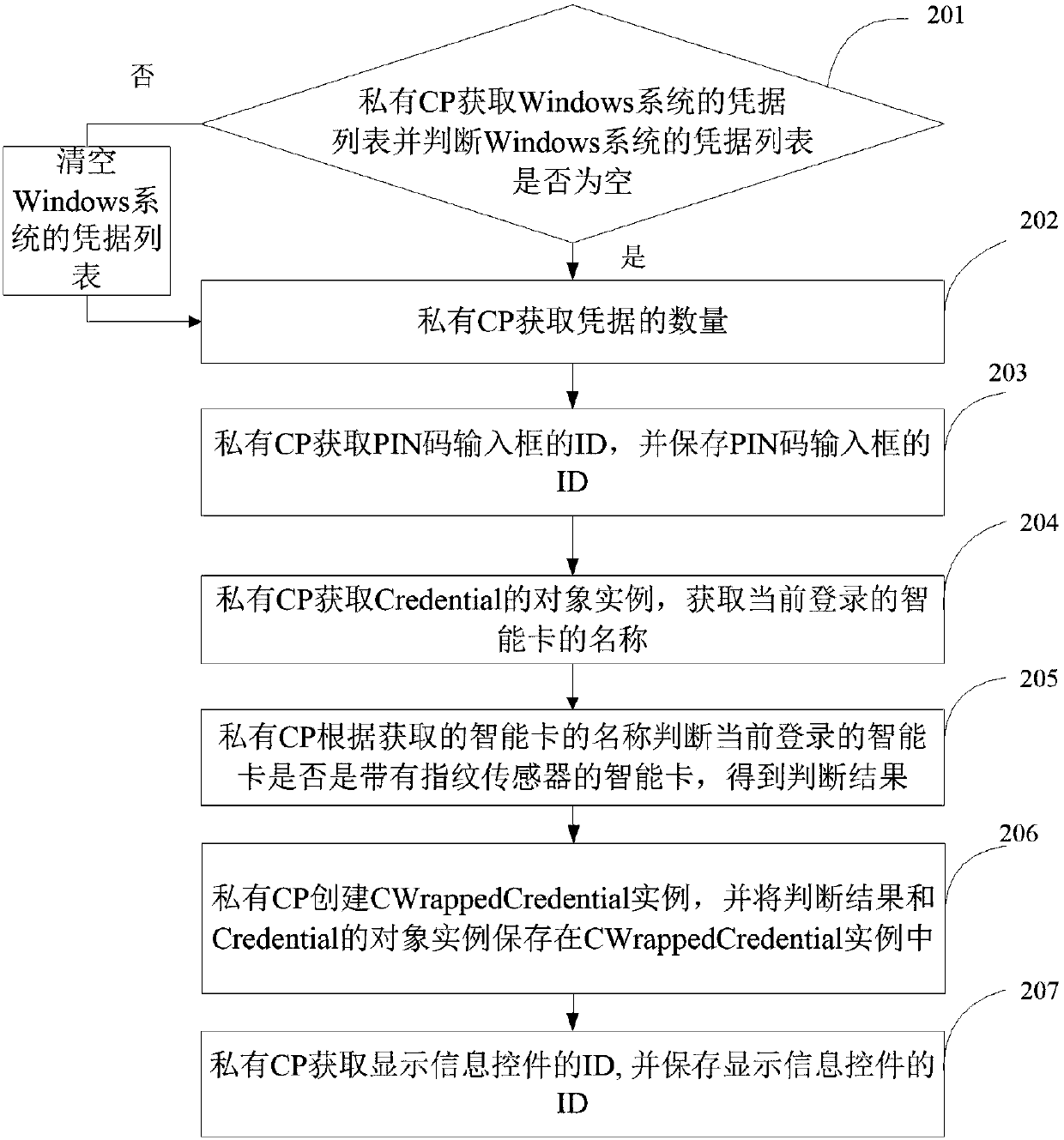
[0229] Embodiment 3 of the present invention provides a device for providing private credentials, such as Figure 6 As shown, the device for providing private credentials includes: a first operating module 301, a third operating module 303, a fifth operating module 305, a ninth operating module 309, and a tenth operating module 310, wherein,
[0230] The first operation module 301 is used to find the default credential providing device of the system from all credential providing devices when the first interface function is called by the upper layer, set the system default credential providing device to be invisible, and return a response to the upper layer;
[0231] The third operation module 303 is used for obtaining the quantity of credentials when the third interface function is called by the upper layer, obtaining and saving the personal identification code input box identification, obtaining the name of the smart card currently logged in and returning a response to the upp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com