A Password-based Anonymous Entity Authentication Method
A password and entity technology, which is applied in the field of computer technology and information security, can solve problems such as insufficient efficiency, and achieve the effect of effective efficiency and protection of identity privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
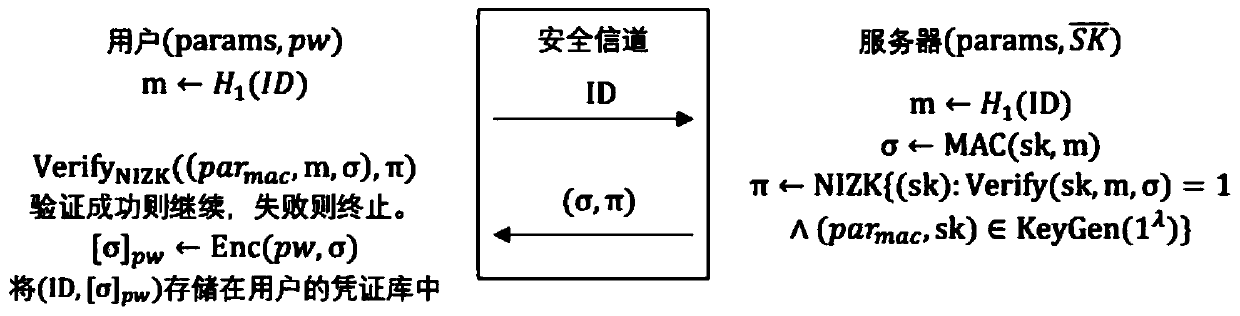
[0041] Embodiment 1. General construction of a password-based anonymous authenticated key exchange protocol
[0042]Based on the above components, this embodiment aims to give the general structure of the password-based anonymous authenticated key exchange protocol of the present invention. This construction requires that the space of the algebraic message authentication code is consistent with the plaintext space of the password encryption scheme.
[0043] 1. System establishment stage
[0044] Given a security parameter λ, the server generates system parameters and publishes them, and at the same time generates corresponding private keys and stores them secretly. The specific execution steps are as follows:
[0045] 1) Select domain parameters in is a cyclic group of order p, where p is a prime number with at least 2λ bits, and g is the group A generator of .
[0046] 2) Select two independent cryptographic hash functions and H 2 : {0, 1}* → {0, 1} k ,in is th...
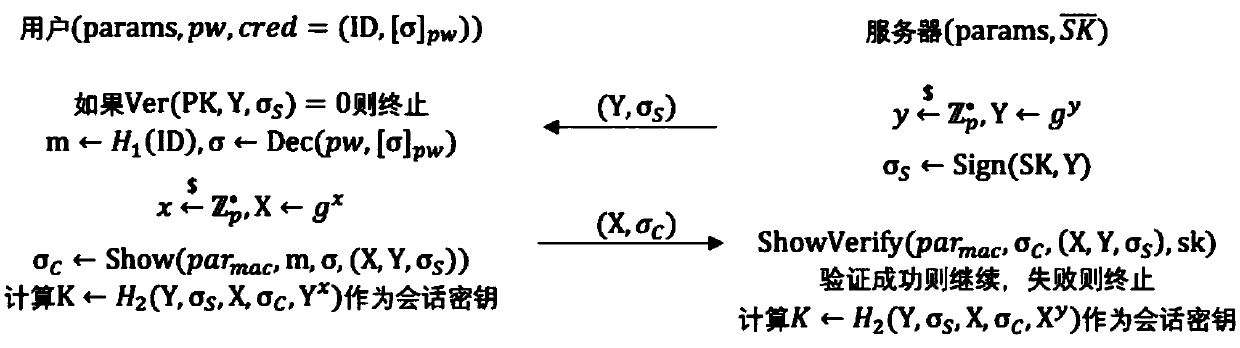
Embodiment 2
[0075] Embodiment 2: An example of an efficient password-based anonymous authenticated key exchange method
[0076] This embodiment aims at constructing an efficient instance of an anonymous password-based authentication key exchange method based on a specific algebraic message authentication code scheme, and is a specific instantiation of the general construction described in embodiment 1).
[0077] This embodiment uses an algebraic message authentication code scheme based on q-SDH assumption, denoted as MAC SDH . MAC is given below SDH The specific description of each algorithm and the construction of the corresponding zero-knowledge proof and certificate description proof algorithm:
[0078] 1)keyGen(1) λ ): Input the security parameter λ, select the domain parameter in is a cyclic group of order p, where p is a prime number with at least 2λ bits, and g is the group A generator of . Then, in Randomly select an element γ in the group, and calculate ω←g γ . Fina...
Embodiment 3
[0117] Embodiment 3: Application of the above-mentioned anonymous authentication method in the TLS protocol
[0118] This embodiment aims to provide a method of applying the above-mentioned authentication method under the TLS protocol, which is an example of the application of the instantiation method in embodiment 2 in real life, and the specific application method is as follows:
[0119] Before the TLS connection is established, the user and the server complete the system establishment phase and user registration phase described in Embodiment 2. In the user registration stage, the server also needs to issue an additional digital certificate cert mac . This certificate is issued by the server, and its owner is a virtual entity apake; the certificate includes an elliptic curve parameter and the public key ω, the MAC SDH The public parameters of the scheme; the type of the certificate is apake; the public key signature algorithm is (SigMAC, SHA256), where SigMAC=(Show, Show...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com