Safety verification method and device
A security verification and verification code technology, applied in the field of security verification methods and devices, can solve the problems of low verification security and the like
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
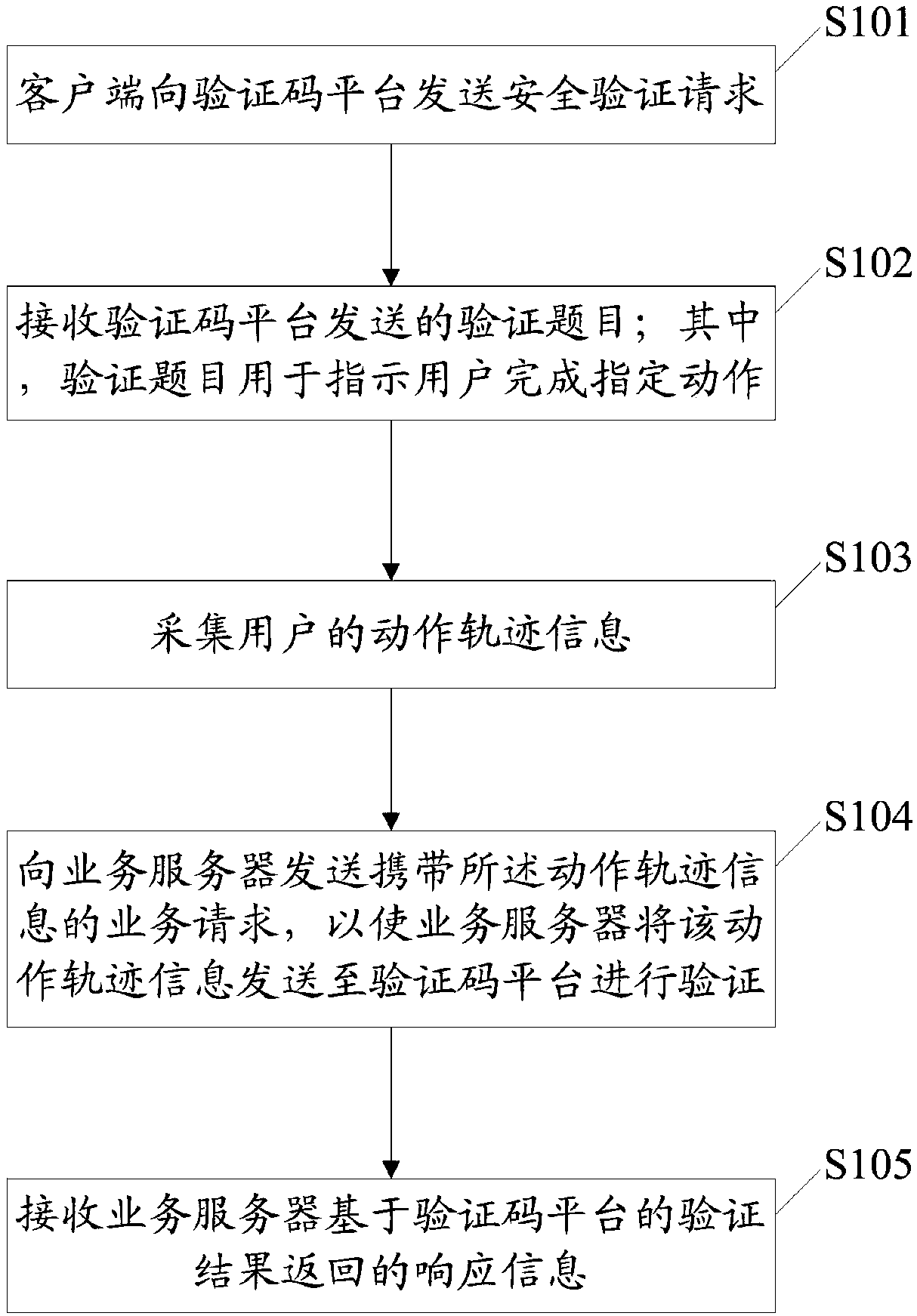
[0089] like figure 1 As shown, the flow chart of the security verification method provided by the embodiment of the present application includes the following steps:
[0090] S101: The client sends a security verification request to the verification code platform.
[0091] In practical applications, users mostly use various services provided by merchants through service clients (referred to as clients in the embodiments of this application), and some of the various services provided by merchants require security verification, so , security verification is usually accompanied by the user's business request. Therefore, in the specific implementation process, when the business used by the user requires security verification, the client can first cache the acquired business information locally, and then send it to the verification code platform. Secure authentication request.
[0092] S102: Receive the verification question sent by the verification code platform; wherein, the ve...
Embodiment 2
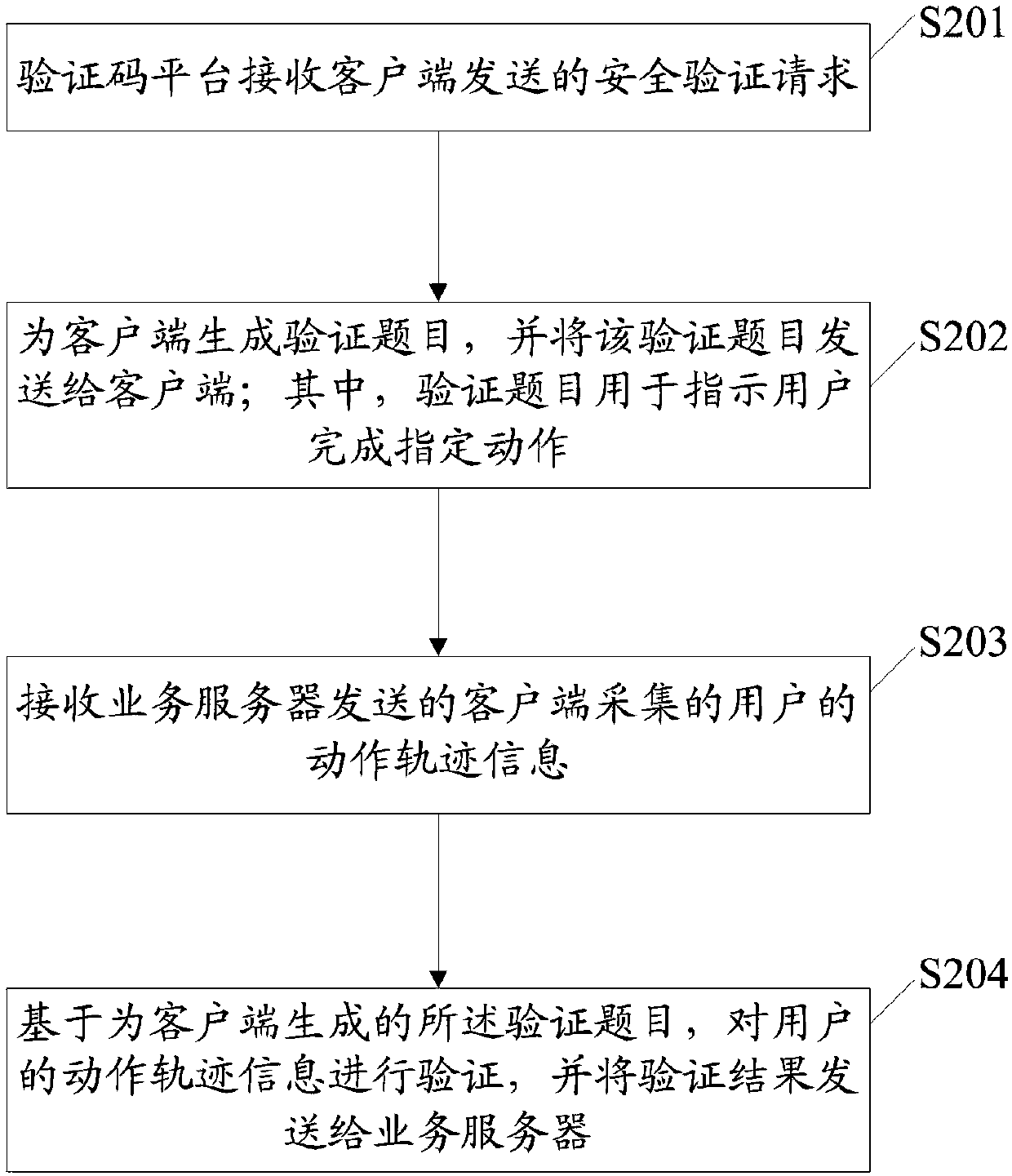
[0103] like figure 2 As shown, the flowchart of another security verification method provided in the embodiment of the present application includes the following steps:
[0104] S201: The verification code platform receives the security verification request sent by the client.
[0105] Here, when the service requested by the user needs to be verified, the client can directly send a security verification request to the verification code platform, that is, the security verification request initiated by the client does not need to be forwarded by the service server.
[0106] S202: Generate a verification topic for the client, and send the verification topic to the client; wherein the verification topic is used to instruct the user to complete a specified action.
[0107] In the specific implementation process, the verification code platform can store a variety of specified actions in advance, and when a verification topic needs to be generated for the client, a specified action...
Embodiment 3
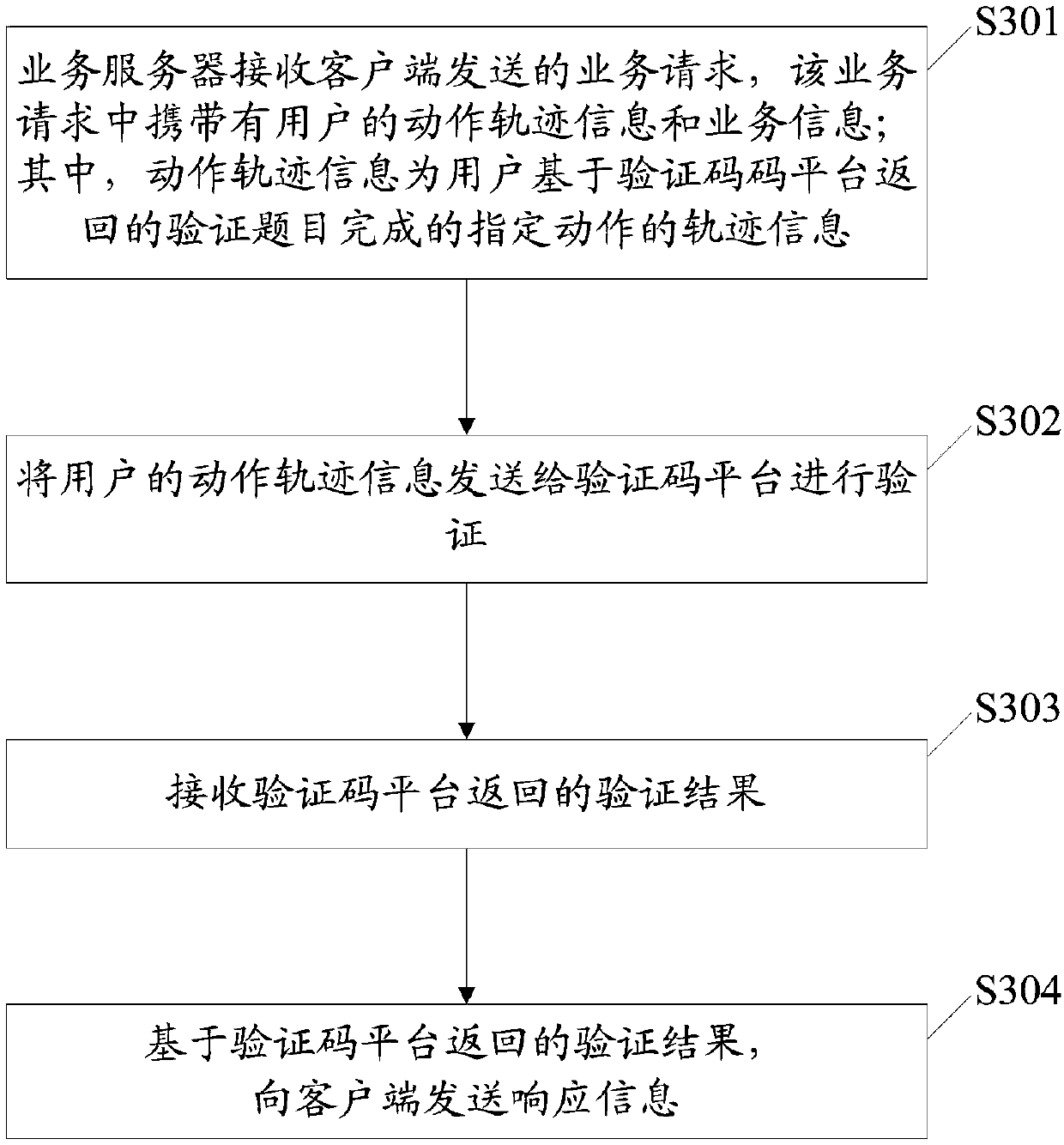
[0116] like image 3 As shown, the flow chart of another security verification method provided by the embodiment of the present application includes the following steps:
[0117] S301: The service server receives a service request sent by a client, and the service request carries the user's action track information and service information; wherein the action track information is the track information of the specified action completed by the user based on the verification question returned by the verification code platform.
[0118]S302: Send the user's action track information to the verification code platform for verification.
[0119] S303: Receive the verification result returned by the verification code platform.
[0120] S304: Send response information to the client based on the verification result returned by the verification code platform.
[0121] In the specific implementation process, if the verification result is that the verification is successful, the service se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com