Identity authentication method and device and computer readable storage medium
An identity verification method and an identity verification technology are applied in the fields of computer-readable storage media, identity verification methods and devices, and can solve the problems of forging certificates, inconvenience to carry and store, and improving the difficulty of authentic and false identification of jewelry.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
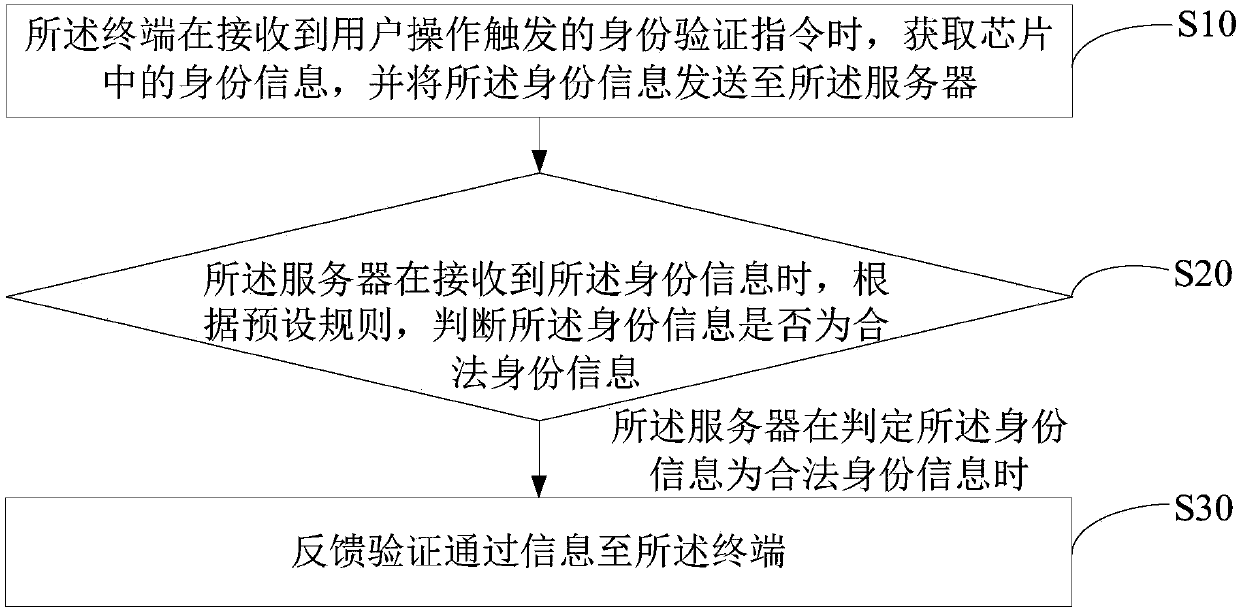
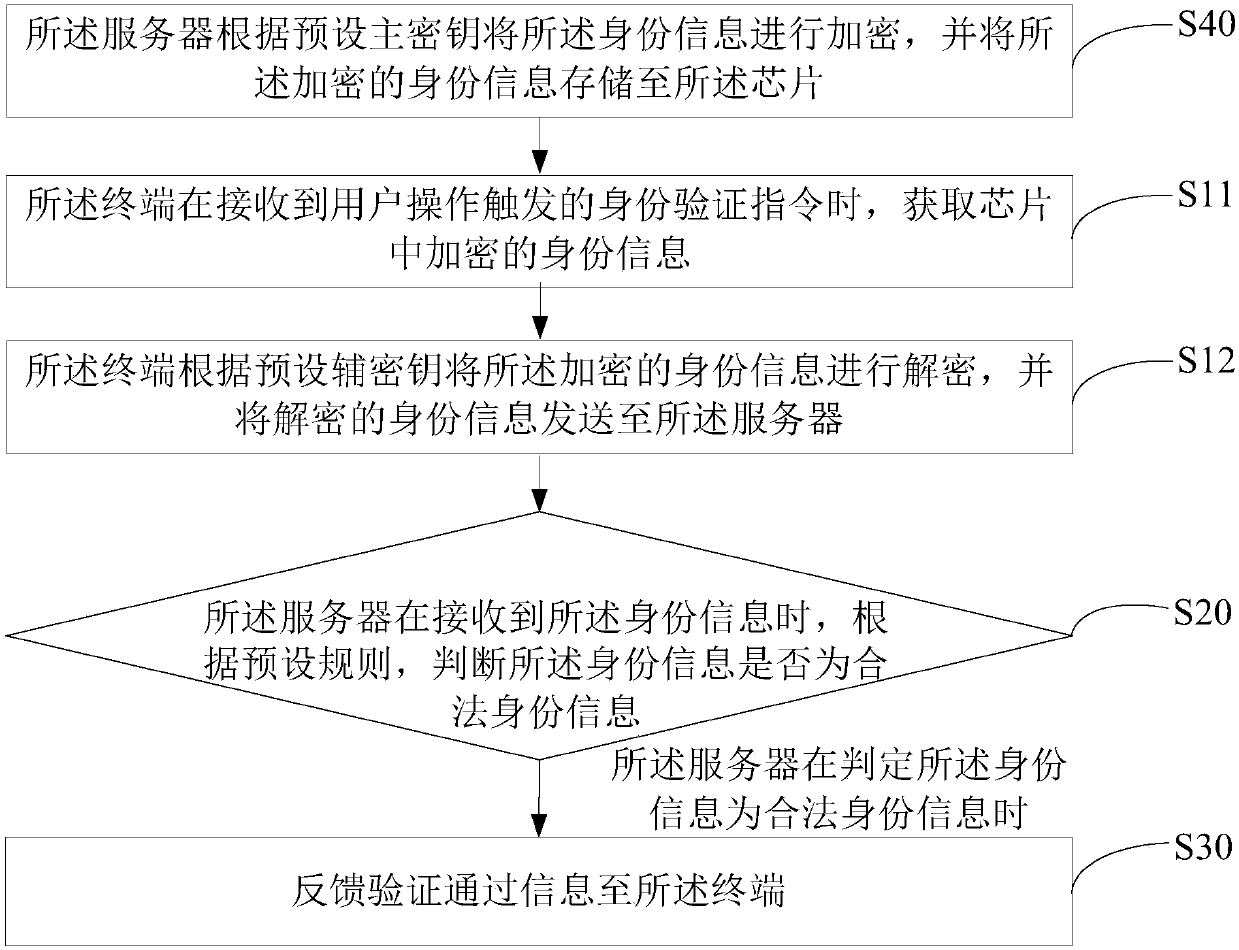
[0036] The main idea of the solution of the embodiment of the present invention is: the identity verification method obtains the identity information in the chip through the terminal when receiving the identity verification instruction triggered by the user operation, and sends the identity information to the server; When the server receives the identity information, it judges whether the identity information is legitimate identity information according to preset rules; At the end, the present invention realizes the purpose of identifying the authenticity of jewelry online, thereby simplifying the jewelry identification process and reducing the difficulty of jewelry identification.
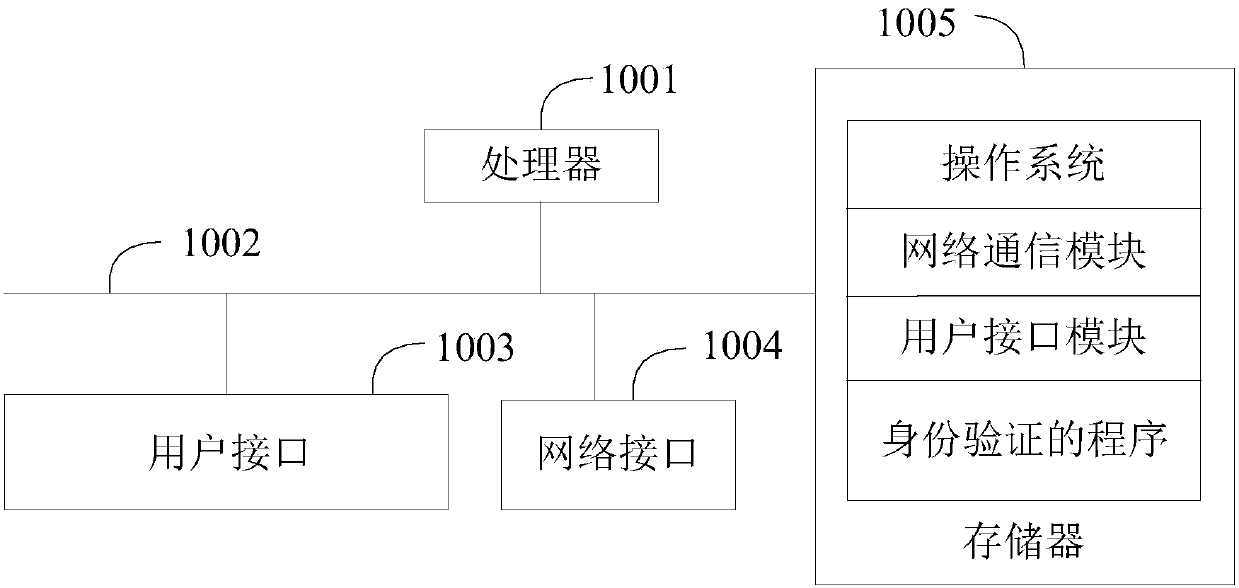
[0037] refer to figure 1 , figure 1 It is a schematic diagram of the operating terminal structure of the hardware operating environm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com