Method for performing camouflage and camouflage removal on characters based on unrepeated keys
A key pair and character technology, applied in the field of information security, can solve problems such as complex algorithms, easy to be deciphered, and inability to distinguish whether data is camouflaged data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further elaborated below in conjunction with the accompanying drawings and embodiments.
[0054] Because the characters contained in "Thousand Characters" are different, in this embodiment, the characters contained in "Thousand Characters" are selected as the key characters.
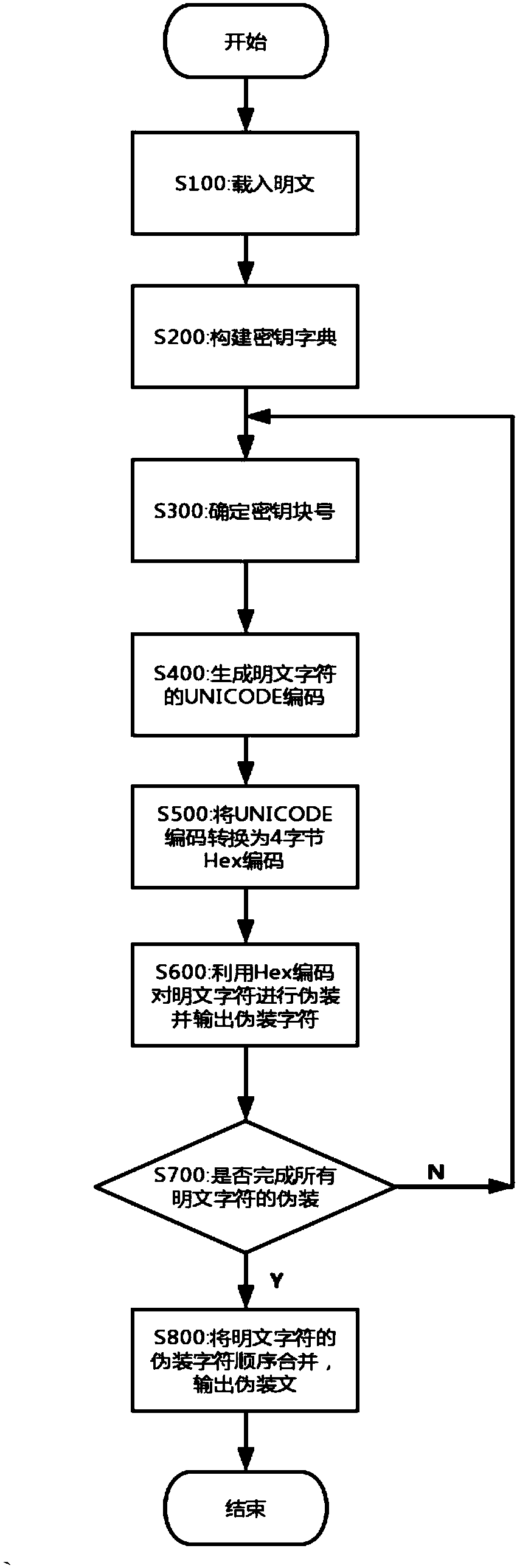
[0055] Such as figure 1 As shown, a method for disguising characters based on non-repeating keys comprises the following steps:
[0056] S100: Load plaintext: input the plaintext that needs to be camouflaged;
[0057] S200: building a key dictionary, comprising the following steps:
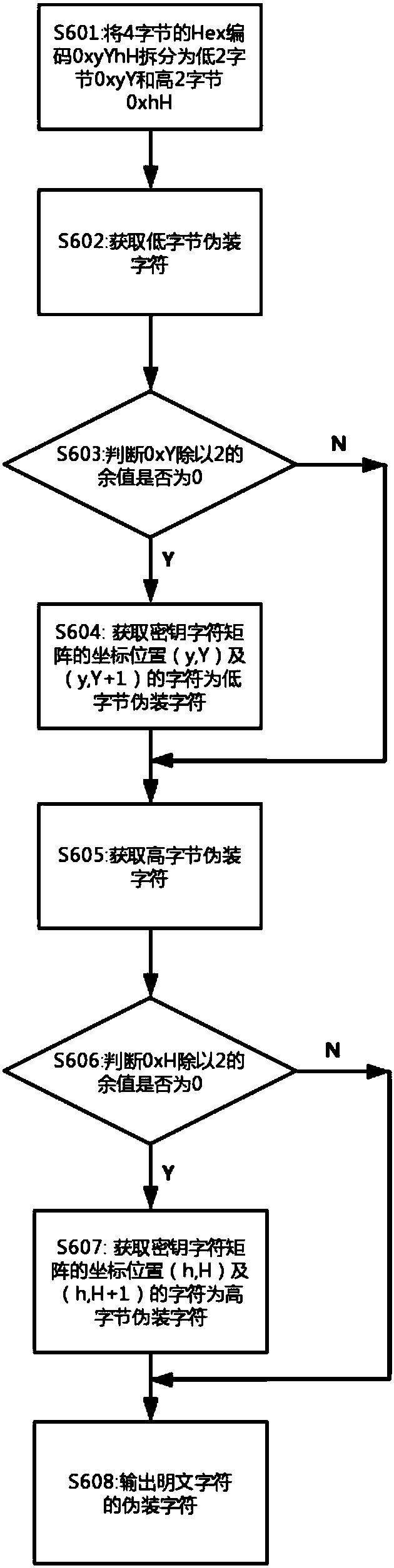
[0058] S201: The key character is formed into a key character matrix of 16*16 with 16 characters as a row and 16 characters as a column: as figure 2 As shown, the characters contained in "Thousand Characters" are selected as the key characters. Since the number of characters in "Thousand Characters" is 1000, it is divided into blocks according to each 16*16 key character matrix, and 24 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com