Image tampering detection method based on comprehensive features of triangular mesh
A triangular mesh and comprehensive feature technology, applied in the field of passive forensics of digital images, can solve problems such as unsatisfactory performance, and achieve the effects of fast processing speed, good robustness, and accelerated detection speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
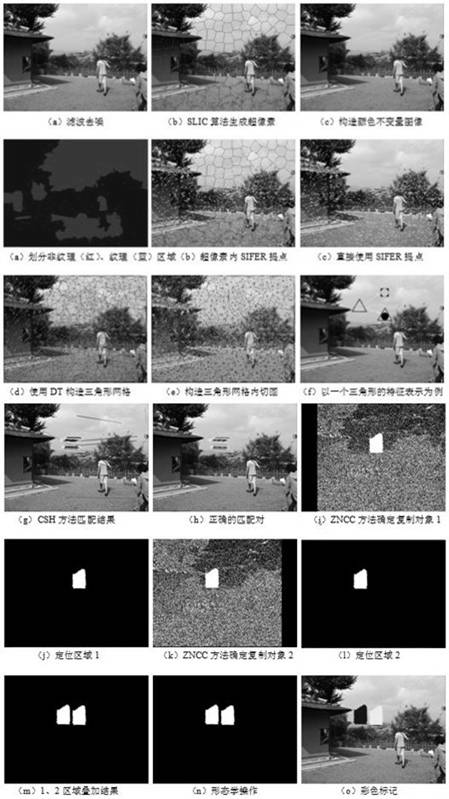
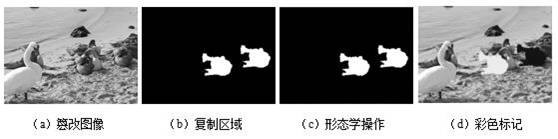
[0062] The method of the present invention is as Figure 7 There are six stages shown: superpixel generation, image feature point extraction, triangular mesh construction, triangular mesh feature construction, triangular mesh feature matching, and post-processing.
[0063] Convention: I refers to the image to be detected; I1 is the image after denoising; S u (u=1,2,...,l) represents a superpixel block; is pixel i at S u Probability in ; E u is S u entropy; I2 is the constructed color invariant image; C u Indicates partition coding, coded values 0 and 1 correspond to non-texture and texture regions respectively; T k (k=1,2,...,n) is the kth triangle, and n is the number of triangles; I k refers to T k inscribed circle of ; o k 、r k Yes k The center and radius of the circle; A k for I k The outer extension square; Q k means T k except I k the rest of the Respectively represent Q k The gradient entropy H under the three channels of R, G, and B k ; Refers t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com