Method and system for protecting data object subject identification based on cryptographic operations
A data object, cryptography technology, used in digital transmission systems, transmission systems, key distribution, and can solve problems such as identification matching
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0051] Said generating the anonymous encoding of the data object subject identification includes the following steps:
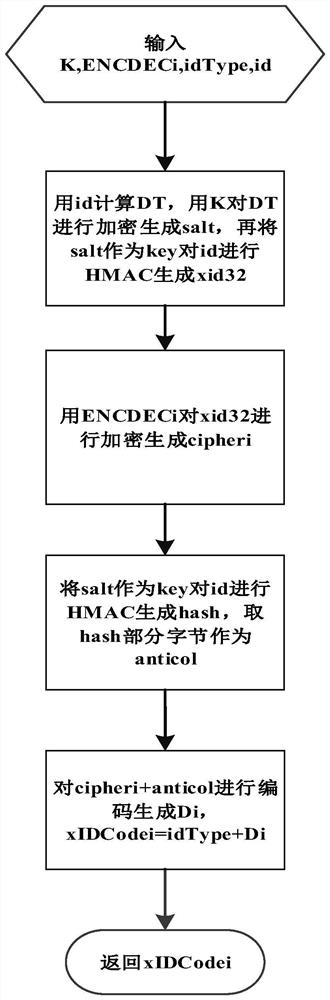
[0052] (A1) The key management server generates a key K and generates an encryption and decryption key ENCDECn of a symmetric cryptographic algorithm for each data owner, where n is any positive integer;
[0053] (A2) using the key K to generate an anonymous identifier for the data object subject identifier after processing the data subject identifier;
[0054] (A3) Using the ENCDECi key, the i-th data owner encrypts the anonymous identifier identified by the data object subject to generate an anonymous ciphertext Ci of the data object subject identifier, where i≤n;
[0055] (A4) Encoding the Ci to generate an anonymous code Xi for the subject identifier of the data object;
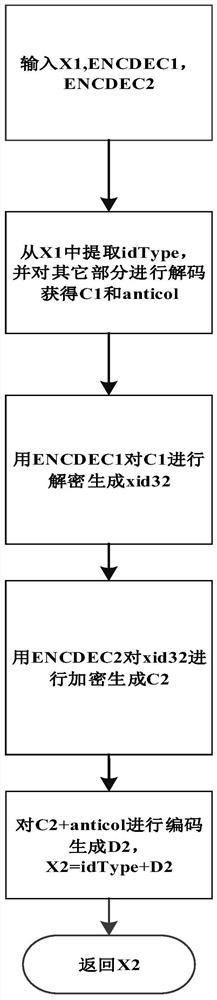
[0056] The anonymous encoding of the converted data object subject identifier includes the following steps:
[0057] (B1) The key management server generates a key K and generates an e...
Embodiment approach 2
[0105] Said generating the anonymous encoding of the data object subject identification includes the following steps:
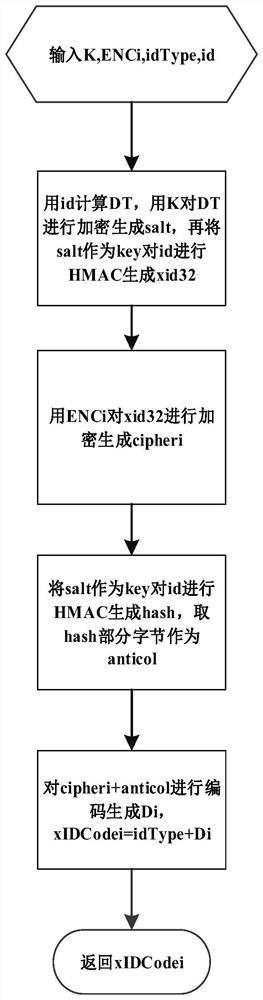
[0106] (A1) The key management server generates a key K and generates an encryption key ENCn for each data owner, where n is any positive integer;
[0107] (A2) using the key K to generate an anonymous identifier for the data object subject identifier after processing the data subject identifier;
[0108] (A3) Using the ENCi key, the data owner i encrypts the anonymous identifier identified by the data object subject to generate the anonymous ciphertext Ci of the data object subject identifier, where i is any positive integer and i≤n;
[0109] (A4) Encoding the Ci to generate an anonymous code Xi for the subject identifier of the data object;
[0110] The anonymous encoding of the converted data object subject identifier includes the following steps:
[0111] (B1) The key management server generates a key K and generates a key pair of asymmetric cryptographic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com