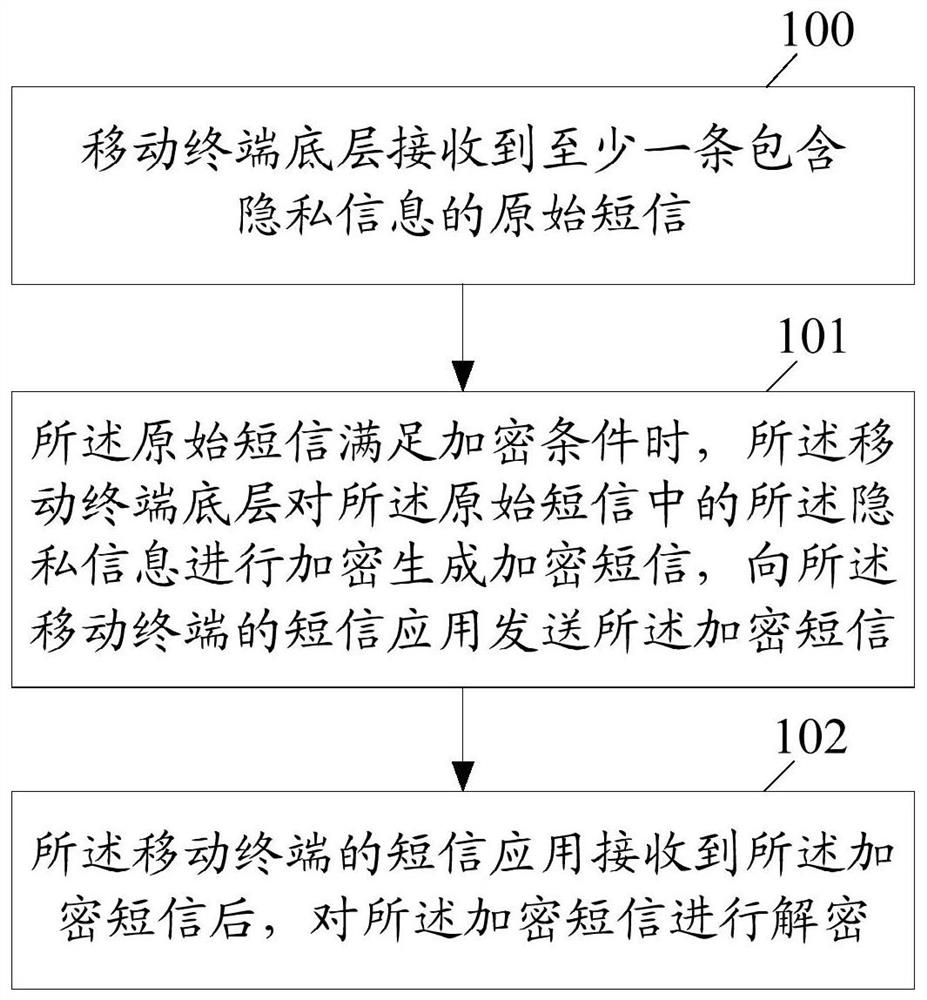
A method and device for encrypting and decrypting information in short messages
A technology for encryption, decryption and SMS, applied in the field of communication, can solve problems such as lack of practicability, and achieve the effect of reducing leakage risk, improving user experience, and ensuring user information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
[0056] In order to better reflect the purpose of the present invention, on the basis of the first embodiment of the present invention, the mobile terminal takes a mobile phone as an example, and the encryption and decryption of digital information in the mobile phone are further described.
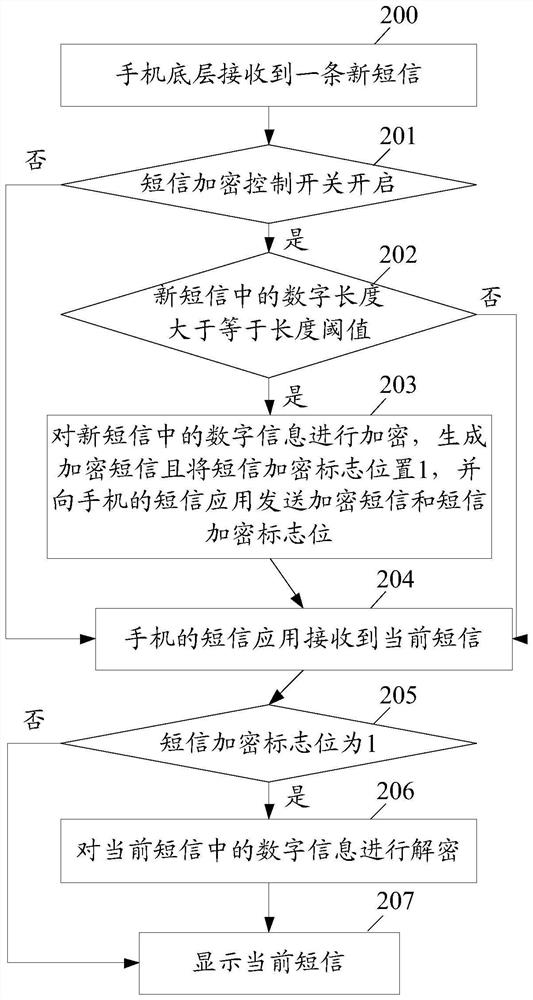
[0057] figure 2 It is a flow chart of the second embodiment of the method for encrypting and decrypting information in a short message according to the present invention, and the method includes:
[0058] Step 200: The bottom layer of the mobile phone receives a new text message.
[0059] Step 201: Determine whether the SMS encryption control switch is turned on, if yes, execute step 202; if not, skip to step 204.
[0060] Here, if the SMS encryption control switch is not turned on, the bottom layer of the mobile phone directly sends the received new SMS to the SMS application of the mobile phone.
[0061] Step 202: Determine whether the length of the number in the new short message is ...
no. 3 example
[0081] In order to better reflect the purpose of the present invention, on the basis of the first embodiment of the present invention, the encryption and decryption of the personal mailbox in the mobile phone short message will be further described.
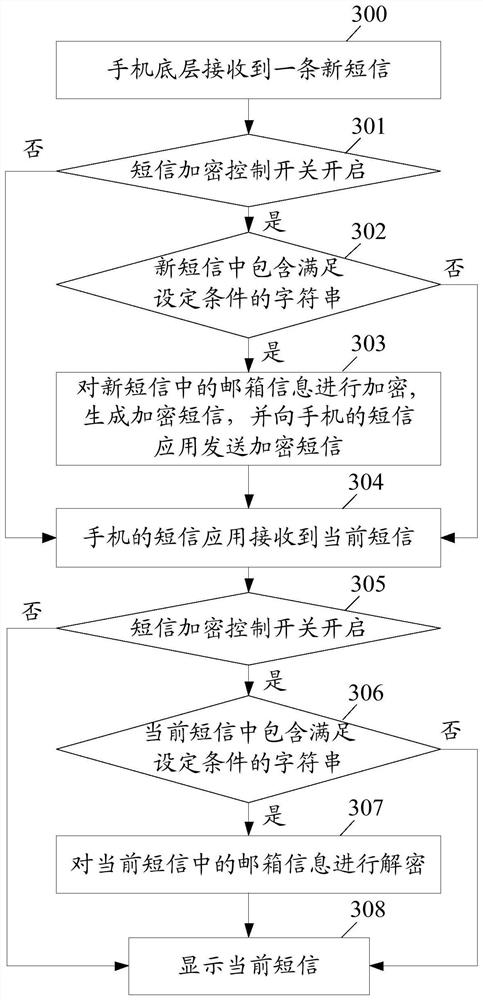
[0082] image 3 It is a flow chart of the third embodiment of the method for encrypting and decrypting information in a short message according to the present invention, and the method includes:
[0083] Step 300: The bottom layer of the mobile phone receives a new text message.
[0084] Step 301: Determine whether the SMS encryption control switch is turned on, if yes, execute step 302; if not, skip to step 304.
[0085] Step 302: Judging whether the new text message contains a character string satisfying the set condition, if yes, execute step 303; if not, skip to step 304.
[0086]In the embodiment of the present invention, the commonly used email address is composed of three parts, the first part is the user account number;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com